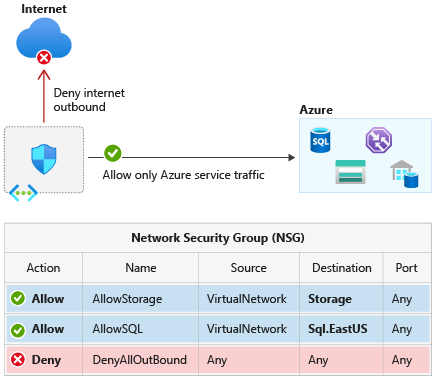
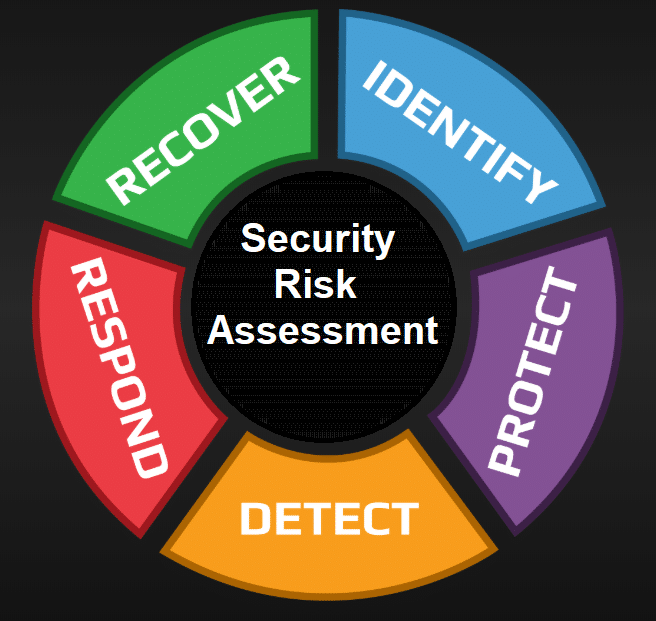
The document “Step-by-Step Explanation of ISO 27001/ISO 27005 Risk Management” by Advisera Expert Solutions offers a comprehensive guide to implementing effective information security risk management in alignment with ISO 27001 and ISO 27005 standards. It aims to demystify the process, providing practical steps for organizations to identify, assess, and treat information security risks efficiently. Advisera
1. Introduction to Risk Management
Risk management is essential for organizations to maintain competitiveness and achieve objectives. It involves identifying, evaluating, and treating risks, particularly those related to information security. The document emphasizes that while risk management can be complex, it doesn’t have to be unnecessarily complicated. By adopting structured methodologies, organizations can manage risks effectively without excessive complexity.
2. Six Basic Steps of ISO 27001 Risk Assessment and Treatment
The risk management process is broken down into six fundamental steps:
- Risk Assessment Methodology: Establishing consistent rules for conducting risk assessments across the organization.
- Risk Assessment Implementation: Identifying potential problems, analyzing, and evaluating risks to determine which need treatment.
- Risk Treatment Implementation: Developing cost-effective strategies to mitigate identified risks.
- ISMS Risk Assessment Report: Documenting all activities undertaken during the risk assessment process.
- Statement of Applicability: Summarizing the results of risk treatment and serving as a key document for auditors.
- Risk Treatment Plan: Outlining the implementation of controls, including responsibilities, timelines, and budgets.
Management approval is crucial for the Risk Treatment Plan to ensure the necessary resources and commitment for implementation.
3. Crafting the Risk Assessment Methodology
Developing a clear risk assessment methodology is vital. This involves defining how risks will be identified, analyzed, and evaluated. The methodology should ensure consistency and objectivity, allowing for repeatable and comparable assessments. It should also align with the organization’s context, considering its specific needs and risk appetite.
4. Identifying Risks: Assets, Threats, and Vulnerabilities
Effective risk identification requires understanding the organization’s assets, potential threats, and vulnerabilities. This step involves creating an inventory of information assets and analyzing how they could be compromised. By mapping threats and vulnerabilities to assets, organizations can pinpoint specific risks that need to be addressed.
5. Assessing Consequences and Likelihood
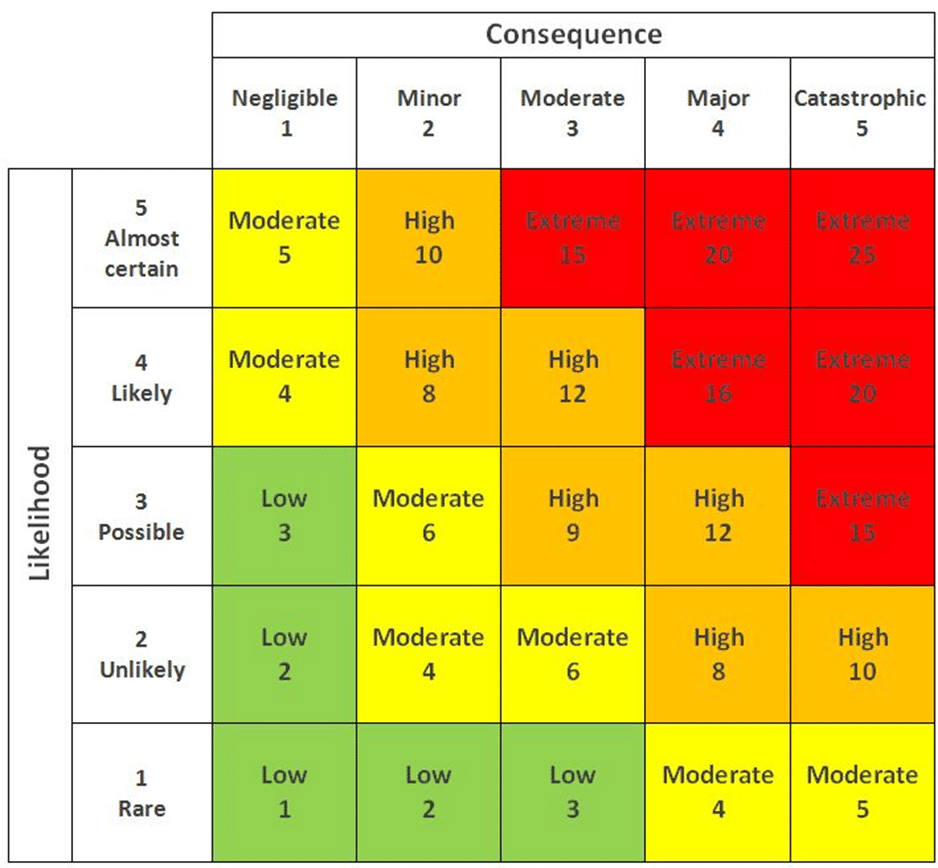
Once risks are identified, assessing their potential impact and the likelihood of occurrence is essential. This evaluation helps prioritize risks based on their severity and probability, guiding the organization in focusing its resources on the most significant threats. Both qualitative and quantitative methods can be employed to assess risks effectively.
6. Implementing Risk Treatment Strategies
After assessing risks, organizations must decide on appropriate treatment strategies. Options include avoiding, transferring, mitigating, or accepting risks. Selecting suitable controls from ISO 27001 Annex A and integrating them into the Risk Treatment Plan ensures that identified risks are managed appropriately. The plan should detail the implementation process, including responsible parties and timelines.
7. Importance of Documentation and Continuous Improvement
Documentation plays a critical role in the risk management process. The ISMS Risk Assessment Report and Statement of Applicability provide evidence of the organization’s risk management activities and decisions. These documents are essential for audits and ongoing monitoring. Furthermore, risk management should be a continuous process, with regular reviews and updates to adapt to changing threats and organizational contexts.
By following these structured steps, organizations can establish a robust risk management framework that aligns with ISO 27001 and ISO 27005 standards, enhancing their information security posture and resilience.

Information Security Risk Management for ISO 27001/ISO 27002
How to Continuously Enhance Your ISO 27001 ISMS (Clause 10 Explained)
Continual improvement doesn’t necessarily entail significant expenses. Many enhancements can be achieved through regular internal audits, management reviews, and staff engagement. By fostering a culture of continuous improvement, organizations can maintain an ISMS that effectively addresses current and emerging information security risks, ensuring resilience and compliance with ISO 27001 standards.
ISO 27001 Compliance and Certification
Security Risk Assessment and ISO 27001 Gap Assessment
At DISC InfoSec, we streamline the entire process—guiding you confidently through complex frameworks such as ISO 27001, and SOC 2.
Here’s how we help:
- Conduct gap assessments to identify compliance challenges and control maturity
- Deliver straightforward, practical steps for remediation with assigned responsibility
- Ensure ongoing guidance to support continued compliance with standard
- Confirm your security posture through risk assessments and penetration testing
Let’s set up a quick call to explore how we can make your cybersecurity compliance process easier.
Feel free to get in touch if you have any questions about the ISO 27001 Internal audit or certification process.
Successfully completing your ISO 27001 audit confirms that your Information Security Management System (ISMS) meets the required standards and assures your customers of your commitment to security.
Get in touch with us to begin your ISO 27001 audit today.
ISO 27001:2022 Annex A Controls Explained
Preparing for an ISO Audit: Essential Tips and Best Practices for a Successful Outcome
Many companies perceive ISO 27001 as just another compliance expense?
ISO 27001: Guide & key Ingredients for Certification
DISC InfoSec Previous posts on ISO27k
ISO certification training courses.
Difference Between Internal and External Audit
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services