
InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Jan 30 2021
The feeling of security and the reality of security don’t always match, says computer-security expert Bruce Schneier. In his talk, he explains why we spend billions addressing news story risks, like the “security theater” now playing at your local airport, while neglecting more probable risks — and how we can break this pattern.
Jan 27 2021
This must-have guide features simple explanations, examples, and advice to help you be security-aware online in the digital age. Learn how to:
* Keep your information secure
* Put the necessary controls on your home network, protecting your family from cyber crime
* Prevent identity theft when shopping online or using contactless payment
* Keep your children safe when using the Internet.
Jan 27 2021
MARITIME CYBER SECURITY
Although acknowledging previous relevant cases, the chosen starting point will be June, 16th 2017, when the International Maritime Organization (IMO) formally adopts the recommendations included in the three declarations of principles in the Resolution MSC.428 (98) entitled Cyber Risk Management in Safety Management System.
In this sense, the cyber security risk assessment becomes integral part of the objective (Art.1.2) included in the ISM Code; according to which the management of the cyber security risk must be included in the general objective, for this reason shipping companies must “…ensure safety at sea, prevention of human injury or loss of life, and avoidance of damage to the environment, in particular to the marine environment and to property“. In particular, these objectives are identified in the pursue of the following obligations:
1. provide for safe practices in ship operation and a safe working environment;
2. assess all identified risks to its ships, personnel and the environment and establish appropriate safeguards; and
3. continuously improve safety management skills of personnel ashore and aboard ships, including preparing for emergencies related both to safety and environmental protection.
In the declarations related to the MSC.428 (98), the IMO introduces for the first time the date of Jan., 1st 2021, stating that: “…Administrations (are encouraged) to ensure that cyber risks are appropriately addressed in safety management system no later than the first annual verification of the company’s Document of Compliance after 1 January 2021“.
The second date to remember is Jul. 5th 2017, when the IMO, through the Maritime Safety Committee released the Guidelines on Maritime Cyber Risk Management included in the MSC-FAL.1/Circ.3. These guidelines suggest recommendations identified as “high level“ for the management of cyber risk in the maritime sector, with special reference to shipping. The pursued aim is to promote the mitigation of cyber risks, through the adjustment of the safety management system, included in the ISM Code framework.
Nov 06 2020
Pwn2Own Tokyo 2020 hacking competition is started, bug bounty hunters already hacked a NETGEAR router and a Western Digital NAS devices.
The Pwn2Own Tokyo is actually coordinated by Zero Day Initiative from Toronto, Canada, and white hat hackers taking part in the competition have to demonstrate their ability to find and exploit vulnerabilities in a broad range of devices.
On the day one of the competition, bug bounty hunters have successfully hacked a vulnerability in the NETGEAR Nighthawk R7800 router. The participants were the Team Black Coffee, Team Flashback, and teams from cybersecurity firms Starlabs and Trapa Security, and the Team Flashback earned $20,000 for a remote code execution exploit that resulting from the chaining of two bugs in the WAN interface.
“The team combined an auth bypass bug and a command injection bug to gain root on the system. They win $20,000 and 2 points towards Master of Pwn.” reads the post on the official site of the Pwn2Own Tokyo 2020.
The Trapa team successfully chained a pair of bugs to gain code execution on the LAN interface of the router, the experts earned $5,000 and 1 point towards Master of Pwn.
The STARLabs team earned the same amount after using a command injection flaw to take control of the device.
The Western Digital My Cloud Pro series PR4100 NSA device was targeted by The Trapa Security team also earned $20,000 for a working exploit for the Western Digital My Cloud Pro series PR4100 NSA device.
The exploit code chained an authentication bypass bug and a command injection vulnerability to gain root on the device.
Source: Pwn2Own Tokyo Day one: NETGEAR Router, WD NAS Device hacked
Pwn2Own Tokyo (Live from Toronto) 2020 – Day One
httpv://www.youtube.com/watch?v=jX0b8iKXnbI&ab_channel=ZeroDayInitiative
Nov 02 2020
[pdf-embedder url=”https://blog.deurainfosec.com/wp-content/uploads/2020/11/Simpliv-Links.pdf” title=”Simpliv Links”]
Oct 06 2020
Including HP Official Ink and Toner cartridge security, HP announced rewards up to $10,000 under the new printer bug bounty program.
After pioneering a bug rewards program for printer security, HP takes another step in this direction. As announced, HP has expanded its bug bounty program for printers to include cartridge security vulnerabilities.
Source: HP Printer Bug Bounty Expands To Include Cartridge Security
Oct 02 2020
Christopher Wright is one of IT Governance Publishing’s most prolific writers, having released five books with us over the past six years.
His work covers many different topics, including advice on organizational cyber security, project management and risk management auditing.
In How Cyber Security Can Protect Your Business – A guide for all stakeholders, Wright provides an effective and efficient framework to help organizations manage cyber governance, risk and compliance.
