Eliminating SQL Injection Vulnerabilities in Software

SQL Injection Strategies: Practical techniques to secure old vulnerabilities against modern attacks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Mar 26 2024
Eliminating SQL Injection Vulnerabilities in Software

SQL Injection Strategies: Practical techniques to secure old vulnerabilities against modern attacks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Mar 22 2024
Are you interested in cybersecurity?
Interested in discovering how Python can bolster your abilities in safeguarding digital assets? Delve into the potential of Python for cybersecurity.
In the current digital era, cybersecurity holds greater significance than ever before. Python, renowned for its versatility and resilience, has emerged as a fundamental tool for cybersecurity professionals globally.
🔹 How Python can streamline threat detection and analysis.
🔹 Practical examples of Python scripts for automating security tasks.
🔹 Resources and tools to kickstart your journey into Python for cybersecurity.
Regardless of whether you’re an experienced cybersecurity professional or new to the field, Python has the potential to transform your approach to security challenges.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Mar 21 2024
Mar 10 2024
There’s more to cyber security than just ISO 27001. Protect your business with the full family of ISO standards.
Protect your organisation from cyber crime with ISO 27001 Training – Instructor-led live online, self-paced online and classroom.
Equip your staff to identify and address cyber security and privacy risks.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 28 2024
France’s National Cybersecurity Agency (ANSSI) observed a significant rise in cyber espionage campaigns targeting strategic organizations in 2023.
These operations are increasingly focused on individuals and non-governmental structures that create, host or transmit sensitive data, ANSSI observed in its 2023 Cyber Threat Landscape report, published on February 27, 2024.
Besides public administration, the primary targets of cyber espionage activity included organizations associated with the French government, such as technology and defense contractors, research institutes and think tanks.
Overall, cyber espionage remained the top cyber threat ANSSI’s teams dealt with in 2023.
ANSSI has also noted an increase in attacks against business and personal mobile phones aimed at targeted individuals.
There has also been an upsurge in attacks that have used methods publicly associated with the Russian government.
“These attacks are not limited to mainland French territory: in 2023, ANSSI dealt with the compromise of an IT network located in a French overseas territory using an attack modus operandi publicly associated with China,” reads the report.
Meanwhile, financially motivated attacks were also on the rise, with an observed 30% increase in ransomware attacks compared to 2022.
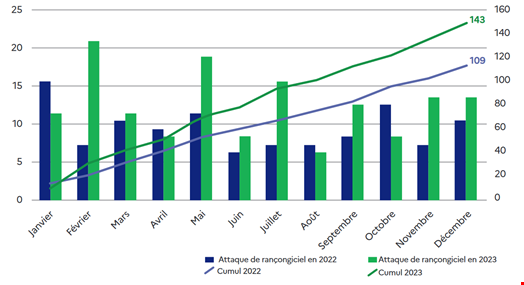
Small and medium enterprises (SMEs) and mid-sized businesses were the most targeted organizations, representing 34% of all cyber-attacks observed by ANSSI in 2023. Local administration came second, suffering 24% of all attacks in 2023.
In total in 2023, ANSSI recorded 3703 cyber events, 1112 of which were labeled as cyber incidents. In 2022, it recorded 3018 cyber events, including 832 cyber incidents.
The latest version of the LockBit ransomware, LockBit 3.0 (aka LockBit Black), was the most used malware in financially motivated cyber-attacks in 2023, taking over previous ransomware versions from the same threat group that dominated the ransomware landscape in 2022.
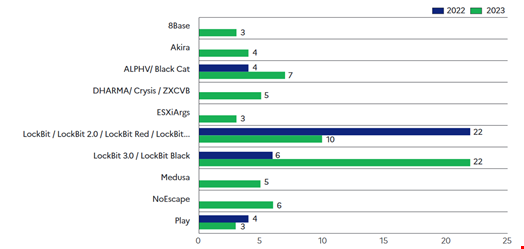
Read more: LockBit Takedown – What You Need to Know about Operation Cronos
Overall, 2023 has seen significant changes in the structure and methods of attackers. They are perfecting their techniques in order to avoid being detected, tracked, or even identified.
“Despite efforts to improve security in certain sectors, attackers continue to exploit the same technical weaknesses to gain access to networks. Exploiting ‘zero-day’ vulnerabilities remains a prime entry point for attackers, who all too often still take advantage of poor administration practices, delays in applying patches and the absence of encryption mechanisms,” reads the report, translated from French to English by Infosecurity.
The top five vulnerabilities exploited by threat actors to compromise French organizations’ IT systems in 2023 include flaws in VMWare, Cisco, Citrix, Atlassian and Progress Software products.
These include the Citrix Bleed and the MOVEit vulnerabilities.
Read more: MOVEit Exploitation Fallout Drives Record Ransomware Attacks
Finally, in a tense geopolitical context, ANSSI noted new destabilization operations aimed mainly at promoting a political discourse, hindering access to online content or damaging an organization’s image.
“While distributed denial of service (DDoS) attacks by pro-Russian hacktivists, often with limited impact, were the most common, pre-positioning activities targeting several critical infrastructures in Europe, North America and Asia were also detected.
“These more discreet activities may nevertheless be aimed at larger-scale operations carried out by state actors waiting for the right moment to act,” the report explained.
Vincent Strubel, ANSSI’s director general, commented: “While financially motivated attacks and destabilization operations saw a clear upturn in 2023, it was once again the less noisy threat, which remains the most worrying, that of strategic and industrial espionage and pre-positioning for sabotage purposes, which mobilised the ANSSI teams the most.”
These geopolitically driven threats will particularly be on ANSSI’s radar in 2024, as Paris is prepares to host the 2024 Olympic and Paralympic Games.
An Investigator’s Guide to Espionage, Ransomware, and Organized Cybercrime
Feb 13 2024
An ongoing campaign of cloud account takeover has affected hundreds of user accounts, including those of senior executives, and impacted dozens of Microsoft Azure environments.
Threat actors attack users with customized phishing lures inside shared documents as part of this ongoing effort.
Some documents that have been weaponized have embedded links to “View document,” which, when clicked, take users to a malicious phishing webpage to steal sensitive information and commit financial fraud.
Threat actors appear to target a broad spectrum of people with varying titles from various organizations, affecting hundreds of users worldwide.
“The affected user base encompasses a wide spectrum of positions, with frequent targets including Sales Directors, Account Managers, and Finance Managers,” Proofpoint researchers shared with Cyber Security News.
“Individuals holding executive positions such as “Vice President, Operations,” “Chief Financial Officer & Treasurer” and “President & CEO” were also among those targeted.”
Threat actors have a realistic approach, as seen by the variety of positions they have targeted, intending to compromise accounts that have varying degrees of access to important resources and responsibilities across organizational activities.
In this campaign, researchers observed the usage of a particular Linux user agent that attackers employed during the attack chain’s access phase.
Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
The ‘OfficeHome’ sign-in application is primarily accessed by attackers using this user-agent, along with other native Microsoft365 apps, like:
Attackers use their own MFA techniques to keep accessing systems permanently. Attackers choose various authentication techniques, such as registering additional phone numbers to authenticate via SMS or phone calls.
Criminals get access to and download confidential data such as user credentials, internal security protocols, and financial assets.
Mailbox access is also used to target individual user accounts with phishing threats and migrate laterally across compromised organizations.
Internal emails are sent to the impacted companies’ finance and human resources departments to commit financial fraud.
Attackers design specialized obfuscation rules to hide their activities and erase any proof of malicious activity from the inboxes of their victims.
