https://www.crowdstrike.com/blog/devsecops-tips-to-develop-better-safer-apps/
According to the CrowdStrike 2023 Global Threat Report, there was a 95% increase in cloud exploits in 2022, with a three-fold increase in cases involving cloud-conscious threat actors. The cloud is rapidly becoming a major battleground for cyberattacks — and the cost of a breach has never been higher. The estimated average cost of a breach impacting multi-cloud environments is more than $4.75 million USD in 2023.1 The acceleration of cloud-focused threat activity and its effects has made security a key priority across organizations.
Security in the Cloud Is a Shared Responsibility
Security teams are accountable for protecting against risks, but they cannot be the only ones. Each team must try to communicate why their part of the development lifecycle is important to the other teams in the pipeline. With the growth of cloud-native applications and the demand for faster application delivery or continuous integration/continuous delivery (CI/CD), the use of containers is increasing widely. As businesses adopt containerized and serverless technologies and cloud-based services, more complex security issues arise.
Application developers have a tricky balance to maintain between speed and security. In DevOps, security used to be an issue addressed after development — but that’s changing. Now, developers who previously had to code right up to the last minute — leaving almost no time to find and fix vulnerabilities — are using tools like Infrastructure as code (IaC) scanning to validate they have fewer security vulnerabilities before they move to the next phase of development.
When security is considered at every step in the pipeline, it ensures developers find and address issues early on and it streamlines the development process. DevSecOps helps developers find and remediate vulnerabilities earlier in the app development process. Vulnerabilities discovered and addressed during the development process are less expensive and faster to fix. By automating testing, remediation and delivery, DevSecOps ensures stronger software security without slowing development cycles. The goal is to make security a part of the software development workflow, instead of having to address more issues during runtime.
5 Tips to Develop Apps with Security and Efficiency
1. Automate security reviews and testing. Every DevSecOps pipeline should utilize a combination or variation of tools and features like those listed below. A good automated and unified solution will provide broad visibility and address those issues as they arise, while alerting, enforcing compliance and providing customized reports with relevant insights for the DevOps and security teams.
- SAST: Static application security testing to detect insecure code before it’s used (tools like GitHub, GitGuardian and Snyk, to name a few)
- SCA: Software composition analysis to detect library vulnerabilities before building (tools like GitHub and GitLab)
- CSA: Container scanning analysis to detect Operating System Library vulnerabilities and mitigate risk (tools like CrowdStrike Falcon® Cloud Security and GitLab)
Figure 1. Dynamic container analysis in the Falcon platform (click to enlarge)
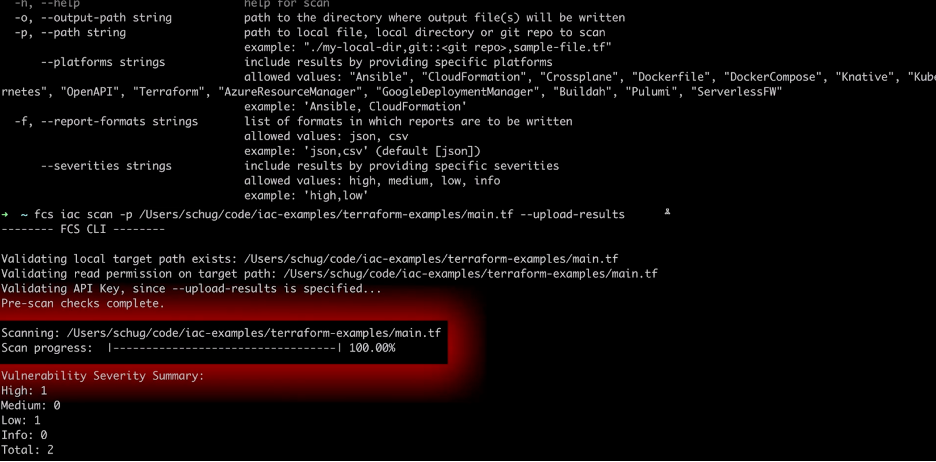
- IaC scanning: Infrastructure-as-code scanning to detect vulnerabilities in infrastructure (tools like Falcon Cloud Security and GitLab)
Figure 2. Falcon infrastructure-as-code (IaC) scanning (click to enlarge)
- ASPM: Application security posture management to detect application vulnerabilities and risks once deployed (such as Falcon Cloud Security)
Figure 3. Architecture view of apps, services, APIs and more in Falcon (click to enlarge)
2. Integrate with developer toolchains. Streamline and consolidate your toolchain so developers and security teams can focus their attention on a single interface and source of truth. The tighter the integration between security and app development, the earlier threats can be identified, and the faster delivery can be accelerated. By seamlessly integrating with Jenkins, Bamboo, GitLab and others, Falcon Cloud Security allows DevOps teams to respond to and remediate incidents faster within the toolsets they already use.
3. Share security knowledge among teams. DevSecOps is a journey enabled by technology, but a process that starts with people. Your DevSecOps team should share lessons learned and mitigation steps after resolving the compromise. Some organizations even assign a security champion who helps introduce this sense of responsibility of security within the team. Be prepared to get your teams on board before changing the process, and ensure everyone understands the benefits of DevSecOps. Make security testing part of your project kickoffs and charters, and empower your teams with training, education and tools to make their jobs easier.
4. Measure your security posture. Identify the software development pain points and security risks, create a plan that works well for your organization and your team, and drive execution. Make sure to track and measure results such as the time lost in dealing with vulnerabilities after code is merged. Then, look for patterns in the type or cause of those vulnerabilities, and make adjustments to detect and address them earlier. This introduces a shared plan with integration into the build and production phases. CrowdStrike offers a free comprehensive Cloud Security Risk Review and services to help you plan, execute and measure your plan.
5. “Shift right” as well as “shift left.” Detection doesn’t always guarantee security. Shifting right and knowing how secure your applications and APIs are in production is just as important. By leveraging ASPM to uncover potential vulnerabilities in the application code once they are up and deployed, teams can find potential exposure in their application code that could allow backdoor access to other critical data and systems.
The bottom line is that while security and development used to be separate, the lines are now blurring to a point where security is becoming more and more integrated with the day-to-day job of developers. The benefit is that the modern practice brings together teams across the company to a common understanding, which then drives business growth. DevSecOps requires teams to collaborate and enables the organization to deliver safer applications to customers without compromising security.
How CrowdStrike Powers Your DevSecOps Journey
Security is not meant to be a red light on the road to your business goals or slow down your software development. It is meant to enable you to reach those goals safely with minimal risk. Falcon Cloud Security empowers DevSecOps teams to “shift left” in the application security paradigm, with tools including Infrastructure-as-Code Scanning, Image Assessment, and Kubernetes Admission Controller, all designed to ensure applications are secure earlier in application development and deployment.
CrowdStrike Falcon Cloud Security lets DevOps and security teams join forces to build applications securely before deployment, monitor they are compliant once deployed, and ensure the code is secure during runtime using ASPM. With ASPM in a unified interface that’s easy to visualize and understand, customers can “shift right” to reduce risk and stop breaches from applications that are already deployed.
The DevSecOps Playbook: Deliver Continuous Security at Speed
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory