Mar 13 2021
The fire in the OVH datacenter also impacted APTs and cybercrime groups
OVH, one of the largest hosting providers in the world, has suffered this week a terrible fire that destroyed its data centers located in Strasbourg. The French plant in Strasbourg includes 4 data centers, SBG1, SBG2, SBG3, and SBG4 that were shut down due to the incident, and the fire started in SBG2 one.
The fire impacted the services of a large number of OVHs’ customers, for this reason the company urged them to implement their disaster recovery plans.
Nation-state groups were also impacted by the incident, Costin Raiu, the Director of the Global Research and Analysis Team (GReAT) at Kaspersky Lab, revealed that 36% of 140 OVH servers used by various threat actors as C2 servers went offline. The servers were used by cybercrime gangs and APT groups, including Iran-linked Charming Kitten and APT39 groups, the Bahamut cybercrime group, and the Vietnam-linked OceanLotus APT.
Of course, the incident only impacted a small portion of the command and control infrastructure used by multiple threat actors in the wild, almost any group leverages on multiple service providers and bulletproof hosting to increase the resilience of their C2 infrastructure to takedown operated by law enforcement agencies with the help of security firms.
“In the top of ISPs hosting Command and control infrastructure, OVH is in the 9th position, according to our tracking data. Overall, they are hosting less than 2% of all the C2s used by APTs and sophisticated crime groups, way behind other hosts such as, CHOOPA.” Raiu told to The Reg.
“I believe this unfortunate incident will have a minimal impact on these groups operations; I’m also taking into account that most sophisticated malware has several C2s configured, especially to avoid take-downs and other risks. We’re happy to see nobody was hurt in the fire and hope OVH and their customers manage to recover quickly from the disaster.”
The fire in the OVH datacenter also impacted APTs and cybercrime groups
Feb 16 2021
Data Obfuscation: An Image Is Worth a Thousand Lines of Malware
In this post, we are going to talk about MITRE ATT&CK® technique T1001 – Data Obfuscation. As the name indicates, this technique consists in making data, usually sent over Command and Control (C&C) communications, more difficult to detect and decode. There are countless ways to do that, but here we are going to focus on disguising payloads – which can simply be information, but also files written as malware or scripts – as images.
Why would someone do that? Mainly because every day lots of images are downloaded when a user is surfing the internet. Downloading an image-like file therefore blends perfectly into regular traffic and does not stand out for a network security control that, for instance, blocks the download of Windows binaries or PowerShell scripts, or does not look for malicious content in an image file. Since these files do not show up as executable, they can fly under the radar of an antivirus or endpoint detection and response (EDR) capability more easily.
Below we will show three examples of how to obfuscate data into image files, namely:
- Adding a JPEG header to the data;
- Appending the data to a JPEG image; and
- Embedding the data into a PNG image using Least Significant Byte (LSB) steganography.
Source: Data Obfuscation: An Image Is Worth a Thousand Lines of Malware
Oct 27 2020
Google Mending Another Crack in Widevine
For the second time in as many years, Google is working to fix a weakness in its Widevine digital rights management (DRM) technology used by online streaming sites like Disney, Hulu and Netflix to prevent their content from being pirated.
The latest cracks in Widevine concern the encryption technology’s protection for L3 streams, which is used for low-quality video and audio streams only. Google says the weakness does not affect L1 and L2 streams, which encompass more high-definition video and audio content.
“As code protection is always evolving to address new threats, we are currently working to update our Widevine software DRM with the latest advancements in code protection to address this issue,” Google said in a written statement provided to KrebsOnSecurity.
In January 2019, researcher David Buchanan tweeted about the L3 weakness he found, but didn’t release any proof-of-concept code that others could use to exploit it before Google fixed the problem.