“Attackers were observed employing proxy services to align the apparent geographical origin of unauthorized activities with that of targeted victims, evading geo-fencing policies,” researchers said.
Thus, in your cloud environment, be aware of account takeover (ATO) and possible illegal access to key resources. Security solutions must offer precise and prompt identification of both initial account compromise and post-compromise actions, together with insight into services and applications that have been misused.
A Leader’s Guide to Cybersecurity: Why Boards Need to Lead–and How to Do It
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 09 2024
In this Help Net Security interview, Robin Long, founder of Kiowa Security, shares insights on how best to approach the implementation of the ISO/IEC 27001 information security standard.
Long advises organizations to establish a detailed project roadmap and to book certification audits at an early stage. He also recommends selecting an internal team that includes a leader with the ISO 27001 Lead Implementer qualification and suggests that in some cases, the best approach to the standard may be to start by prioritizing a limited number of “security wins” before embarking on full implementation.
A few general points about ISO 27001, before getting onto the questions:
1. The documentation behind ISO/IEC 27001:2022 (“ISO 27001”) is broken into two main parts: ISO/IEC 27001 itself, which contains the primary guidance, and a ‘guidance document’ called ISO/IEC 27002, which lists suggested information security controls that may be determined and implemented based on the risk analysis that is carried out according to the requirements of the primary document.
ISO 27001 is also supported by the other standards ISO/IEC 27000:2018 (IT security techniques) and ISO/IEC 27005:2022 (Information security, cybersecurity, and privacy protection), among others.
All these are developed and maintained by the International Organization for Standardization (ISO), which is based in Geneva, Switzerland.
2. Although there are a number of things that you are obliged to do if you’re seeking certified conformity to the standard, it is actually quite flexible about the details. Even the “requirements” – the obligatory clauses in the 27001 document – generally allow a fairly broad range of interpretation. This makes sense when you think that ISO 27001 has been developed as a one-size-fits-all system for all types and sizes of organization that handle sensitive information.
When you look at it like that, it immediately becomes less intimidating.
3. If you decide to go ahead and implement ISO 27001, it’s highly recommended to put together a detailed road map that defines targets of what should be achieved by what date in the timeline of the project (Gantt charts are good for this – look them up!). This helps to keep the project under control and reduces the risk of time and budget overrun. Breaking the project up into weekly components also makes it less daunting.
4. You’ll also need to define a (small) group of people to carry out, maintain and be accountable for implementation of the standard. You might call this the ‘ISMS Team’ (where ISMS means Information Security Management System, another way to describe ISO 27001). This team should ideally incorporate expertise and experience in IT, business development and data protection, and have a channel to senior management.
As a consultant myself, I’m aware of the conflict of interest, but I have to say that I do think it makes sense to hire external advice for assistance with implementation of ISO 27001, for internal audit, and interaction with certification auditors.
One of the main responsibilities of such an advisor is to assist with understanding of the standard and information security management generally, at both high and low levels. The range of ISO27002 controls – for example – is wide indeed, but a competent consultant will break them down into manageable portions that are taken on one by one, in a carefully planned order.
Whether or not you decide to hire a consultant, it’s a pretty good idea also to send the leader of the ISMS Team on an ISO2 7001 Lead Implementer (LI) course. These courses typically run for about three days, and they are helpful. Note that ISO 27001 requires the organisation to provide evidence of the competence of key participants in the project, and the LI qualification for a team member indicates a reasonable degree of knowledge and commitment regarding the standard.
Of course, there are also a number of helpful online resources including the ISO27k Forum.
It’s true that implementation of ISO 27001 necessarily consumes resources, in terms of money and other assets – particularly people’s time. The critical question is whether the resource cost is offset by perceived gains, and this is largely about efficiency of allocation. Among other methods that we can use to attempt to optimise this are:
1. Use of a roadmap – as mentioned above – that takes the organisation all the way through to the two-stage certification audit process at a granular (weekly) level.
2. Early selection of the certification auditor and agreement of tentative dates for the certification audits. The benefits of doing this include the psychological one of getting an end date in the diary to help define the project roadmap. The cost of certification audits is also an important part of the overall budget, and the certification body will provide quotes for these at this stage.
Note that along with the two initial certification audits, there are a couple of (roughly annual) surveillance audits and a recertification audit after three years. These audits all cost money, of course, and require budgeting.
3. Watching out for some of the less obvious costs, including the potential charges associated with:
Consultancy companies love to answer this question – on their websites – with a list of bullet points.
However, I can tell you that in nearly all cases there is just a single key factor at play, and it is a commercial one: Potential important clients or partners have been identified that require certification to the standard. Organisations that operate in sensitive sectors (finance, critical infrastructure, healthcare…) have already learned this or are in the process of learning it, and don’t need to be told about it. If they don’t know, then by all means tell them!
Other reasons that I consider completely valid and credible include:
These are indeed arguably the core areas of ISO 27001. Among the critical things to remember regarding risk assessments are:
ISO 27001 fundamentally breaks down to: “What information security risks do we face? How should we best manage them?”
You definitely don’t have to apply all of the controls, and nearly all organisations treat some, validly, as non-applicable in their Statement of Applicability. For example, businesses where all employees work remotely simply don’t have the full range of risks that can benefit from mitigation by the physical controls.
When it comes to performance evaluation, it’s largely a case of working through the relevant clauses and controls and agreeing how good a job the organisation is doing trying to meet the associated requirements. The ones that are selected for monitoring, measurement and evaluation will depend on the type and size of the organisation and its business objectives. These are basically key performance indicators (KPIs) for information security and might include supplier evaluations and documented events, incidents, and vulnerabilities.
The switch towards remote working and use of cloud resources has been quite disruptive for ISO 27001. The 2022 version has been somewhat adapted (via modifications to the controls) to reflect the change in working conditions. However, it still gives a lot of attention to traditional physical places of work, networks, and pre-SaaS style suppliers.
The big switch away from locally downloaded software to cloud services means that we need to take advantage of the flexibility of ISO 27001 to interpret the 27002 controls in a corresponding way, for example:
This is an enigmatic section of clause 10 (Improvement) that organisations tend to struggle with (the second part is about dealing with non-conformities and is much clearer regarding what needs to be done).
It seems to me that the best approach is to raise the question of ‘how can we make the ISMS better?’ at the periodic ISMS management meetings, come up with some examples whereby this may be achieved and then provide any observed progress in the right direction. That means that by the time of the first follow-up (surveillance) audit you should be able to present a list of several potential improvements along with how they are being achieved.
I’d like to finish up by mentioning that nothing stops your organisation implementing ISO 27001 without getting the certification, or even doing a partial implementation. Many businesses like the concept of ISO 27001 but aren’t quite ready to commit fully. In that case, I highly recommend the following implementation model:
1. Decide which areas of information security are priorities for your organisation in terms of incremental increase in security, resources (money, time, personnel) required and ease of implementation. You can call these your ‘lowest-hanging security fruit’ if you must. Possible examples include access control, HR security or endpoint security.
2. Work through these one by one according to the relevant 27002 controls.
3. Once you have the highest priority areas covered off, start working on lower levels of priority.
4. After a few months of this, you may feel that ISO 27001 isn’t quite so formidable, and that you are ready to tackle it. Go for it!



InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Feb 06 2024
https://www.techtarget.com/whatis/feature/17-free-cybersecurity-tools-you-should-know-about
Cybersecurity products can get pricy but there are many excellent open source tools to help secure your systems and data. Here’s a list of some of the most popular with cyber pros.
Cybersecurity tools aren’t just for the enterprise anymore; they’re essential for every type and size of organization.
