By Jeff James : Twitter at @jeffjames3
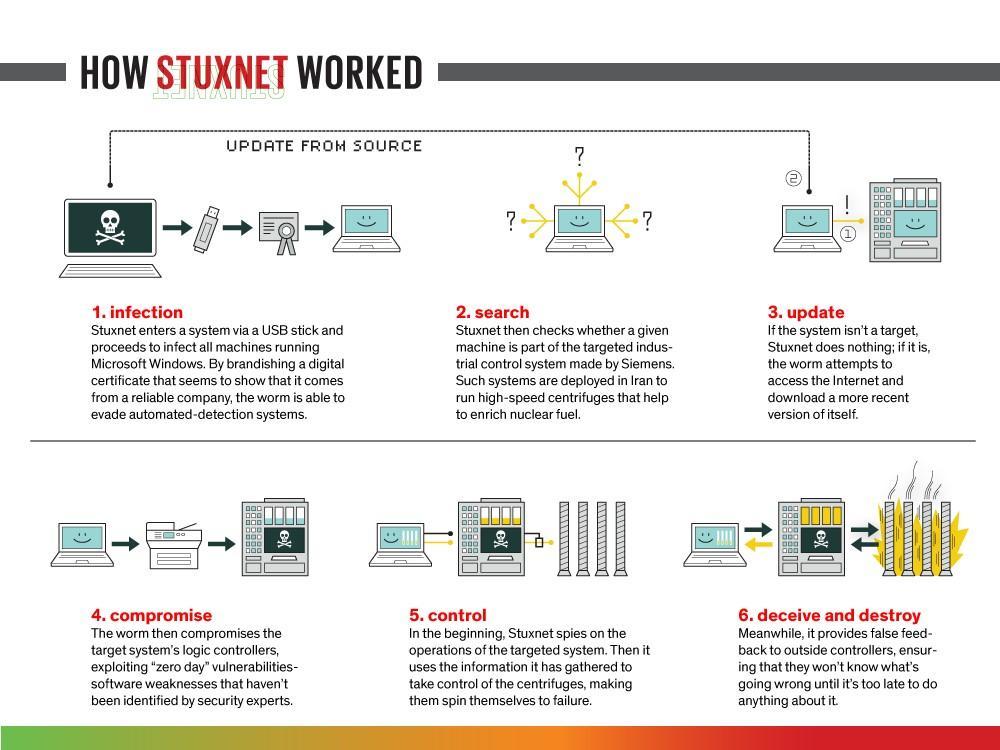
In June 2010, security experts, analysts, and software providers were warning IT managers about Stuxnet, a new computer worm that was spreading rapidly over the internet. Stuxnet was distributed by Windows machines, and the intent of the worm wasn’t immediately clear. After a few months it was revealed that the vast majority of Stuxnet infections were in Iran, and Stuxnet seemed to have been specifically targeting the Siemens industrial control equipment used in the Iranian nuclear program.
German security expert Ralph Langner was interviewed by NPR reporter Tom Gjelten earlier this year about Stuxnet, and Gjelten reported that Langner told him that the worm was so complex and sophisticated that it was “almost alien in design” and believed that only the United States had the resources required to create Stuxnet and orchestrate the attack. As more details emerged, it became clear that Stuxnet was likely developed by either Israeli or American intelligence agencies in an attempt to impede Iran’s nuclear program.
Both Israeli and American security officials have sidestepped questions about their involvement, but Gary Samore, White House Coordinator for Arms Control and Weapons of Mass Destruction, stated at a December 2010 conference on Iran that “we’re glad they [the Iranians] are having trouble with their centrifuge machine and that we – the US and its allies – are doing everything we can to make sure that we complicate matters for them.” [Source: NPR’s Need to Know]
Now security researchers from Symantec have revealed that they’ve discovered a new Stuxnet-like worm called W32.Duqu that shares much of the same code with Stuxnet. Symantec’s Security Research blog posted details about Duqu yesterday:
“Duqu shares a great deal of code with Stuxnet; however, the payload is completely different. Instead of a payload designed to sabotage an industrial control system, the payload has been replaced with general remote access capabilities. The creators of Duqu had access to the source code of Stuxnet, not just the Stuxnet binaries. The attackers intend to use this capability to gather intelligence from a private entity to aid future attacks on a third party. While suspected, no similar precursor files have been recovered that predate the Stuxnet attacks.
According to Symantec, Duqu also functions as a keylogger designed to “capture information such as keystrokes and system information” but lacks the specific code related to “industrial control systems, exploits, or self-replication.” Symantec’s research team believes that Duqu is collecting information for a possible future attack, and seem to point the finger at the original creators of Stuxnet, since the creators of Duqu seem to have direct access to Stuxnet source code:
The creators of Duqu had access to the source code of Stuxnet, not just the Stuxnet binaries. The attackers intend to use this capability to gather intelligence from a private entity to aid future attacks on a third party. While suspected, no similar precursor files have been recovered that predate the Stuxnet attacks.
The arrival of Stuxnet signaled that cyberattacks have entered a new phase, with nation states and professional, highly-skilled programmers helping elevate cyberwarfare to a new, more sophisticated (and dangerous) level. Microsoft Technical Fellow Mark Russinovich offers up a fictional account of what can happen when terrorist groups turn to cyberwarfare in his novel Zero Day, and it’s a chilling preview of what the future of warfare could look like.
While many fingers are pointing at U.S. and Israeli intelligence service for creating Stuxnet – and possibly Duqu — what happens when a hostile nation or well-organized terrorists develop the same level of cyberwarfare capability? Questions like these are undoubtedly keeping IT security professionals and experts at government security agencies awake at night.
For more technical information on the Duqu worm, see Symantec’s W32.Duqu: The Precursor to the Next Stuxnet whitepaper [PDF] and a Symantec post that provides additional Duqu technical details.
The New Face of War: How War Will Be Fought in the 21st Century
Has Israel Begun A Cyber War On Iran With The Stuxnet ‘Missile’?: An article from: APS Diplomat News Service