AI Has Joined the Attacker Team
The threat landscape is entering a new phase with the rise of AI-assisted malware. What once required well-funded teams and months of development can now be created by a single individual in days using AI. This dramatically lowers the barrier to entry for advanced cyberattacks.
This shift means attackers can scale faster, adapt quicker, and deliver higher-quality attacks with fewer resources. As a result, smaller and mid-sized organizations are no longer “too small to matter” and are increasingly attractive targets.
Emerging malware frameworks are more modular, stealthy, and cloud-aware, designed to persist, evade detection, and blend into modern IT environments. Traditional signature-based defenses and slow response models are struggling to keep pace with this speed and sophistication.
Critically, this is no longer just a technical problem — it is a business risk. AI-enabled attacks increase the likelihood of operational disruption, regulatory exposure, financial loss, and reputational damage, often faster than organizations can react.
Organizations that will remain resilient are not those chasing the latest tools, but those making strategic security decisions. This includes treating cybersecurity as a core element of business resilience, not an IT afterthought.
Key priorities include moving toward Zero Trust and behavior-based detection, maintaining strong asset visibility and patch hygiene, investing in practical security awareness, and establishing clear governance around internal AI usage.
The cybersecurity landscape is undergoing a fundamental shift with the emergence of a new class of malware that is largely created using artificial intelligence (AI) rather than traditional development teams. Recent reporting shows that advanced malware frameworks once requiring months of collaborative effort can now be developed in days with AI’s help.
The most prominent example prompting this concern is the discovery of the VoidLink malware framework — an AI-driven, cloud-native Linux malware platform uncovered by security researchers. Rather than being a simple script or proof-of-concept, VoidLink appears to be a full, modular framework with sophisticated stealth and persistence capabilities.
What makes this remarkable isn’t just the malware itself, but how it was developed: evidence points to a single individual using AI tools to generate and assemble most of the code, something that previously would have required a well-coordinated team of experts.
This capability accelerates threat development dramatically. Where malware used to take months to design, code, test, iterate, and refine, AI assistance can collapse that timeline to days or weeks, enabling adversaries with limited personnel and resources to produce highly capable threats.
The practical implications are significant. Advanced malware frameworks like VoidLink are being engineered to operate stealthily within cloud and container environments, adapt to target systems, evade detection, and maintain long-term footholds. They’re not throwaway tools — they’re designed for persistent, strategic compromise.
This isn’t an abstract future problem. Already, there are real examples of AI-assisted malware research showing how AI can be used to create more evasive and adaptable malicious code — from polymorphic ransomware that sidesteps detection to automated worms that spread faster than defenders can respond.
The rise of AI-generated malware fundamentally challenges traditional defenses. Signature-based detection, static analysis, and manual response processes struggle when threats are both novel and rapidly evolving. The attack surface expands when bad actors leverage the same AI innovation that defenders use.
For security leaders, this means rethinking strategies: investing in behavior-based detection, threat hunting, cloud-native security controls, and real-time monitoring rather than relying solely on legacy defenses. Organizations must assume that future threats may be authored as much by machines as by humans.
In my view, this transition marks one of the first true inflection points in cyber risk: AI has joined the attacker team not just as a helper, but as a core part of the offensive playbook. This amplifies both the pace and quality of attacks and underscores the urgency of evolving our defensive posture from reactive to anticipatory. We’re not just defending against more attacks — we’re defending against self-evolving, machine-assisted adversaries.
Perspective:
AI has permanently altered the economics of cybercrime. The question for leadership is no longer “Are we secure today?” but “Are we adapting fast enough for what’s already here?” Organizations that fail to evolve their security strategy at the speed of AI will find themselves defending yesterday’s risks against tomorrow’s attackers.