Some tools specialize in antivirus, while others focus on spear phishing, network security or scripting. Even the best cybersecurity products can only do a few things very well, and there is no room for error.
Effective products, coupled with in-depth cybersecurity planning, are a must for all. Whether businesses have an in-house security team or outsource these services, every entity needs cybersecurity pros to discover and fix any points of weakness in computer systems. This reality can tax the bottom line, but luckily there are many free cybersecurity tools available.
Here is a rundown of some of the top free tools cybersecurity professionals use every day to identify vulnerabilities.
Aircrack-ng is a must-have suite of wireless security tools that focus on different aspects of Wi-Fi security. Aircrack-ng focuses on monitoring, attack testing and cracking your Wi-Fi network. This package of tools can capture, analyze and export packet data, spoof access points or routers and crack complex Wi-Fi passwords. The Aircrack-ng suite of programs includes Airdecap-ng, which decrypts WEP or WPA-encrypted capture files; Airodump-ng, a packet sniffer; Airtun-ng, a virtual tunnel interface creator; and Packetforge-ng, which creates encrypted packets for injection. All of it is free and open source.
Burp is a suite of tools specifically focused on debugging and testing web app security. Burp Suite includes a spider for crawling web app content, a randomness tool for testing session tokens and a sophisticated request repeater to resend manipulated requests. The real power of Burp Suite, however, is the intercepting proxy tool, which enables Burp to intercept, inspect, modify and send traffic from the browser to a target. This powerful feature makes it possible to creatively analyze a web app’s attack vectors from all angles — a key reason it’s often ranked as one of the best free cybersecurity tools. The community version of Burp Suite is free, but there is also a paid Enterprise Edition designed for enabling testing in DevSecOps.
Defendify is an all-in-one product that provides multiple layers of protection and offers consulting services if needed. With Defendify, organizations can streamline cybersecurity assessments, testing, policies, training, detection and response in one consolidated cybersecurity tool.
Features include cybersecurity risk assessments, technology and data use policies, incident response plans, penetration testing, threat alerts, phishing simulations and cybersecurity awareness training.
Many of the costliest data breaches and ransomware attacks in recent years can be traced back to simple phishing campaigns because many company workers fall for them. One of the best protections is to secretly test your staff to see who is gullible, and for that you can use the free program Gophish. Gophish is open source and provides a full-featured toolkit for security administrators to build their own phishing campaigns with relative ease. The overall goal is not to embarrass staff, but find out who needs greater phishing awareness and foster better security training within their organization.
Created by award-winning cybersecurity thought leader and teacher Troy Hunt, Have I Been Pwned is a website where you enter your email address to check if your address has been revealed in a data breach. Have I Been Pwned’s database is filled with billions of usernames, passwords, email addresses and other information that hackers have stolen and published online. Just enter your address in the search box.
Kali Linux is a Debian Linux derivative specifically designed toward testing for security tasks, such as penetration testing, security auditing and digital forensics. Kali includes roughly 600 pre-installed programs, each included to help computer security experts carry out a specific attack, probe or exploit against a target. Aircrack-ng, Nmap, Wireshark and Metasploit are a few of the pre-installed tools that ship with the Kali Linux download.
Similar to Kali Linux but at the application layer rather than OS, the Metasploit Framework can test computer system vulnerabilities or can be used to break into remote systems. It is, in other words, a network penetration “Swiss Army knife” used by both ethical hackers and criminal gangs to probe networks and applications for flaws and weaknesses. There is both a free and a commercial version — known as the Framework and Pro editions, respectively — which are available for trial. Both editions are de facto standard for penetration testing with more than 1,500 exploits. Metasploit comes pre-installed on Kali Linux.
Nmap is a free network mapper used to discover network nodes and scan systems for vulnerability. This popular free cybersecurity tool provides methods to find open ports, detect host devices, see which network services are active, fingerprint operating systems and locate potential backdoors.
While Nmap provides users immense power and capability to explore networks, the program has a rather steep learning curve to get over before one becomes truly proficient in using it.
Nikto is an ultra-powerful, command-line tool useful for uncovering vulnerabilities in web apps, services and web servers. Originally launched in the early 2000s, Nikto is still widely used by both blue and red teams that want to quickly scan web servers for unpatched software, misconfigurations and other security issues. The program also features built-in support for SSL proxies and intrusion detection system evasion. Nikto can run on any computer capable of supporting the Perl programming language.
OpenVAS is an all-in-one vulnerability scanner that comprehensively tests for security holes, misconfigured systems and outdated software. The scanner gets the tests for detecting vulnerabilities from a feed with daily updates. Much of the program’s power stems from its built-in programming interface, which enables developers to create custom scans that fit niche needs.
Its capabilities include unauthenticated and authenticated testing, high-level and low-level internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
OSSEC is a free program for cybersecurity professionals that’s been touted as one of the most popular systems for intrusion detection and prevention. Made up of multiple components — including a server, agent and router monitor — OSSEC is capable of rootkit detection, system integrity checking, threat alerts and response. One of OSSEC’s highlights is its comprehensive log analysis tool, empowering users to compare and contrast log events from many different sources.
OSSEC comes in three versions: standard; OSSEC+, which includes machine learning and real-time community update; and Atomic OSSEC, with more advanced functions.
Using only strong passwords — and keeping them secure — is an essential step in the security of any system. But since a best practice is to use a unique password for every website, app and service, that can get tricky. A good password manager makes it possible to safely store all passwords together so a user only needs to remember one master key rather than dozens of unique passwords. This is especially true for cybersecurity professionals tasked with guarding passwords to mission-critical systems. Fortunately, there are free password management tools. Three good, free options for cybersecurity pros are KeePass, Bitwarden and Psono.
The firewall/router software pfSense can be installed on either a physical computer or virtual machine to protect networks. PfSense is based on the FreeBSD OS, and has become one of the most popular open source firewall/router projects available. PfSense can also be configured for intrusion detection and prevention, traffic shaping, load balancing and content filtering. The pfSense site includes a tour, a community page, a link to both training and support and a download of the latest version of the community edition of the software.
Endpoint fingerprinting is analysis of web traffic to find patterns, responses and packets sent and received in a particular direction — even if they are encrypted. This works even with “dumb” devices that don’t interact with the network but can still enable unauthorized access to an organization’s systems.
P0f is a simple yet powerful network-level fingerprinting and forensics program. While other free cybersecurity programs do a similar job, p0f is unique in that it’s designed for stealth. Where most other programs rely on active scanning and packet injection, p0f can identify fingerprints and other vital information without network interference. Being passive rather than active means p0f is nearly impossible to detect and even harder to block, making it a favorite tool for ethical hackers and cybercriminals alike.
Normally the dissection and examination of malware is left to the antimalware vendors. But if you would like to do the job yourself, there is REMnux, a free Linux toolkit for reverse-engineering and analyzing malware.
Included in every REMnux distribution are tools to analyze Windows executables, reverse-engineer binaries and inspect suspicious documents. It also includes a collection of free tools cybersecurity professionals can use to monitor networks, gather data and conduct memory forensics.
Security Onion is an open source software collection based on the Linux kernel that helps cybersecurity professionals develop a comprehensive profile of their system’s security posture. Security Onion provides network monitoring using full packet capture, host-based and network-based intrusion detection systems, log indexing, search and data visualization features.
The operating system emphasizes ease of use and makes it possible to interweave data and analytics from multiple tools into a unified dashboard. The overarching goal of the project is to offer teams a foolproof security monitoring solution that reduces decision paralysis and false alerts.
