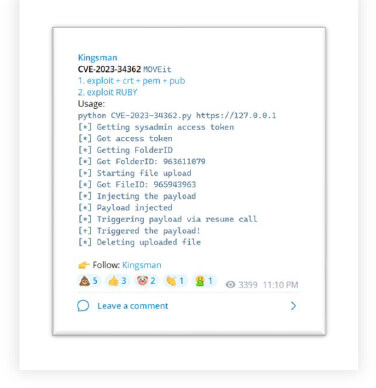
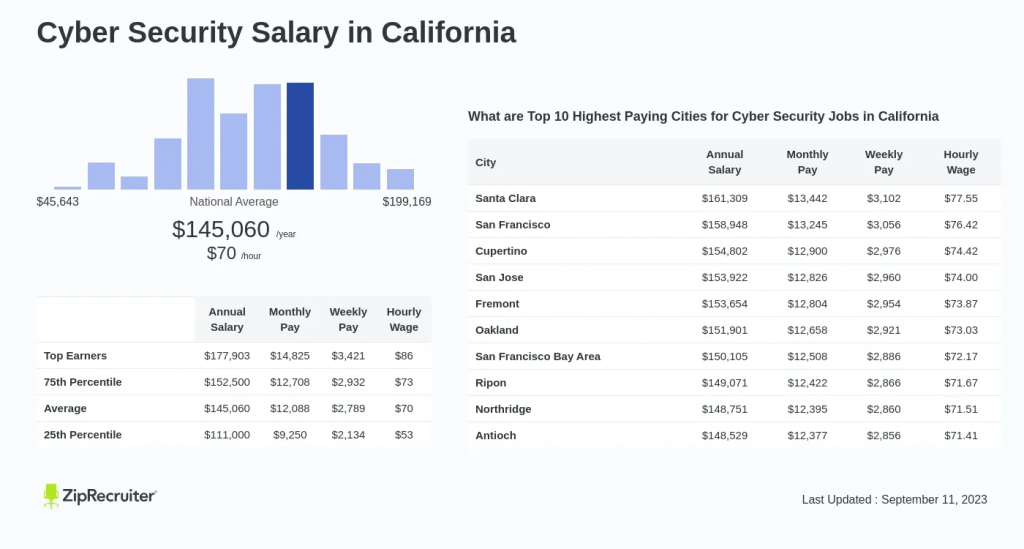
SystemBC (aka Coroxy or DroxiDat) is a multifunctional malware known as Proxy, Bot, Backdoor, and RAT, adapting to attackers’ needs.
Since 2018, this multifunctional malware has been active, and it remains popular in underground markets, with consistent annual incidents.
Cybersecurity researcher, REXor (aka Aaron) recently discovered that several ransomware groups are employing SystemBC, a Swiss Knife proxy malware, for their illicit purposes.
Ransomware Groups Involved
Here below, we have mentioned all the ransomware groups that are involved in using this malware:-
- ViceSociety
- Rhysida
- GoldDupont
- FIN12
- 8BASE
- PLAY
- Hive
- BlackBasta
- TropicalScoprious (CUBA)
- RiddleSpider (Avaddon)
- WizardSpider (Conti, Ryuk)
- Egregor
- DarkSide
- Maze Team (Maze & IcedID)
SystemBC, The SWISS KNIFE
Coroxy infiltrates systems using diverse methods tailored to the user group, employing:-
- Reconnaissance
- Lateral movement
- Deploying SystemBC (often alongside CobaltStrike)
It’s also utilized in Spear Phishing campaigns, delivered via loaders or other malware for installation on victim systems.
SystemBC malware adapts its methods but maintains core tasks:-
Gather system info –> Establish persistence –> Create a Socks5 connection to the C&C server –> Transmit data –> Await attacker commands or malware launches
This backdoor enables attackers to operate from their infrastructure, and over time, numerous groups have used SystemBC.
SystemBC usage varies with each attacker’s access to the infrastructure. Studied samples show diverse executions yet share consistent core functions.
