
Dark forums and Telegram channels have become great places for threat actors to sell critical vulnerabilities and exploits.
These vulnerabilities and exploits were associated with the Elevation of Privilege, Authentication Bypass, SQL Injection, and Remote Code Execution in products like Windows, JetBrains software, Microsoft Streaming Service Proxy, and Ubuntu kernels.
Recent discoveries state that these vulnerabilities were sold in underground forums even before the Vendor officially assigned them.
One such example was the Microsoft Streaming Server vulnerability (CVE-2023-36802) that was on sale in February, though the CVE was officially assigned in September 2023.
Key Vulnerabilities
According to the reports shared with Cyber Security News, several critical and high-severity vulnerabilities were sold in the underground forums, which certain ransomware groups used to gain initial access and lateral movement inside the victim network.
Critical Vulnerabilities
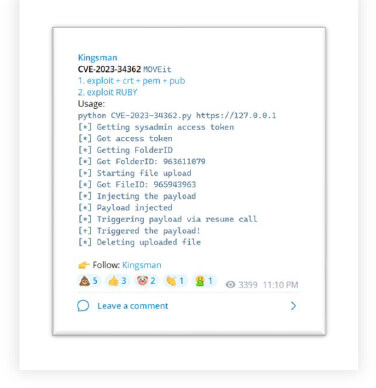
CVE-2023-34362: MOVEit RCE Vulnerability (Exploited By Cl0p Ransomware Group)
This vulnerability was published in NVD on June 02, 2023. However, it was observed to be exploited by threat actors since May 2023. This vulnerability had a severity of 9.8 (Critical) and was patched by Progress.
This vulnerability arises due to insufficient sanitization of user-provided data, which enables unauthenticated remote attackers to access the MOVEit application. With this vulnerability, the Cl0p ransomware group targeted more than 3000 organizations in the US and 8000 organizations worldwide.
CVE-2023-3519: Citrix ADC And Gateway Vulnerability (Exploited By Unknown Threat Actor)
NVD published this vulnerability on June 19, 2023, and Citrix patched it in July 2023. However, threat actors were seen to be exploiting this vulnerability in June 2023, which affected Netscaler ADC and Gateway versions.
A threat actor can use this vulnerability to execute remote code on affected Citrix ADC and Gateway systems to steal sensitive information without any authentication. The severity of this vulnerability was given as 9.8 (Critical).
CVE-2023-42793: JetBrains Unauthenticated RCE (Exploited By North Korean Threat Actors)
This vulnerability could allow an unauthenticated threat actor to access the TeamCity server and execute remote code,, which could compromise the source code and add to a supply chain attack.
This vulnerability was published in NVD in September 2023 and was found to be sold in the underground forums in October 2023. This authentication bypass leading to RCE vulnerability was given a severity of 9.8 (Critical).
According to Microsoft, this vulnerability was potentially used by North Korean nation-state threat actors like Diamond Sleet and Onyx Sleet to install malware and backdoors on their targets.
A complete report about the vulnerabilities sold on the underground market, their associated threat groups, and other information has been published.
Users of these products are recommended to patch the affected versions accordingly and take precautionary measures to prevent them from getting exploited by threat actors.
The Darkest Web: Drugs, Death and Destroyed Lives . . . the Inside Story of the Internet’s Evil Twin
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory

![The Darkest Web (Allison Barton Book 2) by [Kristin Wright]](https://m.media-amazon.com/images/I/51qZVAen96S.jpg)