Snort is an open source network intrusion prevention and intrusion detection system capable of real-time traffic analysis and logging. It uses a series of rules to identify malicious network activity, find the packets and generate alerts. This packet sniffer — managed by Cisco — actively searches and analyzes networks to detect probes, attacks and intrusions. Snort accomplishes this by fusing a sniffer, packet logger and intrusion detection engine into a single package.
Its developer recently released version 3, which includes a new rule parser and rule syntax, support for multiple packet-processing threads, use of a shared configuration and attribute table, access to more than 200 plugins, rewritten TCP handling and new performance monitoring.
Sqlmap is an open source penetration testing tool that automates detecting and exploiting SQL injection flaws of database servers, enabling a remote hacker to take control. It comes with a detection engine and many niche features for the ultimate penetration tester. It supports a variety of databases — including Oracle and open source — and a number of injection types.
Wireshark is considered by many to be an indispensable tool to locate, identify and examine network packets to diagnose critical issues and spot security weaknesses. The website for Wireshark outlines its broad set of features and provides a user’s guide and other resources for putting this free cybersecurity tool to best use.
ZAP is an open source penetration testing tool designed specifically for testing web applications. It is known as a “man-in-the-middle proxy,” where it intercepts and inspects messages sent between browsers and web applications.
ZAP provides functionality for developers, testers new to security testing and security testing specialists. There are also versions for each major operating system and Docker. Additional functionality is available via add-ons in the ZAP Marketplace.
Every cybersecurity expert carries a different set of tools, depending on their mission and skill set. However, the free cybersecurity tools here serve as an entry point for those looking to increase their cybersecurity skills and knowledge. Cyberthreats are getting more lethal every year — and more efficient.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 31 2024
Jan 30 2024
Aembit Becomes the First Workload IAM Platform to Integrate with the Industry-Leading CrowdStrike Falcon Platform to Drive Workload Conditional Access
Aembit, the Workload Identity and Access Management (IAM) platform that enables DevOps and security teams to discover, manage, enforce and audit access between workloads, today announced the availability of a new integration with the industry-leading CrowdStrike Falcon® platform to give enterprises the ability to dynamically manage and enforce conditional access policies based on the real-time security posture of their applications and services.
This integration signifies a significant leap in Aembit’s mission to empower organizations to apply Zero Trust principles to make workload-to-workload access more secure and manageable.
Workload IAM transforms enterprise security by securing workload-to-workload access through policy-driven, identity-based, and secretless access controls, moving away from the legacy unmanaged, secrets-based approach.
Through this partnership, the Aembit Workload IAM solution checks to see if a CrowdStrike Falcon agent is running on the workload and evaluates its real-time security posture to drive workload access decisions to applications and data.
With this approach, now enterprises can protect their workloads from unauthorized access, even against the backdrop of changing conditions and dynamic access requirements. Additional customer benefits from this partnership include:
This industry-first collaboration builds on the recent CrowdStrike Falcon Fund strategic investment in Aembit, underscoring the global cybersecurity leader’s commitment to fostering innovation within the space. The investment reflects the recognition of the growing demands for securing workload access.


InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 18 2024
Today, DDoS attacks stand out as the most widespread cyber threat, extending their impact to APIs.
When successfully executed, these attacks can cripple a system, presenting a more severe consequence than DDoS incidents targeting web applications.
The increased risk amplifies the potential for reputational damage to the company associated with the affected APIs.
A DDoS attack on an API involves overwhelming the targeted API with a flood of traffic from multiple sources, disrupting its normal functioning and causing it to become unavailable to legitimate users.
This attack can be particularly damaging as APIs play a crucial role in enabling communication between different software applications, and disruption can impact the overall functionality of interconnected systems.
The impact of DDoS attacks is particularly severe for businesses and organizations that depend on their APIs to deliver essential services to customers. These attacks, employing methods such as UDP floods, SYN floods, HTTP floods, and others, pose a significant threat.
Typically orchestrated through botnets—networks of compromised devices under the control of a single attacker—DDoS attacks can cripple a target’s functionality.
DDoS attacks on APIs focus on the server and each part of your API service. But how do attackers manage to exploit DDoS attacks on APIs?
This Webinar on API attack simulation shows an example of a DDoS attack on APIs and how WAAP can protect the API endpoints.
Several factors can make APIs vulnerable to DDoS attacks:
Absence or insufficient Rate-Limiting: If an API lacks robust rate-limiting mechanisms, attackers can exploit this weakness by sending a massive volume of requests in a short period, overwhelming the system’s capacity to handle them.
Inadequate Authentication and Authorization: Weak or compromised authentication measures can allow malicious actors to gain unauthorized access to an API. Once inside, they may misuse the API by flooding it with requests, leading to a DDoS scenario.
Insufficient Monitoring and Anomaly Detection: Ineffective monitoring and anomaly detection systems can make identifying abnormal traffic patterns associated with a DDoS attack challenging. Prompt detection is crucial for implementing mitigation measures.
Scalability Issues: APIs that cannot scale dynamically in response to increased traffic may become targets for DDoS attacks. A sudden surge in requests can overload the system if it cannot scale its resources efficiently.
How Do WAAP Solutions Protect Against DDoS Attacks on API?
Web Application and API Protection (WAAP) platform offers in-line blocking capabilities for all layer seven traffic, comprehensively securing web applications and APIs.
To guarantee robust security, WAFs incorporated into WAAP solutions provide immediate defense by filtering, monitoring, detecting, and automatically blocking malicious traffic, thereby preventing its access to the server.
Active monitoring of traffic on an API endpoint enables the identification of abnormal traffic patterns commonly linked to DDoS attacks. Instances of sudden spikes in traffic volume serve as red flags for potential attacks, and a proficient monitoring system can promptly detect and address such increases.
In addition, WAAP enforces rate limits by assessing the number of requests from an IP address. API rate limiting is critical in mitigating DDoS damage and reducing calls, data volume, and types. Setting limits aligned with API capacity and user needs enhances security and improves the user experience.
To avoid impacting genuine users, find solutions that use behavioral analysis technologies to establish a baseline for rate limiting.
AppTrana WAAP’s DDoS mitigation employs adaptive behavioral analysis for comprehensive defense, detecting and mitigating various DDoS attacks with a layered approach. It distinguishes between “flash crowds” and real DDoS attacks, using real-time behavioral analysis for precise mitigation. This enhances accuracy compared to static rate limit-based systems.
Advanced API Security: OAuth 2.0 and Beyond
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 12 2024
Scammers are targeting multiple brands with “job offers” on Meta’s social media platform, that go as far as to offer what look like legitimate job contracts to victims.
A fresh wave of job scams is spreading on Meta’s Facebook platform that aims to lure users with offers for remote-home positions and ultimately defraud them by stealing their personal data and banking credentials.
Researchers from Qualys are warning of “ongoing attacks against multiple brands” offering remote work through Facebook ads that go so far as to send what look like legitimate work contracts to victims, according to a blog post published Jan. 10 by Jonathan Trull, Qualys CISO and senior vice president of solutions architecture.
The attackers dangle offers of work-at-home opportunities to lure Facebook users to install or move to a popular chat app with someone impersonating a legitimate recruiter to continue the conversation. Eventually, attackers ask for personal information and credentials that potentially can allow attackers to defraud them in the future.
Likely aiming to take advantage of people’s tendency to make resolutions in the new year, these fake job ads — a persistent online threat — typically “see a rise in prevalence following the holidays” when people are primed for new opportunities, Trull wrote.
The researchers discovered the scams because fake recruiters were purporting to be from Qualys with offers of remote work. The company, however, never posts its job listings on social media, only on its own website and reputable employment sites, Trull said.
The initial text lures for the scam occur in group chats that solicit users to move to private messaging with the scammer who posts the job opening. “In several cases, the scammer appears to have compromised legitimate Facebook users and then targeted their direct connections,” Trull wrote.
Once a victim installs Go Chat or Signal — the messaging apps used in the scam — attackers ask for additional details so they can receive and sign what appears to be an official Qualys job offer complete with logos, correct corporate addresses, and signature lines.
Attackers then ask victims to send a copy of a government-issued photo ID, both front and back, and told to digitally cash a check to buy software for a new computer that their new employer will ship to them.
Qualys has notified both Facebook and law enforcement of the scam and encourages users to do the same if they observe it on the platform. The blog post did not list the names of other companies or brands that might also be targeted in the attacks.
Job scams are indeed a constant online security issue, one that’s on the rise, according to the US Better Business Bureau (BBB). Online ads and phishing campaigns are popular conduits for job scammers, which use social engineering to bait people into responding and then either steal their personal data, online credentials, and/or money. Scams also can have a negative reputational impact on the companies whose brands are used in the scam.
To avoid being scammed by a fake job listing, Qualys provided some best practices for online employment seekers to follow when using the Internet to search for opportunities.
In general, a mindset of “if it’s too good to be true, it probably is” is a good rule of thumb to approaching online job listings, Trull wrote. “Listen to your intuition,” he added. “If it doesn’t feel right, you should probably not proceed.”
Qualys also advised that people always verify offers by looking up a job opening on an organization’s official website and contacting the company directly instead of using social media contacts that could be abused as part of a scam.
People also should be “highly skeptical” of any job solicitation that doesn’t come from an official source, even if the social media source making the offer appears trusted. Since social media accounts can be hijacked, the source can appear legitimate but isn’t.
Further, if an online recruiter asks a person to install an app to apply for a position, it’s probably a scam, Trull warned. “Real recruiters will call you, email, or set up a multimedia interview call at their expense without any concern — they are set up for it if they are a recruiter,” he wrote.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 06 2024
Red Team Guide by Hadess

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 04 2024
The latest stable channel update for Google Chrome, version 120.0.6099.199 for Mac and Linux and 120.0.6099.199/200 for Windows, is now available and will shortly be rolled out to all users.
Furthermore, the Extended Stable channel has been updated to 120.0.6099.200 for Windows and 120.0.6099.199 for Mac.
There are six security fixes in this release. Three of these flaws allowed an attacker to take control of a browser through use-after-free conditions.
Use-after-free is a condition in which the memory allocation is freed, but the program does not clear the pointer to that memory. This is due to incorrect usage of dynamic memory allocation during an operation.
Use after free in ANGLE in Google Chrome presents a high-severity vulnerability that might have led to a remote attacker compromising the renderer process and using a crafted HTML page to exploit heap corruption.
Google awarded $15,000 to Toan (suto) Pham of Qrious Secure for reporting this vulnerability.
This high-severity flaw was a heap buffer overflow in ANGLE that could have been exploited by a remote attacker using a crafted HTML page to cause heap corruption.
Toan (suto) Pham and Tri Dang of Qrious Secure received a $15,000 reward from Google for discovering this vulnerability.
A high-severity use after free in WebAudio in Google Chrome might potentially allow a remote attacker to exploit heap corruption through a manipulated HTML page.
Google awarded Huang Xilin of Ant Group Light-Year Security Lab a $10,000 reward for finding this issue.
A remote attacker may have been able to exploit heap corruption through a specifically designed HTML page due to high severity vulnerability in Google’s use after free in WebGPU.
The details about the reporter of this vulnerability were mentioned as anonymous.
The use after free conditions existed in Google Chrome before version 120.0.6099.199. To avoid exploiting these vulnerabilities, Google advises users to update to the most recent version of Google Chrome.

Browser Security Platform Checklist
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Jan 03 2024
Information stealing malware are actively taking advantage of an undocumented Google OAuth endpoint named MultiLogin to hijack user sessions and allow continuous access to Google services even after a password reset.
According to CloudSEK, the critical exploit facilitates session persistence and cookie generation, enabling threat actors to maintain access to a valid session in an unauthorized manner.
The technique was first revealed by a threat actor named PRISMA on October 20, 2023, on their Telegram channel. It has since been incorporated into various malware-as-a-service (MaaS) stealer families, such as Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake.
The MultiLogin authentication endpoint is primarily designed for synchronizing Google accounts across services when users sign in to their accounts in the Chrome web browser (i.e., profiles).
A reverse engineering of the Lumma Stealer code has revealed that the technique targets the “Chrome’s token_service table of WebData to extract tokens and account IDs of chrome profiles logged in,” security researcher Pavan Karthick M said. “This table contains two crucial columns: service (GAIA ID) and encrypted_token.”
This token:GAIA ID pair is then combined with the MultiLogin endpoint to regenerate Google authentication cookies.
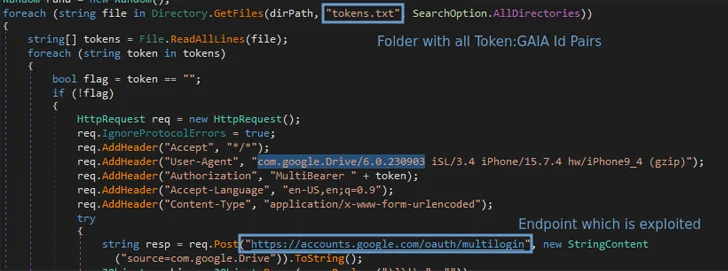
Karthick told The Hacker News that three different token-cookie generation scenarios were tested –
When reached for comment, Google acknowledged the existence of the attack method but noted that users can revoke the stolen sessions by logging out of the impacted browser.
“Google is aware of recent reports of a malware family stealing session tokens,” the company told The Hacker News. “Attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware. In this instance, Google has taken action to secure any compromised accounts detected.”
“However, it’s important to note a misconception in reports that suggests stolen tokens and cookies cannot be revoked by the user,” it further added. “This is incorrect, as stolen sessions can be invalidated by simply signing out of the affected browser, or remotely revoked via the user’s devices page. We will continue to monitor the situation and provide updates as needed.”
The company further recommended users turn on Enhanced Safe Browsing in Chrome to protect against phishing and malware downloads.
“It’s advised to change passwords so the threat actors wouldn’t utilize password reset auth flows to restore passwords,” Karthick said. “Also, users should be advised to monitor their account activity for suspicious sessions which are from IPs and locations which they don’t recognize.”
“Google’s clarification is an important aspect of user security,” said Hudson Rock co-founder and chief technology officer, Alon Gal, who previously disclosed details of the exploit late last year.
“However, the incident sheds light on a sophisticated exploit that may challenge the traditional methods of securing accounts. While Google’s measures are valuable, this situation highlights the need for more advanced security solutions to counter evolving cyber threats such as in the case of infostealers which are tremendously popular among cybercriminals these days.”
(The story was updated after publication to include additional comments from CloudSEK and Alon Gal.)
The Web Application Hacker’s Handbook: Discovering and Exploiting Security Flaws
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 28 2023
Barracuda Email Security Gateway (ESG) Appliance has been discovered with an Arbitrary code Execution vulnerability exploited by a China Nexus threat actor tracked as UNC4841.
Additionally, the vulnerability targeted only a limited number of ESG devices.
However, Barracuda has deployed a security update to all the active ESGs to address this vulnerability, and has been automatically applied to all the devices, which does not require any action from the user.
The new vulnerability has been assigned to CVE-2023-7102, and the severity is yet to be categorized.
