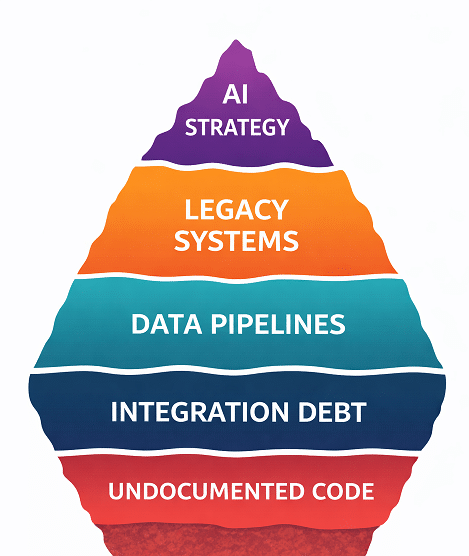
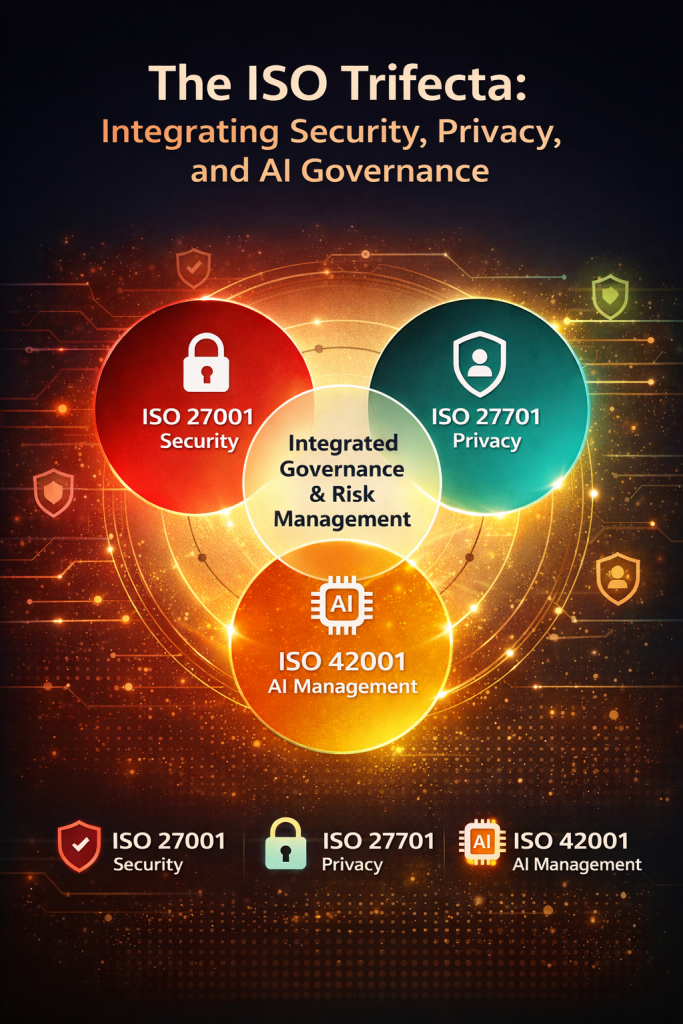
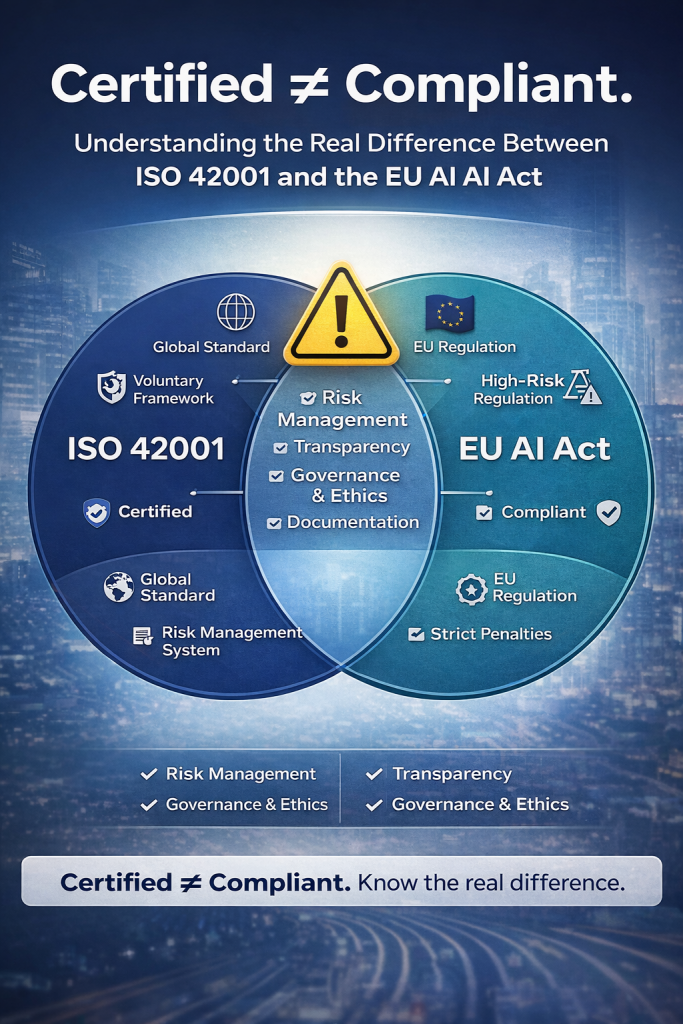
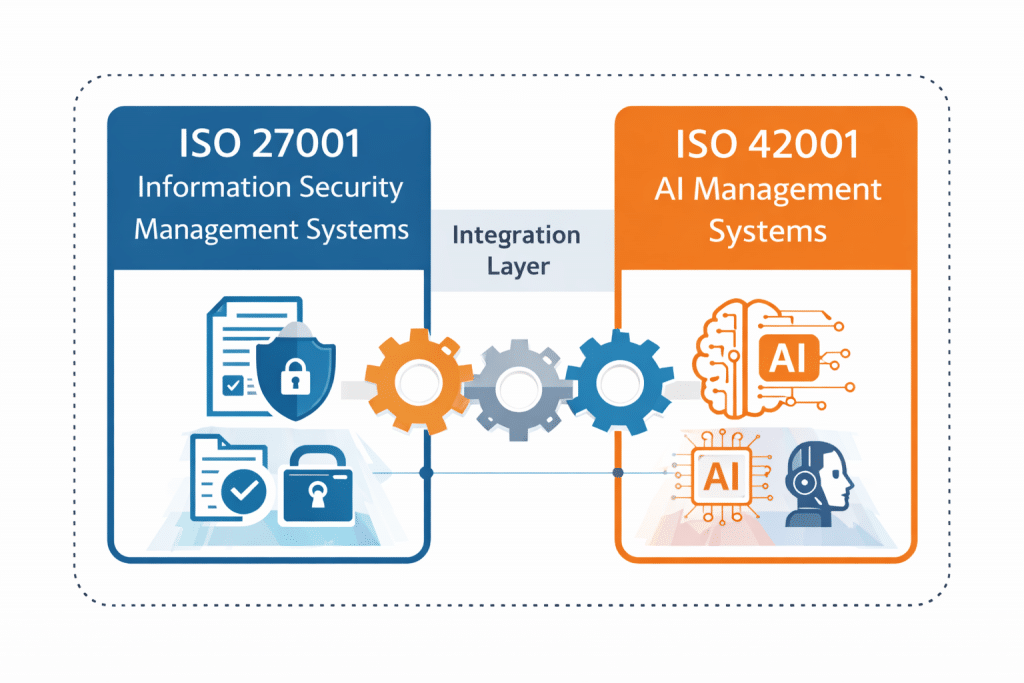
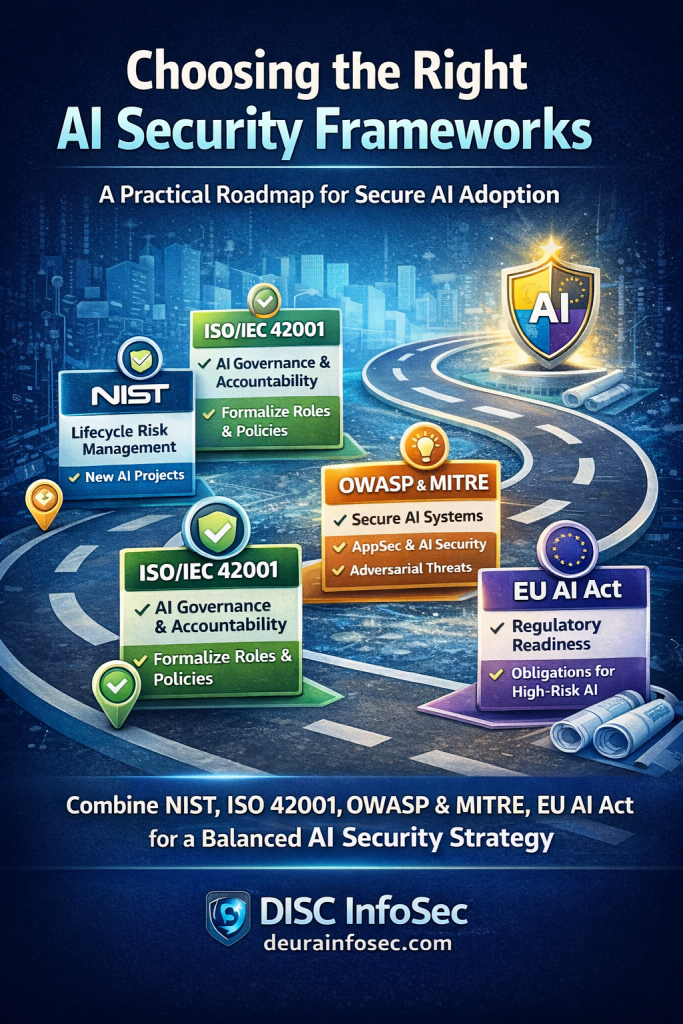
AI is transforming how organizations innovate, but without strong governance it can quickly become a source of regulatory exposure, data risk, and reputational damage. With the Artificial Intelligence Management System (AIMS) aligned to ISO/IEC 42001, DISC InfoSec helps leadership teams build structured AI governance and data governance programs that ensure AI systems are secure, ethical, transparent, and compliant. Our approach begins with a rapid compliance assessment and gap analysis that identifies hidden risks, evaluates maturity, and delivers a prioritized roadmap for remediation—so executives gain immediate visibility into their AI risk posture and governance readiness.
DISC InfoSec works alongside CEOs, CTOs, CIOs, engineering leaders, and compliance teams to implement policies, risk controls, and governance frameworks that align with global standards and regulations. From data governance policies and bias monitoring to AI lifecycle oversight and audit-ready documentation, we help organizations deploy AI responsibly while maintaining security, trust, and regulatory confidence. The result: faster innovation, stronger stakeholder trust, and a defensible AI governance strategy that positions your organization as a leader in responsible AI adoption.
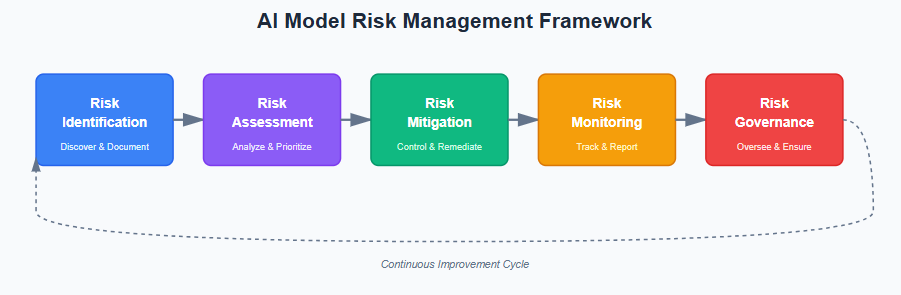
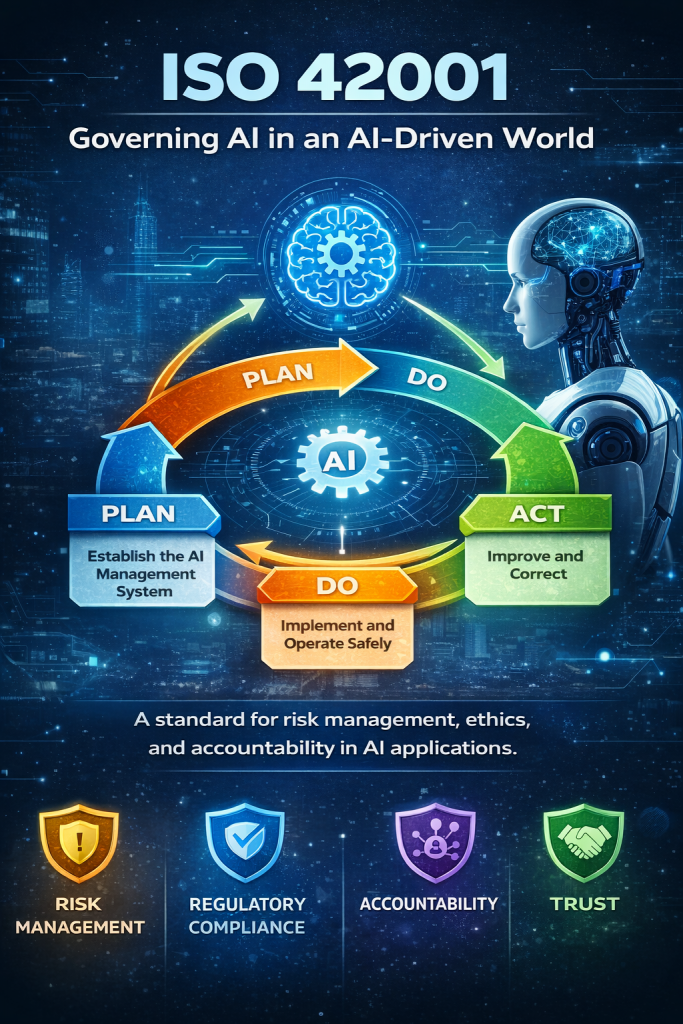
DISC InfoSec helps CEOs, CIOs, and engineering leaders implement an AI Management System (AIMS) aligned with ISO 42001 to manage AI risk, ensure responsible AI use, and meet emerging global regulations.