Source: Google Mending Another Crack in Widevine
Sep 02 2020
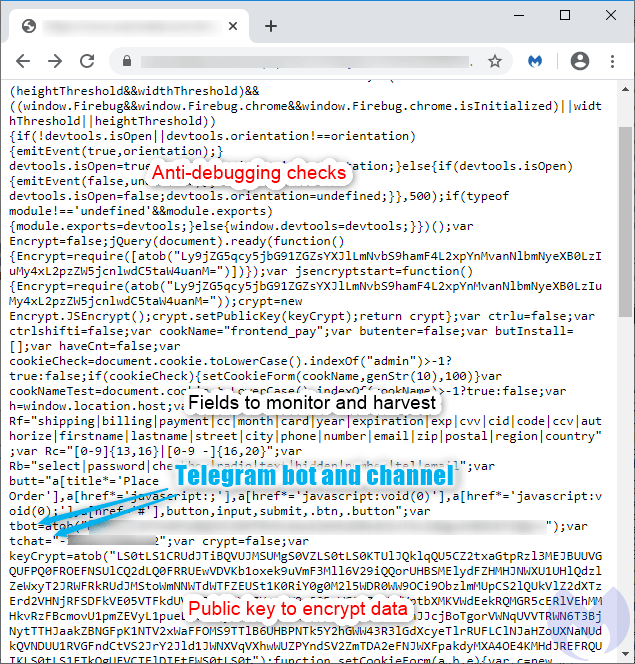
Hackers use e-skimmer that exfiltrates payment data via Telegram
Experts observed a new tactic adopted by Magecart groups, they used Telegram to exfiltrate stolen payment details from compromised websites
Source: Hackers use e-skimmer that exfiltrates payment data via Telegram
CISA Webinar: E-Skimming
httpv://www.youtube.com/watch?v=ngJwm8ydYNI
This Is How Easy It Is To Get Hacked | VICE on HBO
httpv://www.youtube.com/watch?v=G2_5rPbUDNA
Download a Security Risk Assessment Steps paper!
Security Risk assessment Quiz – Find Out How Your security risk assessment Stands Up!
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Subscribe to DISC InfoSec blog by Email
👉 Download a Virtual CISO (#vCISO) and Security Advisory Fact Sheet & Cybersecurity Cheat Sheet
Aug 26 2020
Safari Bug That Allows Stealing Data Disclosed After Apple Delays A Patch
Apple planned to release a fix for the Safari bug by Spring 2021, delaying it for one year. The bug allows stealing local data files.
Source: Safari Bug That Allows Stealing Data Disclosed After Apple Delays A Patch
Data Loss/Leak Prevention | Security Basics
httpv://www.youtube.com/watch?v=5CU9KYA-sz8
Aug 20 2020
5 Common Accidental Sources of Data Leaks
5 Common Accidental Sources of Data Leaks – Nightfall AI
How do bad actors gain access to a company’s data? Most of the time, well-meaning everyday people are the real source of data insecurity.
In cybersecurity and infosec, it’s common to assume that criminals are behind all data breaches and major security events. Bad actors are easy to blame for information leaks or account takeovers, because they’re the ones taking advantage of vulnerabilities in systems to worm their way in and cause massive damage. But how do they gain access in the first place? Most of the time, well-meaning everyday people are the real source of data insecurity.
A study of data from 2016 and 2017 indicated that 92% of security data incidents and 84% of confirmed data breaches were unintentional or inadvertent. Accidental data loss continues to plague IT teams, especially as more organizations are rapidly moving to the cloud. While it’s important to prioritize action against outside threats, make sure to include a strategy to minimize the damage from accidental breaches as well.
This list of five common sources of accidental data leaks will help you identify the problems that could be lurking in your systems, apps, and platforms. Use these examples to prepare tighter security controls and keep internal problems from becoming major issues across your entire organization.
Source: 5 Common Accidental Sources of Data Leaks – Nightfall AI
Jul 09 2020
15 billion credentials available in the cybercrime marketplaces
More than 15 billion username and passwords are available on cybercrime marketplaces, including over 5 billion unique credentials, states the experts.
Source: 15 billion credentials available in the cybercrime marketplaces
Exploring the Dark Web
httpv://www.youtube.com/watch?v=BN1NU0ivzj8
Explore the subject of Cyber Attack
Download a Security Risk Assessment Steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Jun 23 2020
Republicans push bill requiring tech companies to help access encrypted data
The proposed legislation is Congress’ latest attempt to weaken encryption from tech giants.
Source: Republicans push bill requiring tech companies to help access encrypted data
Jun 23 2020
A daily average of 80,000 printers exposed online via IPP
Experts found tens of thousands of printers that are exposed online that are leaking device names, organization names, WiFi SSIDs, and other info.