This vulnerability exists due to using a third-party library, “Spreadsheet::ParseExcel,” in the Barracuda ESG appliances.
This open-source third-party library is vulnerable to arbitrary code execution that can be exploited by sending a specially crafted Excel email attachment to the affected device.
The Chinese Nexus threat actors have been using this vulnerability to deploy new variants of SEASPY and SALTWATER malware to the affected devices.
However, Barracuda has patched these vulnerabilities accordingly. Moreover, Barracuda stated, “Barracuda has filed CVE-2023-7102 about Barracuda’s use of Spreadsheet::ParseExcel which has been patched”.
Another vulnerability, CVE-2023-7101, affected the same spreadsheet: ParseExcel, and no patches or updates were available.
Nevertheless, both of these vulnerabilities were associated with a previously discovered vulnerability, CVE-2023-2868, that was exploited by the same threat group in May and June 2023.
Furthermore, a complete report about these vulnerabilities, along with additional information, has been published, which provides detailed information about this vulnerability and the previously discovered vulnerabilities.
| Malware | MD5 Hash | SHA256 | File Name(s) | File Type |
| CVE-2023-7102 XLS Document | 2b172fe3329260611a9022e71acdebca | 803cb5a7de1fe0067a9eeb220dfc24ca56f3f571a986180e146b6cf387855bdd | ads2.xls | xls |
| CVE-2023-7102 XLS Document | e7842edc7868c8c5cf0480dd98bcfe76 | 952c5f45d203d8f1a7532e5b59af8e330 6b5c1c53a30624b6733e0176d8d1acd | don.xls | xls |
| CVE-2023-7102 XLS Document | e7842edc7868c8c5cf0480dd98bcfe76 | 952c5f45d203d8f1a7532e5b59af8e330 6b5c1c53a30624b6733e0176d8d1acd | personalbudget.xls | xls |
| SEASPY | 7b83e4bd880bb9d7904e8f553c2736e3 | 118fad9e1f03b8b1abe00529c61dc3edf da043b787c9084180d83535b4d177b7 | wifi-service | x-executable |
| SALTWATER | d493aab1319f10c633f6d223da232a27 | 34494ecb02a1cccadda1c7693c45666e1 fe3928cc83576f8f07380801b07d8ba | mod_tll.so | x-sharedlib |
| IP Address | ASN | Location |
| 23.224.99.242 | 40065 | US |
| 23.224.99.243 | 40065 | US |
| 23.224.99.244 | 40065 | US |
| 23.224.99.245 | 40065 | US |
| 23.224.99.246 | 40065 | US |
| 23.225.35.234 | 40065 | US |
| 23.225.35.235 | 40065 | US |
| 23.225.35.236 | 40065 | US |
| 23.225.35.237 | 40065 | US |
| 23.225.35.238 | 40065 | US |
| 107.148.41.146 | 398823 | US |

Tiger Trap: America’s Secret Spy War with China
21st Century Chinese Cyberwarfare
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 20 2023
Without a Trace: How to Take Your Phone Off the Grid
A guide on anonymizing your phone, so you can use it without it using youBy Monique O. Madan and Wesley Callow
Hi, I’m Monique, an investigative reporter here at The Markup. There are a few key moments in my 15-year career that have led me on a quest to phone anonymity:
When a dark-tinted sedan followed me home after I published a controversial story, which led to the resignation of someone in power.
When a reader published my personal address in a virtual chatroom filled with thousands of people—the reader used my phone number to do a reverse look-up search, and found my address.
The last straw?
When the federal government traced my phone number back to me and blocked me from communicating with incarcerated people during the COVID-19 pandemic.
When I joined the team in August, my first order of business was making sure I had a secure way to connect with the people trusting me with their lives, while simultaneously keeping myself safe. I needed an off-the-grid phone.
Enter Wesley Callow, our IT support specialist.
What happens next is straight out of a scene of your favorite detective movie as he went about procuring the gear to build a phone that would protect my privacy. Just picture him in a cloak.
If I’ve learned anything from this, it’s that cash is king. And, I need a trench coat.
Just think of me, Wesley, as a London Fog trench coat, collar-popped-to-perfection kind of guy. When Monique reached out, I embarked on a trip into the world of phone anonymity—a meticulous descent into the “no half measures” underworld, to borrow from the series Breaking Bad, a place where digits and data are in disguise.
First thing: In order to make an anonymous purchase, I needed cash—bank and credit cards leave too much of a trace. I drove to our local grocery store and bought some groceries for my teenage boys. This is an almost daily trip, so definitely no suspicious behavior to be spotted. I chatted up the self-checkout assistant about the boys and got an extra $60 in cash back.
When it comes to service providers, Mint Mobile emerged as a top contender, providing relative ease in activation without demanding personal details. They’re like that low-profile café where the barista doesn’t ask for your life story.
I then ventured off to two local Targets where, to my dismay, there were no Mint Mobile prepaid SIM cards. For my third attempt, I tried Best Buy.
I walked in, head down, headed to the cellphone section. Then, the prepaid carrier section. I perused the spinning display, and then, at the very bottom, there was ONE prepaid Mint Mobile SIM left! It was meant to be. For $45, I got three months of service.
I then headed to my next destination: a nearby drug store. I purchased an Apple Store gift card for $10, again using cash. (You could take an Android phone off the grid too, though, but we’re a Mac newsroom).
It was perfect. Zero people were in the store and the clerk was not chatty. I dropped the cash down, exact change—and bounced from the scene. Now I was ready.
I had a phone plan. Now, I needed a phone. To begin, Apple/Mac experts suggest purchasing a used, budget-friendly iPhone exclusively with cash. This method, they insist, guarantees no direct ties to one’s identity. Monique had an old phone hiding in her drawer. But first, I needed to make sure it had amnesia.
I had Monique send me her old iPhone via a box I shipped to her with a return label inside of it. Once I received it, I wiped the phone back to its factory settings and made sure there was no preexisting SIM card inside.
Then I put the phone into recovery mode, connected it to an old Mac with no Apple ID, and reformatted it again. Now, it’s double wiped for safety.
Everyone loves a fresh start, right?
For my public Wi-Fi, I infiltrated my local Starbucks. The scent of caramel frappuccinos and whispered secrets filled the air. Here, amidst the caffeine loyal, I set up accounts with Mint, Proton Mail, and Apple. The creation of a disposable email account is essential (Proton Mail is the favored platform), followed by setting up an Apple ID (You’ll need it to download apps on your phone) with your Apple gift card. And if you’re prompted to provide a billing address? Input a random, unrelated location. You won’t ever be connecting a credit card with a real billing address anyway.
Opt for a six-digit security code—not 123456.
Using this now-naked phone, my fresh Mint Mobile SIM card, and an Apple gift card, I sought out a public space with no association to me, such as a library or café—anywhere that has communal computers and Wi-Fi, so we can activate the phone’s service. But wait, Wesley, I thought public Wi-Fi was insecure! Like all things, you have to weigh the pros and cons. The odds of being compromised on a public Wi-Fi network are low in the time it would take to set up the accounts we need, and in return, we don’t have personal location data or a personal IP address attached to those accounts.
Once your accounts are set up, turn off Wi-Fi.
For security purposes, Face ID and Touch ID are a no-go. The unanimous advice: opt for a six-digit security code. And don’t make it 123456.
Post-setup, disable Bluetooth. This is important because Bluetooth signals can be intercepted by third-party devices within range, and that allows hackers to access sensitive information, such as your phone’s contacts and messages. The throwaway Proton Mail email address plays another vital role, acting as the gateway to access Proton, a virtual private network (VPN) that masks all phone application traffic.
