There is an ongoing battle between the e-commerce giant and dubious sellers, worldwide, who wish to hamstring competitors and gain an edge by generating fake reviews for their products.
This can include paying individuals to leave a glowing review or by offering free items in return for positive, public feedback.
How they operate and stay under Amazon’s radar varies, but an open ElasticSearch server has exposed some of the inner workings of these schemes.
On Thursday, Safety Detectives researchers revealed that the server, public and online, contained 7GB of data and over 13 million records appearing to be linked to a widespread fake review scam.
It is not known who owns the server but there are indicators that the organization may originate from China due to messages written in Chinese, leaked during the incident.
The database contained records involving roughly 200,000 – 250,000 users and Amazon marketplace vendors including user names, email addresses, PayPal addresses, links to Amazon profiles, and both WhatsApp and Telegram numbers, as well as records of direct messages between customers happy to provide fake reviews and traders willing to compensate them.
According to the team, the leak may implicate “more than 200,000 people in unethical activities.”
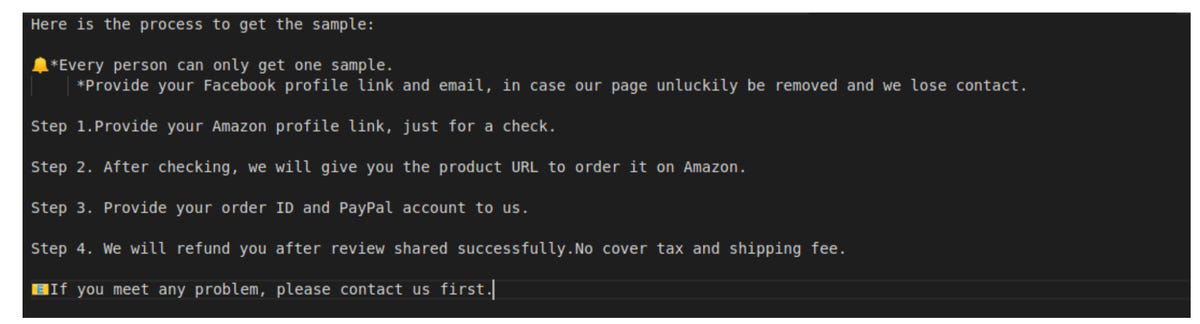
The database, and messages contained therein, revealed the tactics used by dubious sellers. One method is whereby vendors send a customer a link to the items or products they want 5-star reviews for, and the customer will then make a purchase.
Several days after, the customer will leave a positive review and will send a message to the vendor, leading to payment via PayPal — which may be a ‘refund,’ while the item is kept for free.
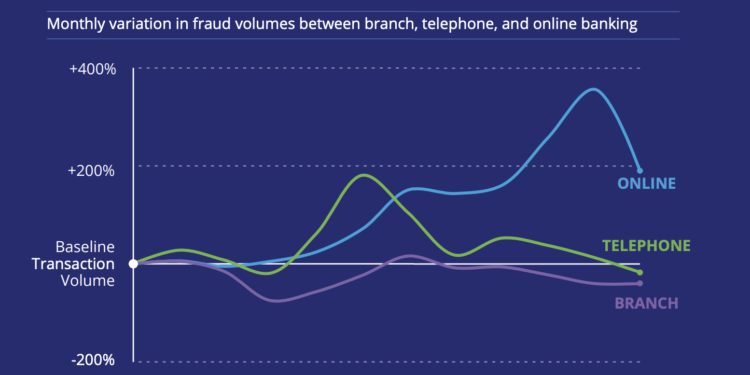
As refund payments are kept away from the Amazon platform, it is more difficult to detect fake, paid reviews.
Data leak implicates over 200,000 people in Amazon fake product review scam



![Types Of Online & Banking Frauds And How To Be Safe ?: Online Banking Scams and tips to be safe by [Sayed Mahboob Hasan Hashmi]](https://m.media-amazon.com/images/I/4112Eh7SAHL.jpg)