How Cyber Security Can Protect Your BusinessBusinesses must protect themselves and their reputations, while reassuring stakeholders they take cyber security seriously. Wright’s pocket guide:
Receive 15% off all of Christopher Wright’s books throughout October by entering the voucher code WRIGHT15 at the checkout. |

|
Sep 17 2020
One of the new features in iOS 14 is the ability to change the default email or browser app to a third-party alternative such as Chrome, Edge, or Outlook. A bug in the first public release of iOS 14, however, causes your default browser or mail app setting to reset to Mail or Safari when […]
Source: iOS 14 default app settings automatically reset to Mail and Safari after reboot – 9to5Mac
In the version of iOS 14 released to the public this week, there is a massive caveat to the new default browser and settings. If you reboot your iPhone or iPad, the default app setting will reset to Apple’s first-party Mail and Safari applications.
What this means is that if you set Chrome as the default browser, but then your iPhone dies or you need to reboot it, Safari will once again become the default browser app until you go back into the Settings app and make the change again. The same applies to email apps such as Microsoft Outlook and Spark as well.
This is almost certainly some sort of bug on Apple’s side, because it is affecting email and browser apps from multiple companies including Google, Microsoft, and Readdle. On Twitter, a Google Chrome engineer has acknowledged the problem, though the ball is likely in Apple’s court to roll out some sort of fix — unless this is bizarrely the intended behavior.
Sep 01 2020
While the US, Russia, Israel, and several European nations all have sophisticated cyber capabilities, one threat intelligence firm argues that China’s aggressive approach to cyber operations has made it perhaps the world’s greatest cyber power.
Source: Is China the World’s Greatest Cyber Power?
“The goal is simple: break down trust in democracies, disrupt election cycles or manipulate democratic election results, and gain economic advantage over adversaries to advance global position and power,” according to the report.
“Over the past decade, China has become increasingly forthright in its intentions, and this change has been observed in cyber operations as well,” the report states. “Researchers have observed stark differences in tactics, tone, and behavior from Chinese state-sponsored cyber, military, and political parties over the past several years.”
“When it comes to China, cyber is not a tactical weapon, it is a strategic means to an end,” Maor says. “And if you are wondering what that end is, it is not something secret — it is something that is published every five years.”
There’s A Crisis That Is Quietly Creating New Economic Superpowers…
httpv://www.youtube.com/watch?v=h6GqEpmn_Fk
Aug 21 2020
Mozilla has expanded its bug bounty program including rewards for bypass methods for the exploit mitigations and security features in Firefox.
Source: Mozilla offers rewards for Bypassing Firefox Exploit Mitigations
Why Firefox is the best browser for privacy and how to configure things properly
httpv://www.youtube.com/watch?v=NH4DdXC0RFw
Jul 20 2020
Programs will address diversity and inclusion, mental health and career education.
“The technical content that is presented on the Black Hat stage each year is an important contribution to the industry, but we’ve found that more sensitive topics such as mental health and diversity within the information security community are often not highlighted enough,” said Steve Wylie, Black Hat General Manager.
Source: Black Hat USA Announces New Community Programs to Address the Needs of Information Security Professionals
Download a Security Risk Assessment Steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Jul 17 2020
Twitter Inc had stepped up its search for a chief information security officer in recent weeks, two people familiar with the effort told Reuters, before the breach of high-profile accounts on Wednesday raised alarms about the platform’s security. Twitter said hackers had targeted employees with access to its internal systems and “used this access to take control of many highly-visible (including verified) accounts.”
The second and third rounds of hijacked accounts tweeted out messages telling users to send bitcoin to a given address in order to get more back. Publicly available blockchain records show the apparent scammers received more than $100,000 worth of cryptocurrency.
The U.S. House Intelligence Committee was in touch with Twitter regarding the hack, according to a committee official who did not wish to be named.
Source: Twitter stepped up search to fill top security job ahead of hack
httpv://www.youtube.com/watch?v=4pquwx-doYg
Explore latest CISO Titles at DISC InfoSec
Download a Security Risk Assessment Steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Jul 13 2020
10 pieces of technical advice you should consider putting in place. Guidance on how organisations can protect themselves in cyberspace, including the 10 steps to cyber security.
Source: The 10 Steps to cyber security
Download a Security Risk Assessment Steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Jul 07 2020
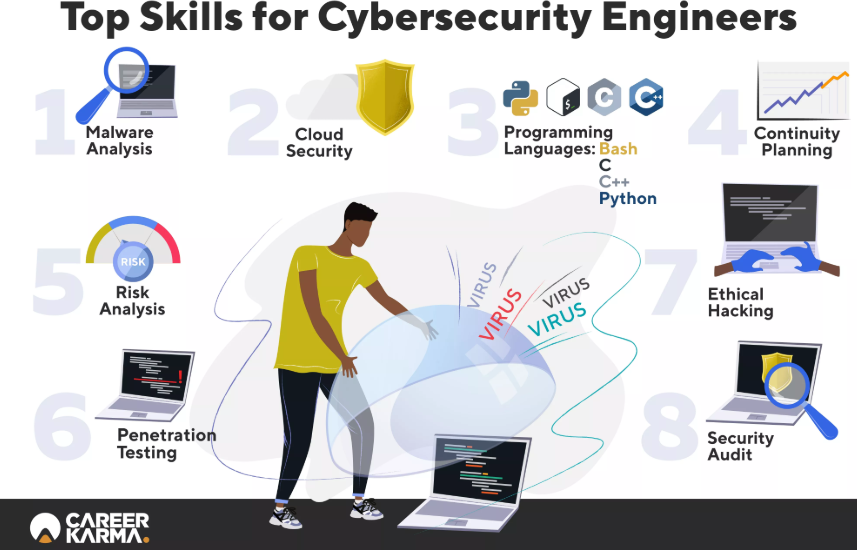
The future of work is online and remote. This has been proven by the recent Covid-19 pandemic, as companies who had been reluctant to embrace the remote-work trend suddenly found themselves running an almost entire remote-based company. As things stand, it is very likely that much of the working world will remain remote-based.
The new remote-working world means two things. The first is that the world will become increasingly more reliant on technology. The second is that the need for top-notch cybersecurity infrastructure will become more important to protect the private information of companies, employees and customers. Both of these are key indicators that the tech industry, which continues to thrive even during the coronavirus pandemic, will only continue to grow and at a faster rate than ever. If you are considering making a career change, you should absolutely look into the tech industry. More specifically, you should explore careers in cybersecurity.
Cybersecurity professionals are tasked with the programming that powers the systems, methods and policies that safeguard the software and online programs from malicious third-party cyberattacks. Recent cyberattacks on companies like Sony and Capital One made headlines, and for good reason. Millions and millions of private customer information (such as social security numbers) were immediately at risk. Skilled cybersecurity engineers are tasked with finding the ways that hackers break into mainframes at companies, and fix any potential weak spots.
A cybersecurity engineer sometimes serves as a “white hat” hacker, ethically hacking into their own company to find these potential weak spots in the company’s security infrastructure. If any weak spots are found, the cybersecurity engineer immediately fixes the problem.
Cybersecurity engineers earn a decent salary, with most junior engineers making $65,000 a year. More senior roles earn as much as $137,000, according to Payscale.
If you are wondering how to become a cybersecurity engineer, you want to start by learning how to code. You may be tempted to think that doing so will require going back to school to earn a computer science or IT degree, but this is actually becoming a less popular choice among career switchers. Instead, many are opting for the much faster and more economical route of coding bootcamps.
A coding bootcamp is a short-term means of tech education that is hyper-focused on coding. With most students completing their bootcamp in just two to three months, there is not much room for anything else but teaching what is coding, and how to use it to earn a living. As was mentioned earlier, the working world has switched to remote. Well, so has tech education, and many coding schools also offer online coding bootcamps.
Perhaps the most beneficial feature of a coding bootcamp is the flexible tuition financing that they offer. Coding schools offer what is called an income-sharing agreement (ISA). This is actually a tuition financing option that is opposite from how a student loan works. Instead of students taking on $40,000 or more in debt that is impossible to escape from, even through bankruptcy, an ISA works as a way for a coding school to invest in their students.
ISAs offered by schools like App Academy work by waiving the bootcamp tuition so that the student doesn’t have to pay anything upfront. The student agrees to repay the cost through monthly payments based entirely on their salary after they graduate and land a job. Since the school is making an investment, with its return based on how much money their graduates can earn, it makes sense that many of these programs do their best to ensure that their grads are not only well-prepared in terms of programming skills, but are also marketable to potential employers.
To do this, most coding schools hold regular job fairs and networking events that give their students a chance to connect with potential employers. These events are also held through online means so that all students can have an opportunity to join. Many coding schools also have partnership programs with local companies that allow them to place their graduates in legitimate, well-paying programming jobs more quickly.
InfoSec Threats, Books and Training Courses
Download a Security Risk Assessment Steps paper!
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles
Jun 29 2020

SMBs are responsible for nearly 44% of US economic activity, but given the current climate, it can be difficult for them to find available and/or affordable resources.
Source: Tall Order for Small Businesses: 3 Tips to Find Tailored Security Solutions
FIC2020: The top cybersecurity trends to watch for
httpv://www.youtube.com/watch?v=QZKSUwSo0IA
Subscribe to DISC InfoSec blog by Email
Take an awareness quiz to test your basic cybersecurity knowledge
DISC InfoSec 🔒 securing the business 🔒 via latest InfoSec titles