It’s like giving your phone a discreet disguise—instead of my trench coat, think Harry Potter’s invisibility cloak.
Always keep your VPN on, and routinely check that it’s working. Subsequently, any required apps should only be downloaded with the VPN engaged.
Maintaining this cloak of invisibility comes with challenges. If you find this overwhelming, we totally get it. But doing at least some of these steps will protect you—just find the balance and tradeoffs that work for you. For day-to-day usage, some golden rules emerge:
This phone should strictly be used for its principal purpose. Do not use it for casual online strolls, superfluous apps, or note storage.
Monique here. Do you feel like you just ran a marathon after reading that? Do you need a moment to process? I sure did.
As a gritty street reporter at heart, I’ve learned true and complete anonymity isn’t easy. But in this line of work, it’s worth it. That means constantly backing up my documents and keeping a duplicate contact list elsewhere, in case my line is compromised and I need a new burner.
Wait, did I just use the word “burner”? Feels like I’m living in an episode of How to Get Away with Murder. (Hi, Viola Davis!)
Covering criminal justice, immigration, social justice, and government accountability means my cellphone is my best friend. It’s not only the first line of communication with my sources, but it’s my first line of trust. My phone hosts applications to make contact with people behind bars—oftentimes the only line the incarcerated has to the outside world. It’s the device that rings in the middle of the night from inconsolable parents who have been separated from their children at the border.
Additionally, it confidentially stores my emails and documents people send to me, and it lets me access encrypted chatrooms that help me better understand and network with the communities I cover.
In today’s hyper-connected era, the lengths some are going to preserve their phone anonymity are undeniably intricate. While not a path for everyone, this approach paints a vivid picture of the extreme measures individuals are willing to take in the name of privacy.
As for me, I keep a copy of Wesley’s guide tucked away, so I don’t forget the many, many rules of how to master this cash-gift-card-SIM-phone-wipedown operation. I want my sources—and people on the fence on whether or not to trust me—to know that I am committed to protecting their identity, privacy, and stories.

Living Off the Grid: A Teen’s Guide On How to Navigate Life Without a Cellphone
The Invisible Web: How to Stay Anonymous Online
When spyware turns phones into weapons
How a Spy in your pocket threatens the end of privacy, dignity and democracy

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 12 2023
What is Cyberwarfare:
Cyberwar refers to the use of digital technology, including computer systems, networks, and electronic communication, as a means to conduct warfare in the virtual realm. In a cyberwar, conflicting parties leverage cyber capabilities to carry out attacks and defenses in an attempt to achieve strategic, political, or military objectives. These attacks can target a wide range of digital assets, including computer systems, networks, and information systems.
Cyberwarfare encompasses various tactics, techniques, and procedures, such as hacking, malware deployment, denial-of-service attacks, and information warfare. The goals of cyberwarfare can range from disrupting or destroying critical infrastructure to stealing sensitive information, conducting espionage, or influencing public opinion.
Key characteristics of cyberwar include its asymmetric nature, where a smaller, technologically sophisticated actor may pose a significant threat to a larger, conventionally powerful entity. Attribution, or determining the origin of cyber attacks, can be challenging, adding complexity to the dynamics of cyberwarfare.
Governments, military organizations, and other entities invest in cybersecurity measures to defend against cyber threats and protect their critical assets from potential attacks in the digital domain. The landscape of cyberwarfare is continually evolving as technology advances and new vulnerabilities emerge.
The Cyber War is Here: U.S. and Global Infrastructure Under Attack: A CISO’s Perspective
“The Cyber War Is Here” simplifies the complex world of cybersecurity, cyber risk, and the crucial relationship between corporate boards and Chief Information Security Officers (CISOs). Written by a distinguished cybersecurity expert and USAF Veteran, it emphasizes the strategic importance of cybersecurity in modern business. Marc highlights the evolving role of CISOs, emphasizing their shift from IT guardians to strategic advisors to the board. The book explores successful board-CISO interactions and the consequences of misalignment, offering a clear blueprint for effective partnership. “The Cyber War Is Here” dives into the national and economic security implications of cyber threats, stressing the critical link between cybersecurity and national defense. The book argues that strengthening digital defenses and fostering public-private sector collaboration is essential for national resilience. Designed for a broad audience, from individuals to boards of directors, CISOs, business executives, and policymakers, this book serves as a call to action for proactive cyber governance. It illuminates the interconnectedness of individual organizational security and national security, providing both a catalog of risks and strategies and a roadmap for action in the global cyber conflict arena. “The Cyber War Is Here” is a call to action for all.

Cyber warfare

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 06 2023
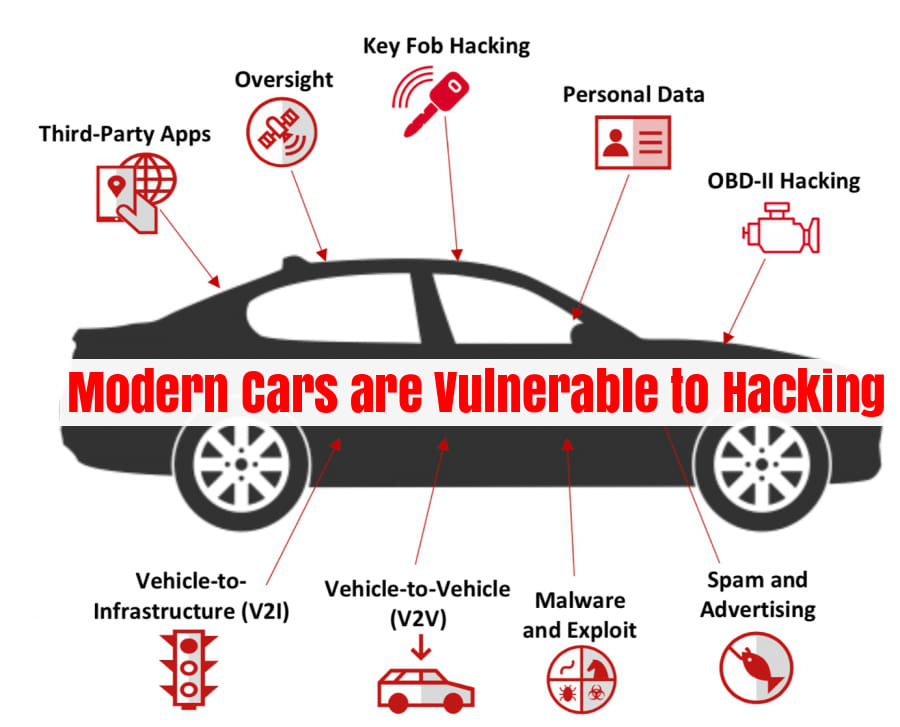
It is so easy to vacuum up private data from vehicles that Andrea Amico taught his daughter how to extract text messages from her mom’s car when she was only eight years old.
Blue-haired and an engineer by training, Amico has a hacker’s mentality, which has manifested in giving drivers a way to protect their data and beat the system at no cost.
Amico is the founder and CEO of Privacy4Cars, the outfit behind a free app that lets individuals erase the astonishing amount of personal data — including text messages, biometrics and geolocation — that many automakers collect, store and often share with law enforcement, insurers and even data brokers.
Privacy4Cars also allows consumers to pull a full report on exactly what data their own car is scooping up, using nothing but a vehicle identification number.
Amico worked on car data privacy for years on what he called a “passion project” basis. After running a large car inspection business, he came to understand the scale of the problem — and the stakes — and founded Privacy4Cars in 2019.