Get Your Free AI Governance Readiness Assessment – Is your organization ready for ISO 42001, EU AI Act, and emerging AI regulations?
AI Governance Gap Assessment tool
- 15 questions
- Instant maturity score
- Detailed PDF report
- Top 3 priority gaps
Click below to open an AI Governance Gap Assessment in your browser or click the image to start assessment.
ai_governance_assessment-v1.5Download
Built by AI governance experts. Used by compliance leaders.
AI & Data Governance: Power with Responsibility – AI Security Risk Assessment – ISO 42001 AI Governance
In today’s digital economy, data is the foundation of innovation, and AI is the engine driving transformation. But without proper data governance, both can become liabilities. Security risks, ethical pitfalls, and regulatory violations can threaten your growth and reputation. Developers must implement strict controls over what data is collected, stored, and processed, often requiring Data Protection Impact Assessment.
With AIMS (Artificial Intelligence Management System) & Data Governance, you can unlock the true potential of data and AI, steering your organization towards success while navigating the complexities of power with responsibility.
Limited-Time Offer: ISO/IEC 42001 Compliance Assessment – Clauses 4-10
Evaluate your organization’s compliance with mandatory AIMS clauses & sub clauses through our 5-Level Maturity Model
Limited-Time Offer — Available Only Till the End of This Month!
Get your Compliance & Risk Assessment today and uncover hidden gaps, maturity insights, and improvement opportunities that strengthen your organization’s AI Governance and Security Posture.
Click the image below to open your Compliance & Risk Assessment in your browser.
✅ Identify compliance gaps
✅ Receive actionable recommendations
✅ Boost your readiness and credibility
Built by AI governance experts. Used by compliance leaders.
AI Governance Policy template
Free AI Governance Policy template you can easily tailor to fit your organization.
AI_Governance_Policy template.pdf
Adobe Acrobat document [283.8 KB]

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
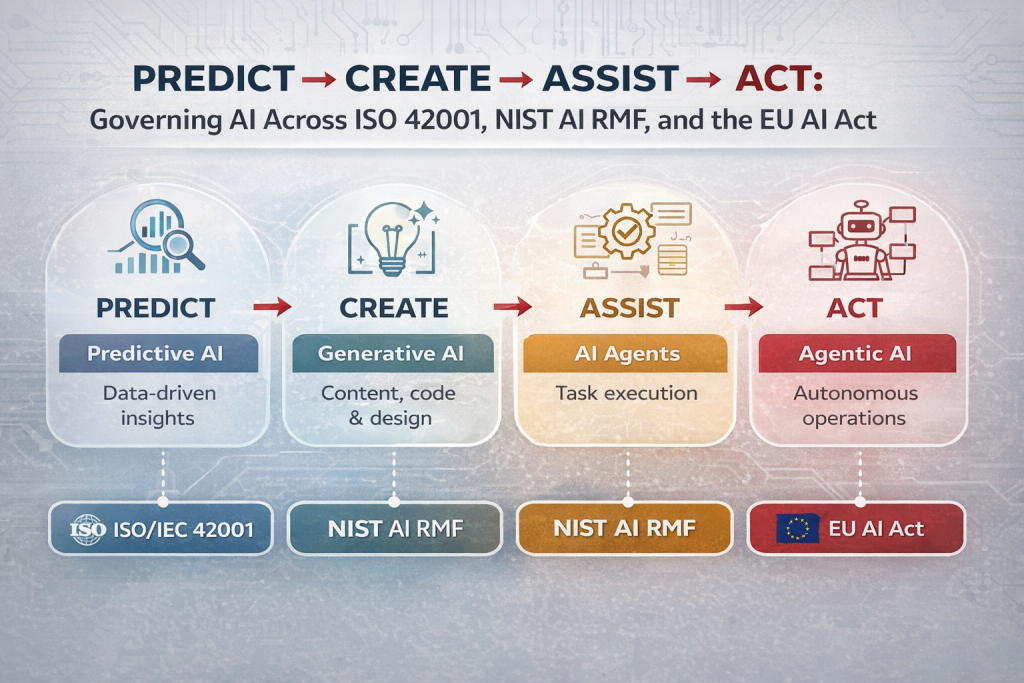
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- AI Agents and the New Cybersecurity Frontier: Understanding the 7 Major Attack Surfaces
- Understanding AI/LLM Application Attack Vectors and How to Defend Against Them
- AI Governance Assessment for ISO 42001 Readiness
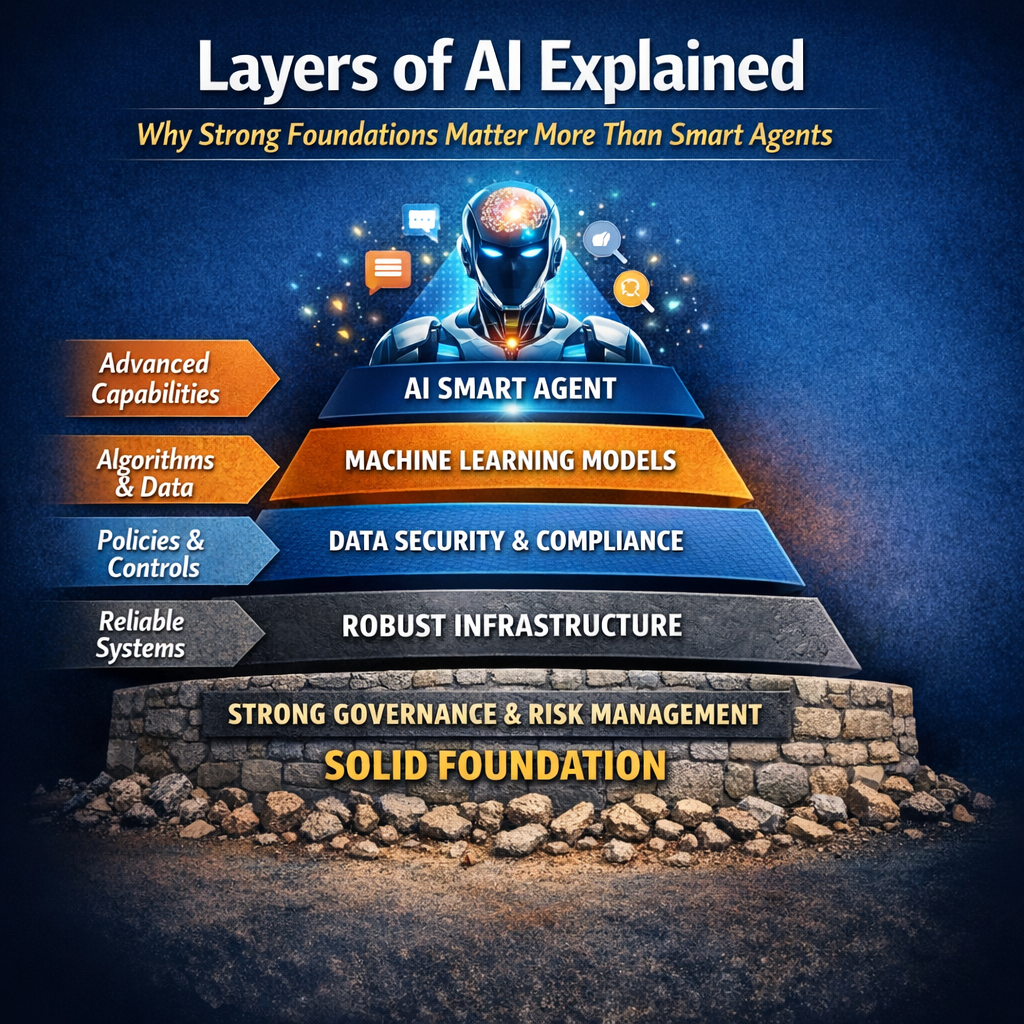
- Beyond ChatGPT: The 9 Layers of AI Transforming Business from Analytics to Autonomous Agents
- CMMC Level 2 Third-Party Assessment: What It Is, Why It Matters, and What to Expect