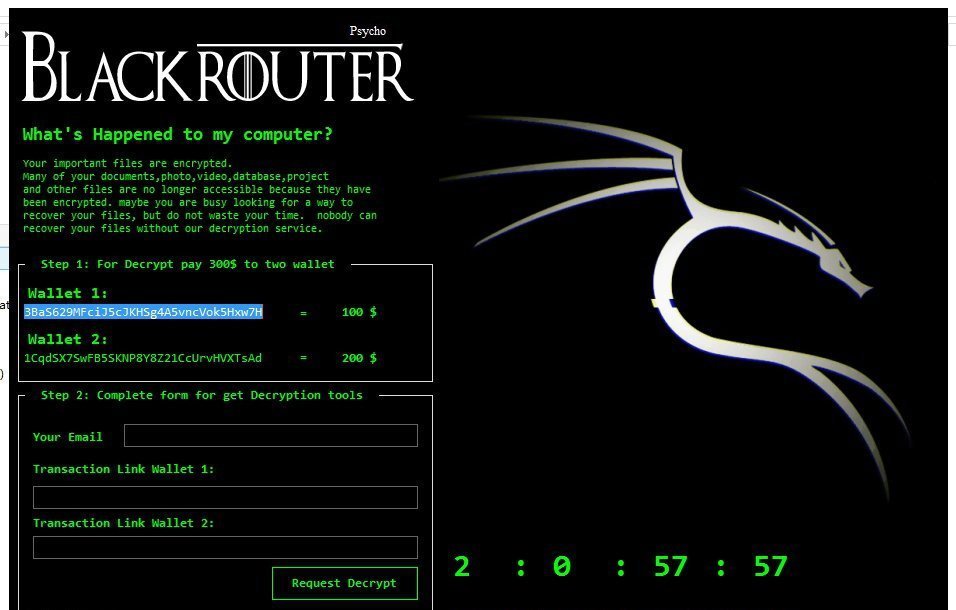
Group-IB published a report titled “Ransomware Uncovered 2020-2021”. analyzes ransomware landscape in 2020 and TTPs of major threat actors.
Group-IB, a global threat hunting and adversary-centric cyber intelligence company, has presented its new report “Ransomware Uncovered 2020-2021”. The research dives deep into the global ransomware outbreak in 2020 and analyzes major players’ TTPs (tactics, techniques, and procedures).
By the end of 2020, the ransomware market, fuelled by the pandemic turbulence, had turned into the biggest cybercrime money artery. Based on the analysis of more than 500 attacks observed during Group-IB’s own incident response engagements and cyber threat intelligence activity, Group-IB estimates that the number of ransomware attacks grew by more than 150% in 2020, with many restless players having joined the Big Game Hunting last year.
In 2020, ransomware attacks on average caused 18 days of downtime for the affected companies, while the average ransom amount increased almost twofold. Ransomware operations turned into robust competitive business structures going after large enterprises, with Maze, Conti, and Egregor gangs having been at the forefront last year. North America, Europe, Latin America, and the Asia-Pacific became the most commonly attacked regions respectively.
To keep the cybersecurity professionals up to date with how ransomware gangs operate and help the defense teams thwart their attacks, Group-IB’s DFIR team has for the first time mapped the most commonly used TTPs in 2020 in accordance with MITRE ATT&CK®. If you are a cybersecurity executive, make sure your technical team receives a copy of this report for comprehensive threat hunting and detection tips.
More on: Most Active Ransomware Gangs in 2020

The growing threat of ransomware has put it in the spotlight of law enforcement. Some gangs operating under the Ransomware-as-a-Service (RaaS) model, such as Egregor and Netwalker, were impacted by the police efforts. Another notorious RaaS collective, Maze, called it quits at the end of 2020. Despite these events, the ransomware business continues prospering, with the Ransomware-as-a-Service model being of the driving forces behind this phenomenal growth.
Ransomware empire prospers in pandemic-hit world.