While investigating the recent SolarWinds Orion supply-chain attack security researchers discovered another backdoor, tracked SUPERNOVA.
The investigation of the SolarWinds Orion supply-chain attack revealed the existence of another backdoor that was likely used by a separate threat actor.
After the initial disclosure of the SolarWinds attack, several teams of researchers mentioned the existence of two second-stage payloads.
Security experts from Symantec, Palo Alto Networks, and Guidepoint reported that threat actors behind the SolarWinds attack were also planting a .NET web shell dubbed Supernova.
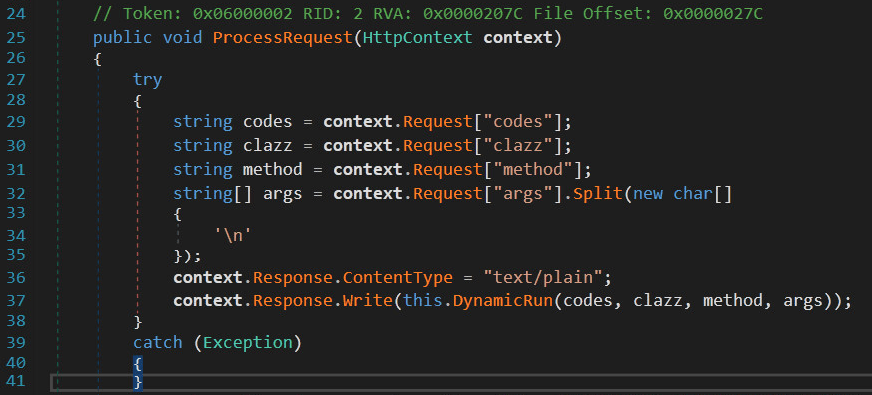
Researchers from Palo Alto Networks revealed that the malicious code is a tainted version of the legitimate .NET library “app_web_logoimagehandler.ashx.b6031896.dll” included in the SolarWinds Orion software.
“In the analysis of the trojanized Orion artifacts, the .NET .dll app_web_logoimagehandler.ashx.b6031896.dll was dubbed SUPERNOVA, but little detail of its operation has been publicly explored.” reads the analysis published by Palo Alto Networks.
“SUPERNOVA differs dramatically in that it takes a valid .NET program as a parameter. The .NET class, method, arguments and code data are compiled and executed in-memory. There are no additional forensic artifacts written to disk, unlike low-level webshell stagers, and there is no need for additional network callbacks other than the initial C2 request. In other words, the SolarStorm attackers have constructed a stealthy and full-fledged .NET API embedded in an Orion binary, whose user is typically highly privileged and positioned with a high degree of visibility within an organization’s network.”
Source: SUPERNOVA, a backdoor found while investigating SolarWinds hack
Learning about .NET Malware by Going Over the SUNBURST SolarWinds Backdoor
httpv://www.youtube.com/watch?v=cMauHTV-lJg