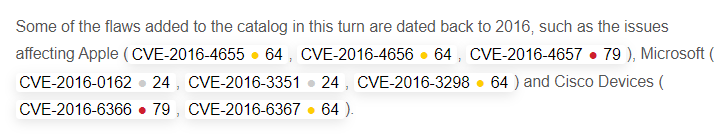
Researchers uncovered 3.6M accessible MySQL servers worldwide that represent a potential attack surface for their owners.
Researchers from Shadow Server scanned the internet for publicly accessible MySQL server instances on port 3306/TCP and uncovered 3.6M installs worldwide responding to their queries.
These publicly accessible MySQL server instances represent a potential attack surface for their owners.
“These are instances that respond to our MySQL connection request with a Server Greeting. Surprisingly to us, we found around 2.3M IPv4 addresses responding with such a greeting to our queries. Even more surprisingly, we found over 1.3M IPv6 devices responding as well (though mostly associated with a single Autonomous System).” states the report published by the researchers.
Most of the accessible IPv4 MySQL servers are in the United States (740.1K), China (296.3K), Poland (207.8K) and Germany (174.9K).

Accessible IPv4 MySQL servers
Most of the accessible IPv6 MySQL servers are in the United States (460.8K), Netherlands (296.3K), Singapore (218.2K) and Germany (173.7K).
Researchers recommend admins follow the MySQL 5.7 Secure Deployment Guide and MySQL 8.0 Secure Deployment Guide for the deployment of their servers.
“It is unlikely that you need to have your MySQL server allowing for external connections from the Internet (and thus a possible external attack surface). If you do receive a report on your network/constituency take action to filter out traffic to your MySQL instance and make sure to implement authentication on the server.” concludes the report.
The researchers shared data on the accessible MySQL instances in the Accessible MySQL Server Report.
Over 3.6 million MySQL servers found exposed on the Internet
PHP & MySQL: Server-side Web Development










![CYBERSECURITY AND INFRASTRUCTURE SECURITY AGENCY: Actions Needed to Ensure Organizational Changes Result in More Effective Cybersecurity for Our Nation by [United States Government Accountability Office]](https://m.media-amazon.com/images/I/51FIzAXr-CL._SX260_.jpg)






