Becoming verified on well-known platforms such as Instagram, Twitter, or the Apple AppStore has become the standard for determining one’s standing in the current online social scene. As users, we trust verified accounts more than those that aren’t. In the business sector, the situation is exactly the same with third-party OAuth app publishers who have been validated by Microsoft. Unfortuitously, threat actors have noticed the significance of the verified status in the Microsoft environment as well.
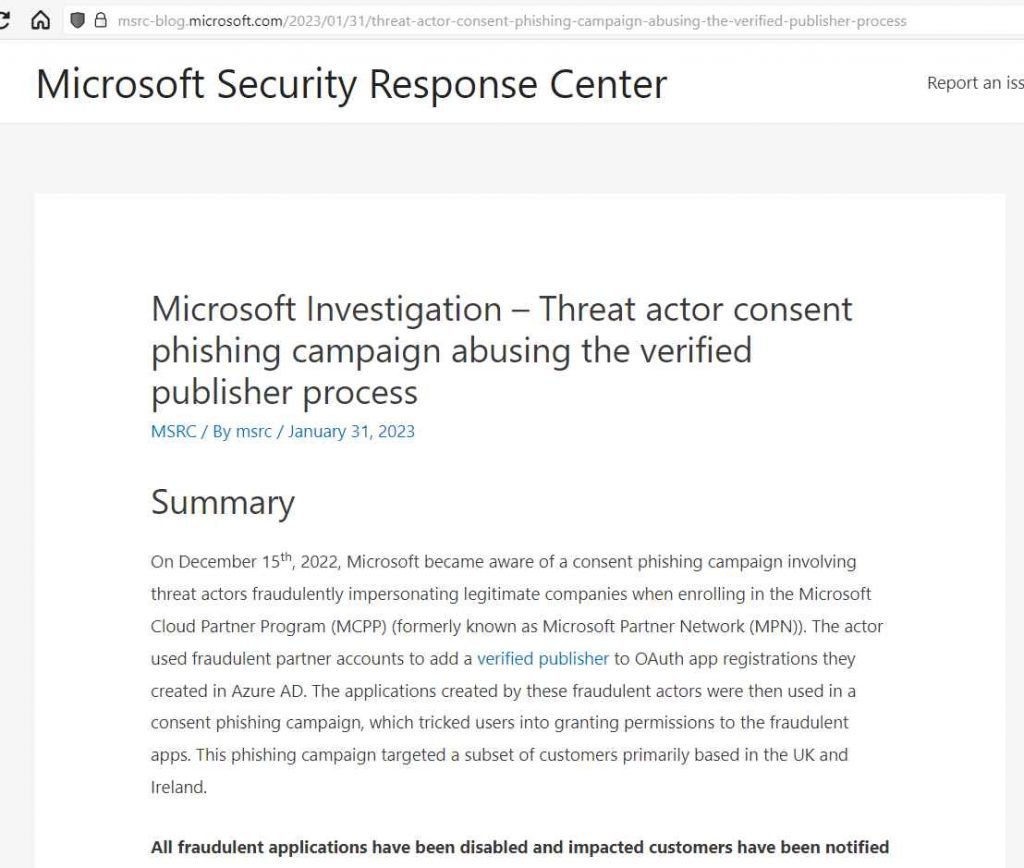
Researchers from Proofpoint found a new malicious third-party OAuth app campaign that used the Microsoft “certified publisher” status in order to meet certain of Microsoft’s criteria pertaining to the distribution of OAuth apps. This raised the likelihood that users would be duped into giving authorization when a malicious third-party OAuth app (from this point forward, referred to as a “OAuth app” or a “malicious app”) asks access to data that is available through a user’s account. Researchers found that the malicious applications had extensive delegated rights, such as the ability to read emails, change mailbox settings, and obtain access to files and other data that were associated with the user’s account.
According to Microsoft, a Microsoft account can achieve the status of “publisher verified” or “verified publisher” when the “publisher of the app has verified their identity using their Microsoft Partner Network (MPN) account and has associated this MPN account with their app registration.” Other terms for this achievement include “verified publisher” and “verified publisher.” (Just so there isn’t any misunderstanding, a “certified publisher” has absolutely nothing to do with the desktop program known as Microsoft Publisher, which is available in some levels of Microsoft 365.)
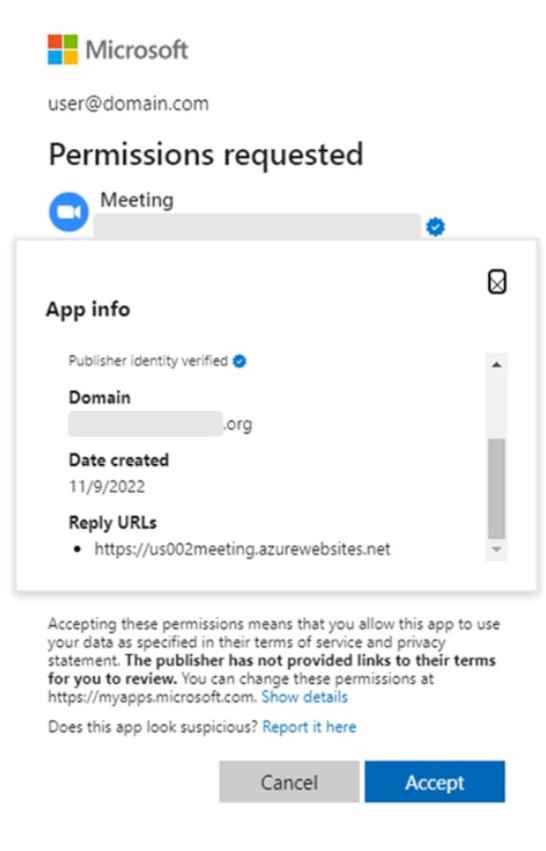
The material provided by Microsoft goes on to provide more clarification, stating that “after the publisher of an app has been confirmed, a blue verified badge displays in the Azure Active Directory (Azure AD) authorization prompt for the app and on other websites.” Note that when Microsoft discusses third-party OAuth applications, it is talking to apps that have been developed by companies that fall into this category. These businesses are referred to as “publishers” in the Microsoft environment.
Researchers were able to identify three malicious applications that were developed by three distinct malicious publishers. The same firms were singled out for attack by these applications, and they are connected to the same malicious infrastructure. Multiple people were seen giving permission to the malicious applications, which put the environment of their firm at risk.
According to the findings of their investigation, the majority of the participants in this campaign seemed to originate from the United Kingdom (UK). Individuals from the finance and marketing departments, as well as high-profile users such as managers and executives, were among those whose accounts were compromised. Beginning on December 6th, 2022, we made our first observation of this particular avatar of malicious third-party OAuth applications. In every instance, the specialized backend infrastructure that supports the applications was only put in place a few days or weeks before December 6th.
When users give their permission, malicious applications’ default delegated permissions allow threat actors to access and manipulate mailbox resources, calendar events, and meeting invitations that are linked to accounts that have been compromised. This access and manipulation is only possible when users give their consent. After receiving approval, gaining access does not need further action on the part of the user since the permissions also allow “offline access.” The given token, also known as the refresh token, often has a lengthy expiration time that is more than one year. This provided threat actors with access to the data associated with the hacked account as well as the potential to utilize the compromised Microsoft account in later BEC attempts or other types of attacks.
In addition to the possibility of user accounts being hijacked, firms that have been impersonated run the risk of having their brand abused. It is quite difficult for firms in this situation to determine whether or not their reputation is being sullied by one of these assaults. There is no necessary contact that must take place between the entity that is being impersonated and the malicious verified publisher.
Even though an OAuth third-party app has been validated by Microsoft, it is imperative to proceed with extreme care when allowing access to the app. OAuth applications are not reliable and should not be trusted only on the basis of their verified publisher status. End users are likely to become victims of sophisticated social engineering approaches because of the complexity of the assaults that are being carried out.








![A Hacker's Mind: How the Powerful Bend Society's Rules, and How to Bend them Back by [Bruce Schneier]](https://m.media-amazon.com/images/W/WEBP_402378-T1/images/I/41Yeq54EmfL.jpg)























