IT Governance Ltd, the global provider of cyber security management solutions, has announced a value-add offer in March. Organisations that buy the No3 ISO27001 Comprehensive Toolkit before the end of March will receive the Cybersecurity Self Assessment Tool free, making double savings on resource and time.
The No3 ISO27001 Comprehensive Toolkit contains highly practical books, document templates and risk assessment tool, also providing a 100% return on investment. It helps organisations tackle cybersecurity issues quickly and efficiently, whilst considerably improving their cybersecurity defences.
The recent Symantec Threat Awareness Survey uncovered that over 50% of the 1,900 SME’s interviewed, thought that they were immune to cybercrime because they were too small.
However, Symantec’s report found that since 2010 40% of all attacks were on SME’s. Ross Walker, Symantec director of small business for Symantec UK, commented “hackers are going after ‘low hanging fruits’ these are the companies who are less security aware and do not have the proper defences in place”.
Alan Calder, CEO of IT Governance, says “The best way to build robust and effective cyber defences is by implementing ISO27001, the world’s cybersecurity standard. An ISO27001-compliant Information Security Management System (ISMS) promotes customer confidence, helps vendors win new business and improves organisational efficiency”.
The easiest way to implement an ISO27001-compliant ISMS, especially for SMEs, is with the No 3 Comprehensive ISMS ISO27001 Toolkit. It provides organisations with all the tools they will need for the implementation of an information security management system (ISMS).
The No 3 Comprehensive ISMS ISO27001 Toolkit includes copies of the three key standards (ISO27001, ISO27002 and ISO27005), the Risk Assessment Tool (vsRisk™), the Documentation Template Toolkit and manuals that describe in practical detail how each aspect of the ISMS should be tackled.
One user of the Toolkit said: “Using the templates was the only way that we could deliver a first edition ISMS in under six months. Our deliverable was a work in progress, but miles ahead of where they would have been without the templates”.
Organisations that buy the No 3 Comprehensive ISMS ISO27001 Toolkit before the end of March will receive the Cybersecurity Self Assessment Tool free. It enables any organisation to quickly assess and demonstrate which areas of the organisation are up to scratch and where more attention is required.
Organisations can purchase the ISO27001 Comprehensive Toolkit here!











![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=a3168449-b81f-45c3-8b23-5ed61d6b8845)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=1119f164-7e48-4ad2-b112-d80cd3808a1d)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=7df2ef1d-242f-4110-8903-59f134349e57)
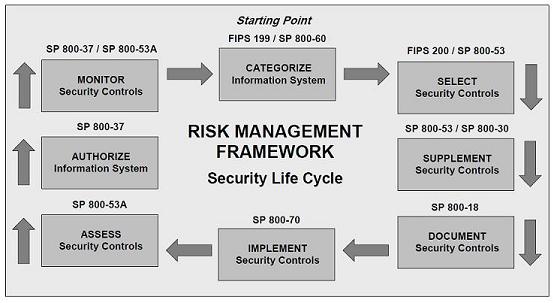
 The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. 


![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=2590b94c-4c68-4b01-a367-028d2bdde031)



