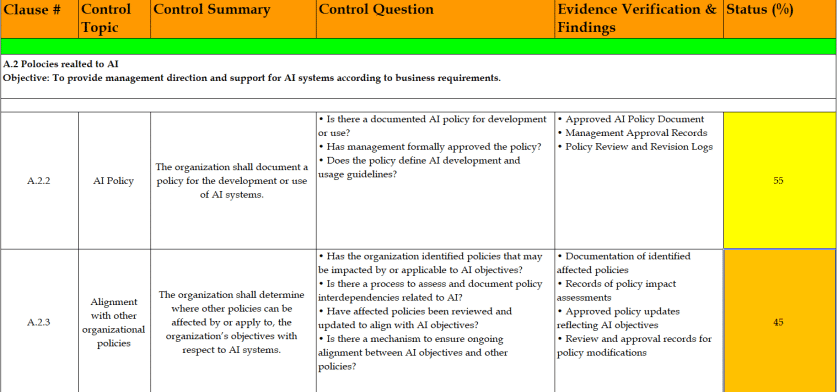
A recent Cisco report highlights a critical issue in the rapid adoption of artificial intelligence (AI) technologies by enterprises: the growing phenomenon of “AI infrastructure debt.” This term refers to the accumulation of technical gaps and delays that arise when organizations attempt to deploy AI on systems not originally designed to support such advanced workloads. As companies rush to integrate AI, many are discovering that their existing infrastructure is ill-equipped to handle the increased demands, leading to friction, escalating costs, and heightened security vulnerabilities.
The study reveals that while a majority of organizations are accelerating their AI initiatives, a significant number lack the confidence that their systems can scale appropriately to meet the demands of AI workloads. Security concerns are particularly pronounced, with many companies admitting that their current systems are not adequately protected against potential AI-related threats. Weaknesses in data protection, access control, and monitoring tools are prevalent, and traditional security measures that once safeguarded applications and users may not extend to autonomous AI systems capable of making independent decisions and taking actions.
A notable aspect of the report is the emphasis on “agentic AI”—systems that can perform tasks, communicate with other software, and make operational decisions without constant human supervision. While these autonomous agents offer significant operational efficiencies, they also introduce new attack surfaces. If such agents are misconfigured or compromised, they can propagate issues across interconnected systems, amplifying the potential impact of security breaches. Alarmingly, many organizations have yet to establish comprehensive plans for controlling or monitoring these agents, and few have strategies for human oversight once these systems begin to manage critical business operations.
Even before the widespread deployment of agentic AI, companies are encountering foundational challenges. Rising computational costs, limited data integration capabilities, and network strain are common obstacles. Many organizations lack centralized data repositories or reliable infrastructure necessary for large-scale AI implementations. Furthermore, security measures such as encryption, access control, and tamper detection are inconsistently applied, often treated as separate add-ons rather than being integrated into the core infrastructure. This fragmented approach complicates the identification and resolution of issues, making it more difficult to detect and contain problems promptly.
The concept of AI infrastructure debt underscores the gradual accumulation of these technical deficiencies. Initially, what may appear as minor gaps in computing resources or data management can evolve into significant weaknesses that hinder growth and expose organizations to security risks. If left unaddressed, this debt can impede innovation and erode trust in AI systems. Each new AI model, dataset, and integration point introduces potential vulnerabilities, and without consistent investment in infrastructure, it becomes increasingly challenging to understand where sensitive information resides and how it is protected.
Conversely, organizations that proactively address these infrastructure gaps are better positioned to reap the benefits of AI. The report identifies a group of “Pacesetters”—companies that have integrated AI readiness into their long-term strategies by building robust infrastructures and embedding security measures from the outset. These organizations report measurable gains in profitability, productivity, and innovation. Their disciplined approach to modernizing infrastructure and maintaining strong governance frameworks provides them with the flexibility to scale operations and respond to emerging threats effectively.
In conclusion, the Cisco report emphasizes that the value derived from AI is heavily contingent upon the strength and preparedness of the underlying systems that support it. For most enterprises, the primary obstacle is not the technology itself but the readiness to manage it securely and at scale. As AI continues to evolve, organizations that plan, modernize, and embed security early will be better equipped to navigate the complexities of this transformative technology. Those that delay addressing infrastructure debt may find themselves facing escalating technical and financial challenges in the future.
Opinion: The concept of AI infrastructure debt serves as a crucial reminder for organizations to adopt a proactive approach in preparing their systems for AI integration. Neglecting to modernize infrastructure and implement comprehensive security measures can lead to significant vulnerabilities and hinder the potential benefits of AI. By prioritizing infrastructure readiness and security, companies can position themselves to leverage AI technologies effectively and sustainably.
Everyone wants AI, but few are ready to defend it
Data for AI: Data Infrastructure for Machine Intelligence
Click the ISO 42001 Awareness Quiz — it will open in your browser in full-screen mode
Protect your AI systems — make compliance predictable.
Expert ISO-42001 readiness for small & mid-size orgs. Get a AI Risk vCISO-grade program without the full-time cost.
Secure Your Business. Simplify Compliance. Gain Peace of Mind
Check out our earlier posts on AI-related topics: AI topic
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security