McKinsey’s playbook, “Deploying Agentic AI with Safety and Security,” outlines a strategic approach for technology leaders to harness the potential of autonomous AI agents while mitigating associated risks. These AI systems, capable of reasoning, planning, and acting without human oversight, offer transformative opportunities across various sectors, including customer service, software development, and supply chain optimization. However, their autonomy introduces novel vulnerabilities that require proactive management.
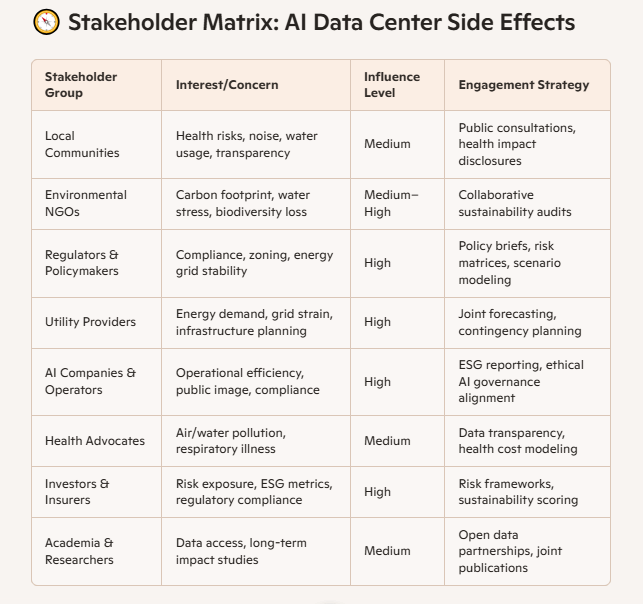
The playbook emphasizes the importance of understanding the emerging risks associated with agentic AI. Unlike traditional AI systems, these agents function as “digital insiders,” operating within organizational systems with varying levels of privilege and authority. This autonomy can lead to unintended consequences, such as improper data exposure or unauthorized access to systems, posing significant security challenges.
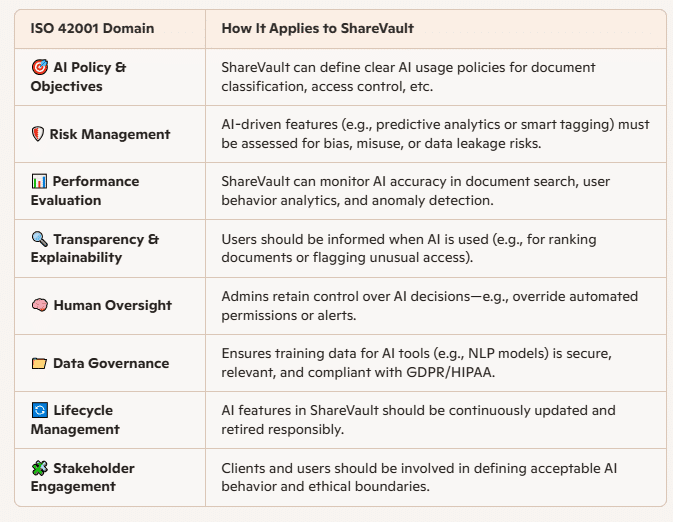
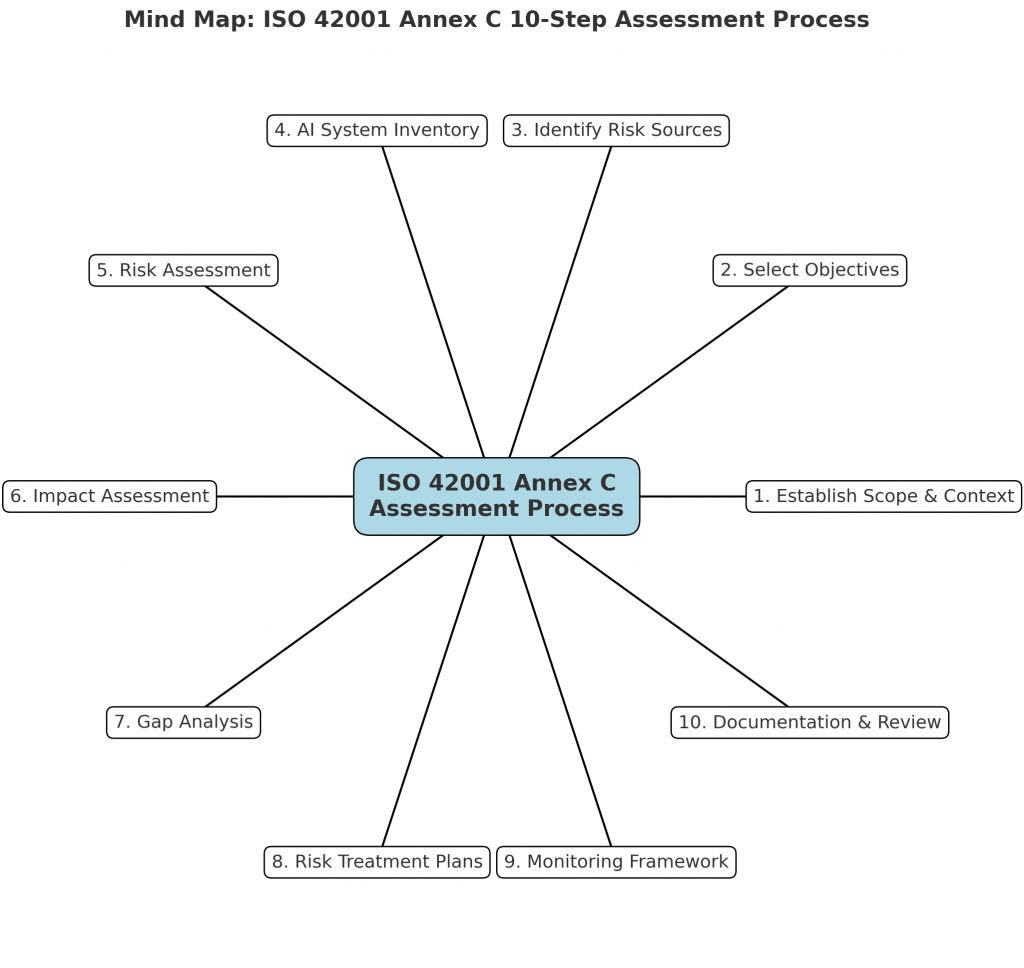
To address these risks, the playbook advocates for a comprehensive AI governance framework that integrates safety and security measures throughout the AI lifecycle. This includes embedding control mechanisms within workflows, such as compliance agents and guardrail agents, to monitor and enforce policies in real time. Additionally, human oversight remains crucial, with leaders focusing on defining policies, monitoring outliers, and adjusting the level of human involvement as necessary.