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
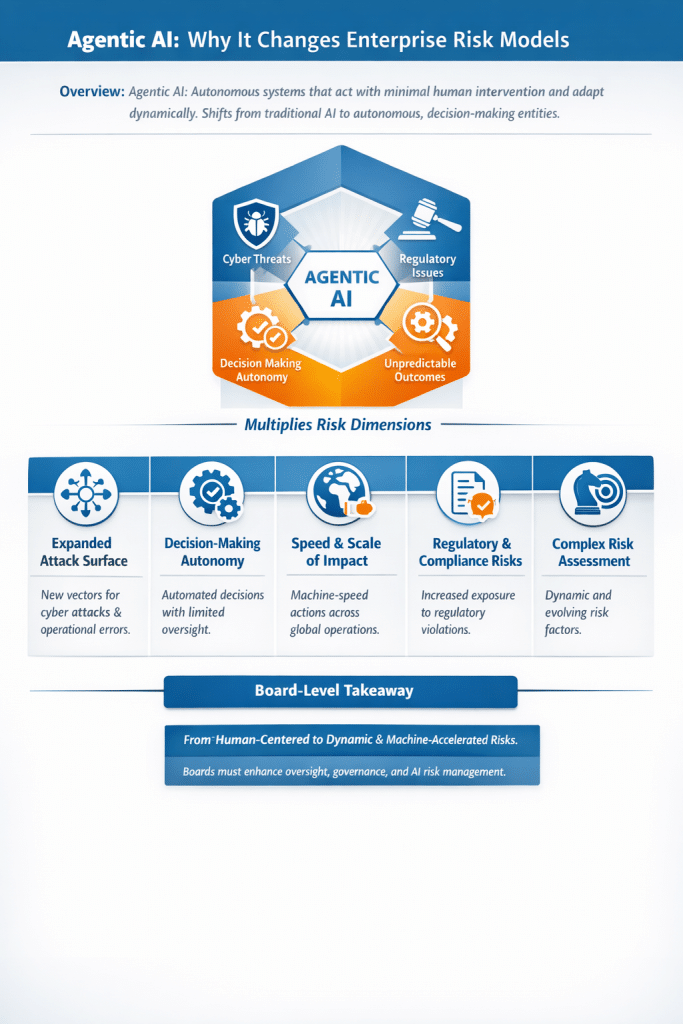
- AI Agents and the New Cybersecurity Frontier: Understanding the 7 Major Attack Surfaces
- Understanding AI/LLM Application Attack Vectors and How to Defend Against Them
- AI Governance Assessment for ISO 42001 Readiness
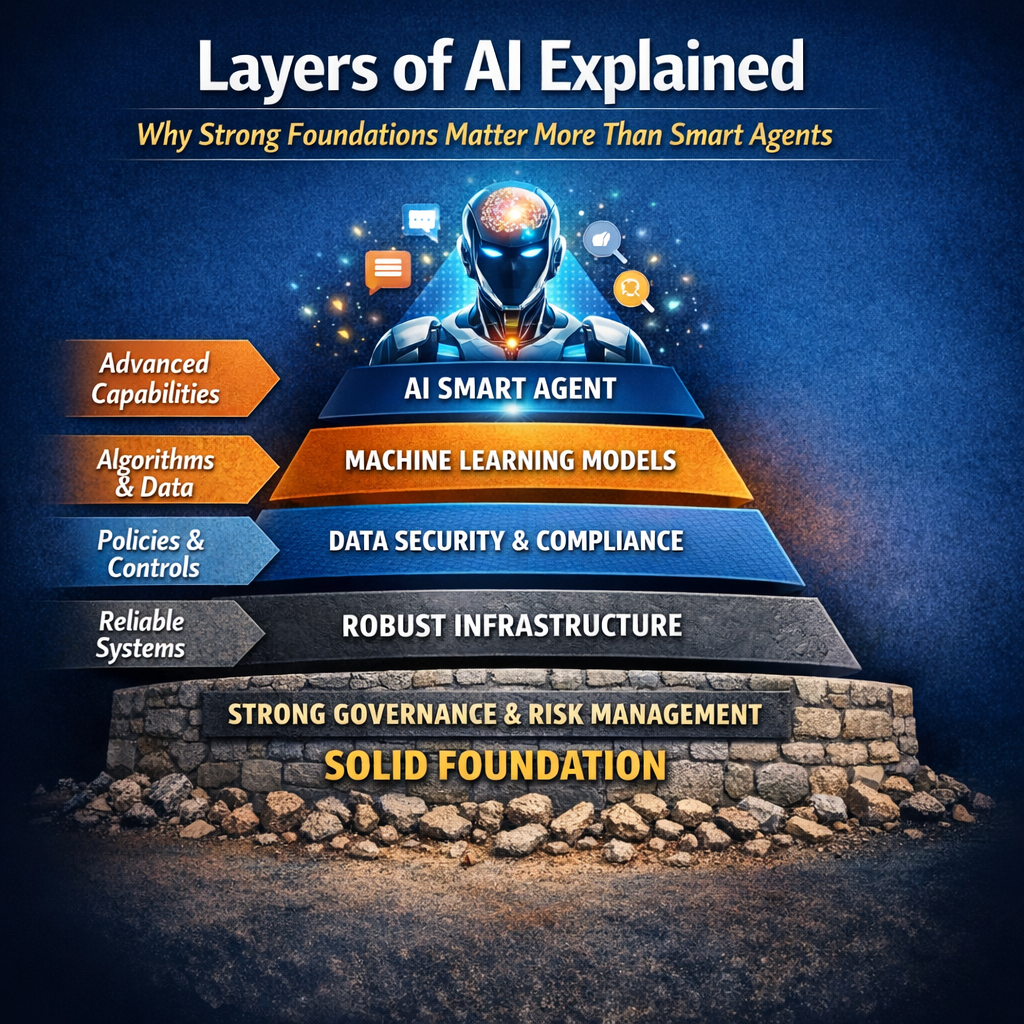
- Beyond ChatGPT: The 9 Layers of AI Transforming Business from Analytics to Autonomous Agents
- CMMC Level 2 Third-Party Assessment: What It Is, Why It Matters, and What to Expect