Source: A daily average of 80,000 printers exposed online via IPP
Exploiting Network Printers
httpv://www.youtube.com/watch?v=DwKzSO4yA_s
How To Hack A Printer And See All Documents Printed
httpv://www.youtube.com/watch?v=6JFP_gUIZZY
Download a Security Risk Assessment steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
Jun 18 2020
Facebook sues developer over alleged data scraping abuse
The lawsuit alleges that a data scraper took login credentials from about 5,500 people and then harvested phone numbers of their friends.
Source: Facebook sues developer over alleged data scraping abuse
What Is Web/Data Scrapping ? How To Scrap Large Data From A Website
httpv://www.youtube.com/watch?v=bp73TqGcY9c
Would like to know more on InfoSec Awareness…
Download a Security Risk Assessment steps paper!
Subscribe to DISC InfoSec blog by Email
May 31 2020
How hoteliers can mitigate data breaches
As hackers shift tactics, business owners can take steps to prevent attacks and minimize damage.
Source: How hoteliers can mitigate data breaches
The 5 Most Dangerous New Attack Techniques and How to Counter Them
httpv://www.youtube.com/watch?v=xz7IFVJf3Lk
Data Breaches: Crisis and Opportunity
Download a Security Risk Assessment Checklist paper!
Subscribe to DISC InfoSec blog by Email
May 25 2020
Hacker extorts online shops, sells databases if ransom not paid
More than two dozen SQL databases stolen from online shops in various countries are being offered for sale on a public website. In total, the seller provides over 1.5 million rows of records but the damage is likely much larger.
Source: Hacker extorts online shops, sells databases if ransom not paid
More than two dozen SQL databases stolen from online shops in various countries are being offered for sale on a public website. In total, the seller provides over 1.5 million rows of records but the amount of stolen data is much larger.
The attacker is hacking into insecure servers that are reachable over the public web, copies the databases, and leaves a note asking for a ransom in return of the stolen data.
Money made
Victims have 10 days to pay BTC 0.06 ($525 at current price) a wallet provided in the ransom note, else the hacker makes the database public or uses it as they please.
Hacked! What to do with an extortion email
httpv://www.youtube.com/watch?v=CQS-fSsIQbo
Bitcoin Email Blackmail Ransom Scam
httpv://www.youtube.com/watch?v=H40C7Hbpdqw
Download a CyberAware cheat sheet
Dec 13 2019
Data Security Solutions for Fintech Startups

By Ena Kadribasic on Security
The fintech sector has brought consumers an endless stream of modern offerings that have enabled them to ditch several outdated banking and lending products.
Companies now have advanced B2B payment solutions at their fingertips, and online financial solutions have never been more convenient – largely thanks to the progress made by fintech startups.
But, despite being on the cutting edge of digital financial products, young fintech companies are at a disadvantage in a wildly important arena: data security.
With limited resources, growing compliance regulations around the world, and a constantly-evolving list of increasingly dangerous cyber threats, fintech startups face a uniquely difficult uphill battle.
And, with data breaches continuing to leer as an ever-present security threat, fintech firms are turning to new and advanced approaches to data privacy.
But, first, what do we mean when we talk about data security for startups?
Source: Data Security Solutions for Fintech Startups
Subscribe to DISC InfoSec blog by Email
Oct 16 2019
CyberSecurity for Digital Operations
This report examines the general state of security within business today, exploring the hurdles that are preventing companies from an ideal security posture and suggesting the steps that can lead to improved security in the digital economy.
As the technology industry enters the next phase of maturity, there are more questions about the implications of emerging trends operating on a global scale. Aside from social impact ramification, utmost reliance on digital data and the sweeping collection of personal information are highlighting the critical nature of information security and privacy.
Digital Transformation: From AI and IoT to Cloud, Blockchain, and Cybersecurity | MIT PE
httpv://www.youtube.com/watch?v=NwwazhND9BA
Inside the CenturyLink Security Operations Center: Securing Your Digital Business
httpv://www.youtube.com/watch?v=_UyhYPOnNcY
The Convergence (and Divergence) of IT and OT Cyber Security
Subscribe to DISC InfoSec blog by Email
Aug 15 2019
Data Loss Prevention: Protect Yourself, Your Family, and Your Business
photo courtesy of Unsplash
By Jasmine Dyoco
Another day, another data breach. Lately, it seems like we can’t go more than a few days without hearing about another cyber attack. Data breaches have recently occurred at health insurance providers like Anthem, banks like Capital One, and even the Equifax credit bureau. If there’s anything these recent hacks have shown us, it’s that no industry is safe.