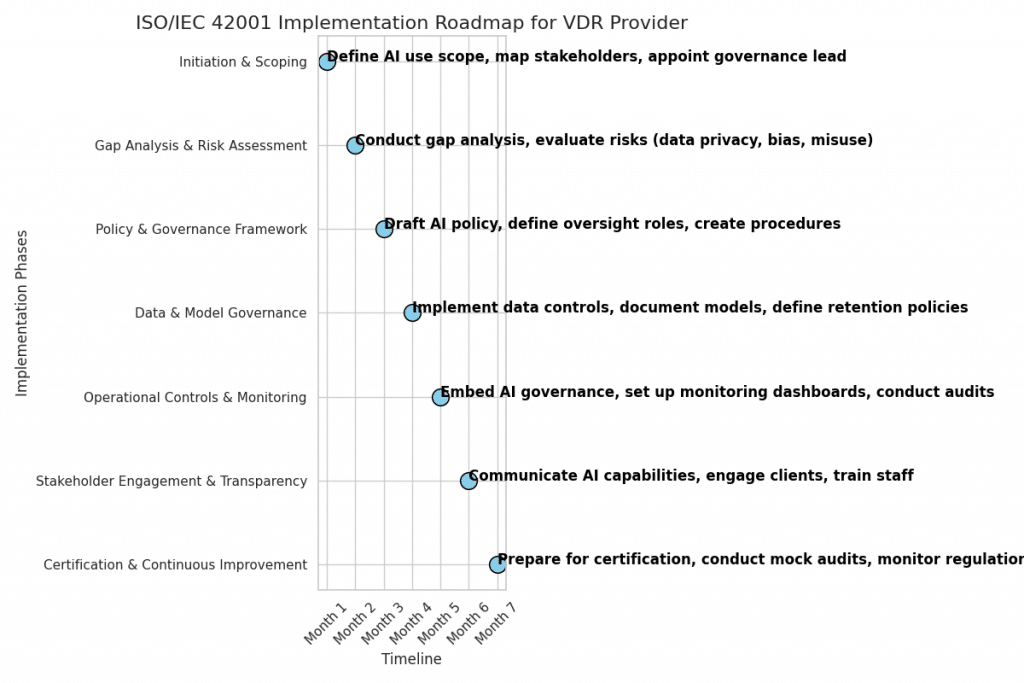
The playbook also highlights the necessity of reimagining organizational workflows to accommodate the integration of AI agents. This involves transitioning to AI-first workflows, where human roles are redefined to steer and validate AI-driven processes. Such an approach ensures that AI agents operate within the desired parameters, aligning with organizational goals and compliance requirements.
Furthermore, the playbook underscores the importance of embedding observability into AI systems. By implementing monitoring tools that provide insights into AI agent behaviors and decision-making processes, organizations can detect anomalies and address potential issues promptly. This transparency fosters trust and accountability, essential components in the responsible deployment of AI technologies.
In addition to internal measures, the playbook advises technology leaders to engage with external stakeholders, including regulators and industry peers, to establish shared standards and best practices for AI safety and security. Collaborative efforts can lead to the development of industry-wide frameworks that promote consistency and reliability in AI deployments.
The playbook concludes by reiterating the transformative potential of agentic AI when deployed responsibly. By adopting a proactive approach to risk management and integrating safety and security measures into every phase of AI deployment, organizations can unlock the full value of these technologies while safeguarding against potential threats.
My Opinion:
The McKinsey playbook provides a comprehensive and pragmatic approach to deploying agentic AI technologies. Its emphasis on proactive risk management, integrated governance, and organizational adaptation offers a roadmap for technology leaders aiming to leverage AI’s potential responsibly. In an era where AI’s capabilities are rapidly advancing, such frameworks are essential to ensure that innovation does not outpace the safeguards necessary to protect organizational integrity and public trust.
Click the ISO 42001 Awareness Quiz — it will open in your browser in full-screen mode
Protect your AI systems — make compliance predictable.
Expert ISO-42001 readiness for small & mid-size orgs. Get a AI Risk vCISO-grade program without the full-time cost.
Secure Your Business. Simplify Compliance. Gain Peace of Mind
Check out our earlier posts on AI-related topics: AI topic
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security