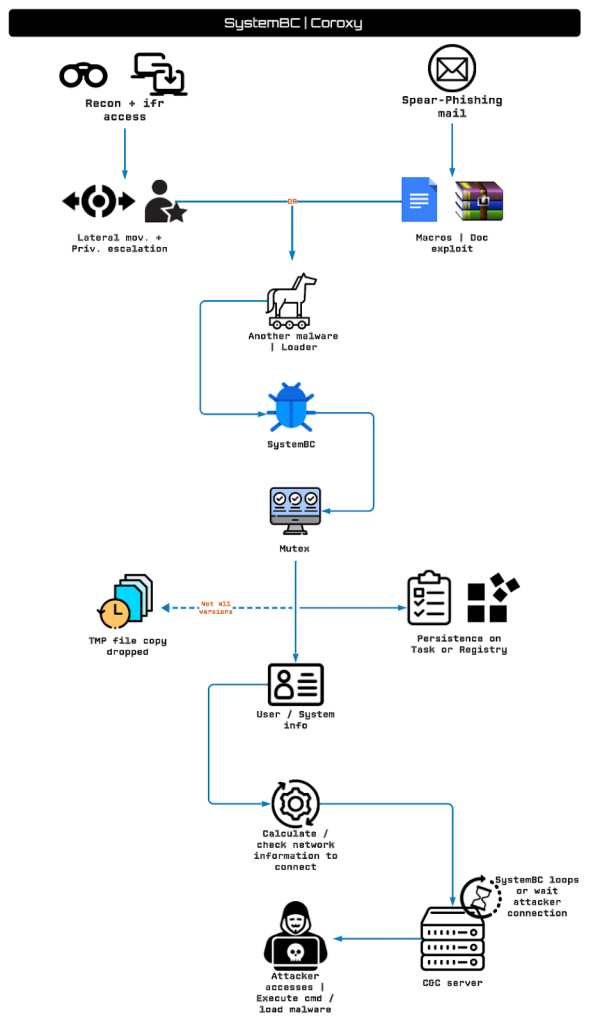
Usually, when an executable is run, a duplicate copy of SystemBC is made and persistence is established via tasks or registry entries.
Some samples may use a packer or need deobfuscation/extraction without a loader or malware.
Extracting from memory may be required, revealing identical copies in a temporary folder indicating malware duplication with dynamic filenames.
Coroxy employs a Mutex control in all examined samples that prevents multiple runs. It may generate a random string or deobfuscate a domain as a Mutex, adding complexity.
Samples establish persistence differently, as some create jobs or registry entries, often using PowerShell to execute SystemBC.
In certain versions, SystemBC launches a duplicate in the following paths:-
- ProgramData
- Roaming
- Temp
SystemBC detects a2guard, a handy anti-analysis move to spot antivirus or disruptive software. It captures process snapshots, using ProcessFirst and ProcessNext to hunt for the binary.
This grants persistence, process control, and info gathering, with deobfuscation and decryption for future network connections.
After pinpointing the connection location, SystemBC establishes it through a loop, usually targeting a known server and port, reads the report.
Though versions may differ slightly, the core behavior remains the same. However, the analyst found a focus on Coroxy’s relevance, with active discussions and inquiries in forums.
Besides this, the identified infrastructure allows OS access for around $350 to $300, payable through active cryptocurrency wallets.
IOCs
Hash:
- c96f8d4d1ee675c3cd1b1cf2670bb9bc2379a6b66f3029b2ffcfdd67c612c499
- 6f78256f20eb2b5594391095a341f8749395e7566fdd2ddd3a34a0db9bb9f871
- E81eb1aa5f7cc18edfc067fc6f3966c1ed561887910693fa88679d9b43258133
- 97ebef56e3fa3642d0395c00c25975e586089d26632e65422099a5107d375993
- ef71c960107ba5034c2989fd778e3fd72d4cdc044763aef2b4ce541a62c3466c
- 6E57D1FC4D14E7E7C2216085E41C393C9F117B0B5F8CE639AC78795D18DBA730
- 6b56f6f96b33d0acefd9488561ce4c0b4a1684daf5dde9cc81e56403871939c4
- F0073027076729CE94BD028E8F50F5CCB1F0184C91680E572580DB0110C87A82
- 3d1d747d644420a2bdc07207b29a0509531e22eb0b1eedcd052f85085bef6865
- c68035aabbe9b80ace209290aa28b8108cbb03a9d6a6301eb9a8d638db024ad0
- c926338972be5bdfdd89574f3dc2fe4d4f70fd4e24c1c6ac5d2439c7fcc50db5
Domain:
- payload[.]su
- mxstat215dm[.]xyz
- mxstex725dm[.]xyz
- zl0yy[.]ru
- r0ck3t[.]ru
IP (High confidence):
- 91[.]191[.]209[.]110
- 5[.]42[.]65[.]67
- 45[.]15[.]158[.]40
IP (Mid-Low confidence):
- 178[.]236[.]246[.]117
- 185[.]174[.]136[.]148
- 45[.]142[.]122[.]179
- 178[.]236[.]247[.]39
- 45[.]142[.]122[.]105
- 185[.]112[.]83[.]129
- 185[.]112[.]83[.]164
- 185[.]112[.]83[.]172
- 185[.]112[.]83[.]59
- 5[.]42[.]65[.]67
- 78[.]153[.]130[.]166
- 45[.]142[.]122[.]215
- 91[.]191[.]209[.]110
- 5[.]188[.]206[.]246

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory