Threat actors hacked the official Git server of the PHP programming language and pushed unauthorized updates to insert a backdoor into the source code.
Unknown attackers hacked the official Git server of the PHP programming language and pushed unauthorized updates to insert a backdoor into the source code.
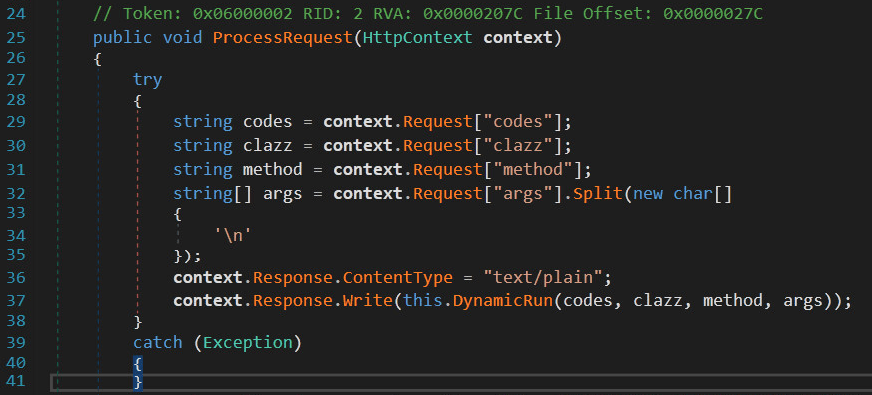
On March 28, the attackers pushed two commits to the “php-src” repository hosted on the git.php.net server, they used the accounts of Rasmus Lerdorf, the PHP’s author, and Jetbrains developer Nikita Popov.
Maintainers of the project are investigating the supply chain attacks, experts believe attackers have compromised the git.php.net server.
“We don’t yet know how exactly this happened, but everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account).” wrote Popov. “While investigation is still underway, we have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server. Instead, the repositories on GitHub, which were previously only mirrors, will become canonical. This means that changes should be pushed directly to GitHub rather than to git.php.net.”
The maintainers of the PHP reverted the changes and are reviewing the repositories to detect any other evidence of compromise beyond the two referenced commits.
In the future, in order to access the repositories, users will now need to be part of the php organization on GitHub and their account will have 2FA enabled. Adopting this new configuration it is possible to merge pull requests directly from the GitHub web interface.
At this time, it is not immediately clear if the backdoor was downloaded and distributed by other parties before the malicious commits were detected.