Better yet – do the basics and your systems won’t get encrypted in the first place
Source: Don’t pay the ransom, mate. Don’t even fix a price, say Australia’s cyber security bods
The infoseccers strongly advised against paying the criminals:
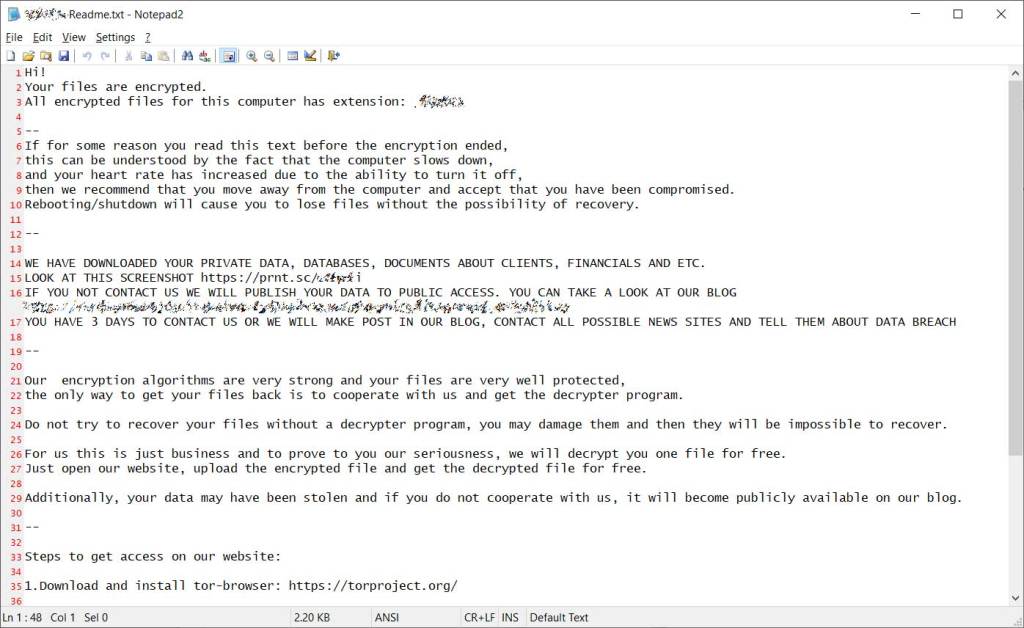
Paying a ransom does not guarantee decryption of data. Open source reporting indicates several instances where an entity paid the ransom but the keys to decrypt the data were not provided. The ACSC has also seen cases where the ransom was paid, the decryption keys were provided, but the adversary came back a few months later and deployed ransomware again. The likelihood that an Australian organizations will be retargeted increases with every successful ransom payment.
It is generally much easier and safer to restore data from a backup than attempting to decrypt ransomware affected data.
“Many of these [attacks] could have been avoided or substantially mitigated by good cyber security practices,” sighed the ACSC in the report (PDF, 18 pages), which covered the months July 2019-June 2020.
How to recover your system from a Ransomware attack
httpv://www.youtube.com/watch?v=kJuibb9QaWk&ab_channel=CSO
Download a Security Risk Assessment Steps paper!
Security Risk assessment Quiz – Find Out How Your security risk assessment Stands Up!
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Subscribe to DISC InfoSec blog by Email
👉 Download a Virtual CISO (#vCISO) and Security Advisory Fact Sheet & Cybersecurity Cheat Sheet