Social Security numbers, credit cards, and passwords are just some of the types of compromised data. Given the number of recent attacks, Bloomberg reports that some cybersecurity professionals now make millions of dollars per year.
Massive amounts of information have been stolen. According to The Week, “virtually everyone in the U.S. has been affected by a data breach in some way — even those who never go online.” If you’re worried a hacker might have your data, here’s how you can protect yourself and your family:
Malware and Viruses
Malware and computer viruses are common ways that scammers get sensitive information. Contrary to popular belief, Macs (and smartphones and tablets) can get viruses. Whether you use Mac, Windows, Linux, or an iPad, protecting your computer against viruses also protects your information.
According to Secure Data Recovery, proactive actions can help keep hackers and viruses from accessing your data. Use strong passwords that are hard to guess. A sentence or phrase is stronger than a single word, for example. You should also install a firewall and antivirus software. Save backups of your files to a device like an external hard drive. Alternatively, you could also save data to the cloud using Google Drive or similar.
Security and Compliance
Cyber threats are continually evolving. By having an information security (InfoSec) plan in place, you can protect data from falling into the wrong hands. InfoSec helps organizations maintain confidentiality while complying with industry regulations. DISC help the organization to succeed in infosec and Privacy program by building and assessing Information Security Management System (ISMS) and Privacy Information Management System (PIMS) based on various standards and regulations.
For instance, Deura Information Security Consulting (DISC) can perform a risk assessment to identify the security risks. Based on those gaps, they’ll help you create a “safe, secure, and resilient cyber environment.” Additionally, they’ll help your organization comply with regional cyber laws. Those laws include Europe’s General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
Protect Your Teens
Nobody is safe from online attacks. Unfortunately, that includes children and teenagers. Some scams specifically target teens and young adults. One example is phishing, which tricks teens into revealing their social media passwords. Teens are also susceptible to phishing scams that include “urgent” subject lines. These scams often trick people into clicking a link to avoid missing a once-in-a-lifetime opportunity.
To protect your children, the InfoSec Institute advises telling them to keep their login information private and to never click on social media links via email. Teach them red flags, like email scams claiming they’ve won money or website URLs that have misspellings or extra letters. Your whole family can learn what to look for by practicing with a phishing simulator.
Credit Freezes and Monitoring
Many people believe cybercriminals only steal money. The reality is that many of them are interested in stealing data, identities, or intellectual property. In the event that you do experience data loss, whether due to a virus, malware, or online scam, it’s essential to take action.
According to the IRS, you should report identity theft to the FTC, your bank, and each of the credit bureaus. You might want to freeze your credit and place a one-year alert on your credit report. Credit monitoring companies can help you protect your credit score by alerting you of any fraudulent activity. If you follow the tips listed above, you can recover your data and protect yourself from future attacks.
How to report and protect yourself from credit card fraud
How to prevent credit card fraud amid coronavirus pandemic
The Secret to Cybersecurity: A Simple Plan to Protect Your Family and Business from Cybercrime
May 20 2019
Millions of Instagram influencers had their private contact data scraped and exposed
Millions of Instagram influencers had their private contact data scraped and exposed
A massive database containing contact information of millions of Instagram influencers, celebrities and brand accounts has been found online. The database, hosted by Amazon Web Services, was left exposed and without a password allowing anyone to look inside. At the time of writing, the database had over 49 million records — but was growing by […]
Source: Millions of Instagram influencers had their private contact data scraped and exposed – TechCrunch
May 06 2019
Unsecured SkyMed Database Exposed PII Data Of 137K Individuals
Unsecured SkyMed Database Exposed PII Data Of 137K Individuals
Reportedly, the unsecured SkyMed database exposed huge records having medical and personal information of US citizens online.
Source: Unsecured SkyMed Database Exposed PII Data Of 137K Individuals
ISO/IEC 27018:2014, 1st Edition: Information technology – Security techniques – Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
NIST Special Publication 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
« Previous Page — Next Page »