Consumers can use the app to delete data retroactively, but there is no way to block its collection moving forward so those especially concerned about privacy have to regularly wipe the car’s data, which usually primarily resides in the infotainment system, Amico said.
The process for deletion is unique for most car models and types. Amico says the company has amassed step-by-step delete instructions for tens of thousands of vehicles, whose settings often differ by model, make, year manufactured and even how many extras customers pay for to enhance a given model.
The app typically works for four out of five cars. Wiping data can take as few as three commands, or as many as 50, Amico said. If a car owner has not downloaded a given car’s software updates, that can complicate matters.
Data linked to more than a million cars has been deleted using the app to date, Amico said.
With car data privacy in the spotlight recently, the demand is likely to rise.
Last month a Seattle-based federal judge declined to revive a class action lawsuit alleging four auto manufacturers had broken Washington state privacy laws by gathering and storing customers’ private text messages and mobile phone call logs.
The judge ruled the practice did not meet the threshold for an illegal privacy violation under state law, which requires plaintiffs prove that “his or her business, his or her person, or his or her reputation” has been threatened by the harvesting of private data.
Despite the ruling, car data privacy concerns are growing as more consumers become aware of their exposure, and even some industry figures concede more needs to be done to educate car owners about data practices.
Privacy4Cars offers a website feature which allows users to search their vehicle identification number and quickly learn the data their car gathers, pulling and crystallizing information from the small print manufacturers typically disclose in complex, dense and lengthy terms and conditions and privacy disclosures.
A recent search of what Privacy4Cars calls its “Vehicle Privacy Report” showed a variety of automakers disclosing they can or do pull, store and even sell a wide range of data, including:
Many automakers also acknowledge they share data with law enforcement, insurers and data brokers.
While some cars searched on the Privacy4Cars website were silent on whether they collect data from synced phones, Sean McKeever, a senior security researcher at GRIMM, a cybersecurity company with an automotive division, said most cars do gather and store phone data.
“If the vehicle offers phone connectivity, you can assume there is some level of data being stored on the vehicle,” McKeever said via email.
Amico estimated that about two-thirds of U.S. auto manufacturers declare they collect data from synced phones, at least for some models.
“They’re also very quick to say that it’s none of their responsibility and essentially it’s the consumers’ fault if they leave this data behind,” he said in an interview.
To use the Privacy4Cars’ Vehicle Privacy Report search tool, drivers must have their vehicle identification number (VIN). A recent random check of the privacy report’s portal, using VIN numbers linked to used vehicles on Carmax, showed that many cars collect all of the data listed above and more.
Vehicles collecting synced phone data, for example, included a 2018 Vokswagen Atlas, a 2023 Audi Q4, a 2019 Volvo XC90 and a 2020 Honda Civic. All of these vehicles also collect location data and some gather biometric data along with compiling personal identifiers and user profiles.
None of the automakers offered comment except for Volkswagen. A spokesperson said that “when a customer syncs their phone via Bluetooth, the car can access phone data as granted by the customer and all of this data is stored within the vehicle.”
They added that customers can delete this data at any time through a factory reset and noted that “while the car itself will access the data, the car does not transmit this data beyond the car.”
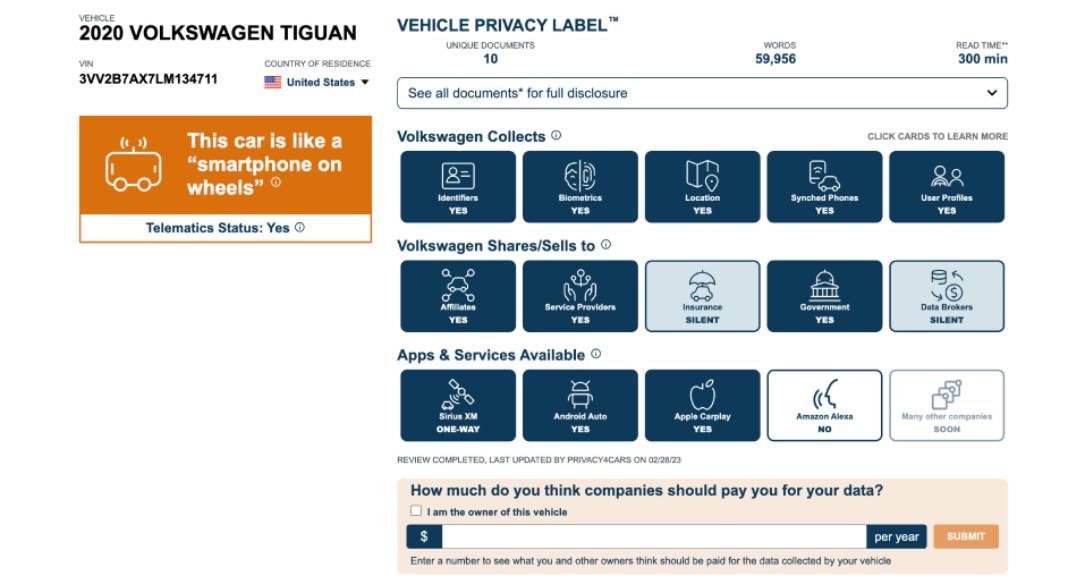 A privacy report for a 2020 Volkswagen Tiguan.
A privacy report for a 2020 Volkswagen Tiguan.
Many of the cars Recorded Future News searched in the Vehicle Privacy Report also allowed data to be collected from Android Auto, Apple Carplay and Amazon Alexa.
Amico said that if your car uses Android Auto, for example: “Guess what? Google collects data from you as well.” Google does not have an Android Auto-specific privacy policy or data disclosure, Amico said. The data can also potentially be sold by Google for targeted advertising. Google did not respond to a request for comment.
Privacy4Cars also takes on data brokers, offering a way for consumers to easily reach them and tell them not to sell their data. An “Assert Your Rights” button on the upper right corner of the company’s homepage takes users to a place to share their information so that Privacy4Cars can submit consumer privacy requests to first-party businesses, data brokers, and third parties on their behalf.
Most drivers have no idea what data their car is collecting because other than through Privacy4Cars it can be very hard to track down and digest the information. The privacy disclosures for the four cars mentioned above involved between nine and 12 unique documents, and each ran between 55,00 and 60,000 words, according to the Privacy4Cars site.
Older cars appear not to be immune. A check for a 2012 Honda Odyssey, for example, revealed the vehicle collects data from synced phones, geolocation information and compiles personal identifiers and user profiles.
Car owners should use the app to wipe data particularly when they buy or sell a used car and return vehicles to car rental agencies or leasing companies, Amico said, although most people don’t know they should do so.
Four out of five used cars contain the data of previous owners since most owners and subsequently car dealers don’t wipe them clean, he said.
In some cases cars even store pieces of code from previous drivers that can allow old owners to access new owners’ data. Most cars’ infotainment systems also store text messages and other unencrypted data.
Amico’s services aren’t foolproof. The FBI, for instance, still might be able to hack into the car’s systems and extract data. But they do make it a “hell of a lot harder” for them or anyone else to do so.
Even those unworried about getting entangled with the FBI have serious reasons to delete their data, he said.
“If you have a navigation system, you have about a 50/50 chance that you can press two buttons and show up inside the house of somebody because you press ‘go home’ and then you pop the garage open,” Amico said.
This is Part 1 of a three-part series on automobile privacy that will run through the month of December.

Automated Vehicle Law: Legal Liability, Regulation, and Data Security

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Dec 03 2023
Introducing to Cybersecurity | Cyber Writes ✍

Introduction to Cyber Security: Basic to Advance Techniques
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory