ISO 27701 is an international standard that provides guidelines for implementing a privacy information management system (PIMS) based on the requirements of the General Data Protection Regulation (GDPR) and other relevant privacy regulations. It was published by the International Organization for Standardization (ISO) in August 2019.
ISO 27701 is an extension of ISO 27001, which is a widely recognized international standard for information security management. It introduces additional controls and requirements specific to the management of privacy information within an organization.
The standard outlines the framework for establishing, implementing, maintaining, and continually improving a privacy information management system. It helps organizations to identify and manage privacy risks, implement privacy controls, and demonstrate compliance with applicable privacy laws and regulations.
ISO 27701 focuses on protecting individuals’ privacy rights and ensuring responsible handling of personal information. It provides guidance on various aspects of privacy management, including privacy policy development, privacy risk assessment, privacy impact assessments, consent management, data subject rights, data breach management, and vendor management.
By implementing ISO 27701, organizations can enhance their privacy practices, build trust with customers and partners, and demonstrate their commitment to protecting personal information. It is especially relevant for organizations that process large amounts of personal data or handle sensitive information, as it helps them establish a systematic approach to privacy management.
It’s important to note that ISO 27701 is not a certification itself but an extension to ISO 27001. Organizations can seek certification against ISO 27001 and include ISO 27701 requirements as part of their certification process to demonstrate compliance with privacy regulations.
in what situation ISO 27701 certification may be appropriate?
ISO 27701 certification may be appropriate for organizations that handle personal data and are subject to privacy regulations such as the General Data Protection Regulation (GDPR) in the European Union or other similar privacy laws worldwide. Here are some situations where ISO 27701 certification may be relevant:
- Data Controllers and Processors: Organizations that act as data controllers or processors and handle personal data on a significant scale can benefit from ISO 27701 certification. This includes organizations in sectors such as healthcare, finance, e-commerce, technology, and marketing that process large volumes of personal information.
- Legal and Regulatory Compliance: ISO 27701 certification helps organizations demonstrate compliance with privacy regulations. If an organization operates in jurisdictions with strict privacy laws or serves customers from regions with robust privacy requirements, certification can provide assurance to stakeholders that the organization has implemented appropriate privacy controls.
- Third-Party Assurance: Organizations that act as vendors or service providers for other companies may pursue ISO 27701 certification to demonstrate their commitment to privacy management. This can be particularly relevant for organizations providing cloud services, data processing, or other services involving personal data, as it helps build trust and confidence with customers.
- Competitive Advantage: ISO 27701 certification can serve as a competitive differentiator for organizations. It showcases their dedication to privacy protection and can attract customers who prioritize strong privacy practices and compliance when selecting vendors or partners.
- Data Breach Prevention and Response: ISO 27701 provides guidelines for managing data breaches and responding to privacy incidents effectively. Organizations that want to establish robust incident response procedures and enhance their ability to prevent and manage data breaches can benefit from implementing ISO 27701.
- Privacy-Driven Culture: ISO 27701 certification promotes a privacy-centric culture within an organization. It helps organizations establish clear policies, procedures, and training programs to educate employees about privacy responsibilities and foster a privacy-aware mindset throughout the organization.
Ultimately, the decision to pursue ISO 27701 certification depends on the specific needs, risk profile, and regulatory environment of the organization. Conducting a thorough assessment of privacy risks, legal requirements, and business objectives can help determine whether certification is appropriate and beneficial for the organization.
Achieve full compliance with ISO 27701:2019
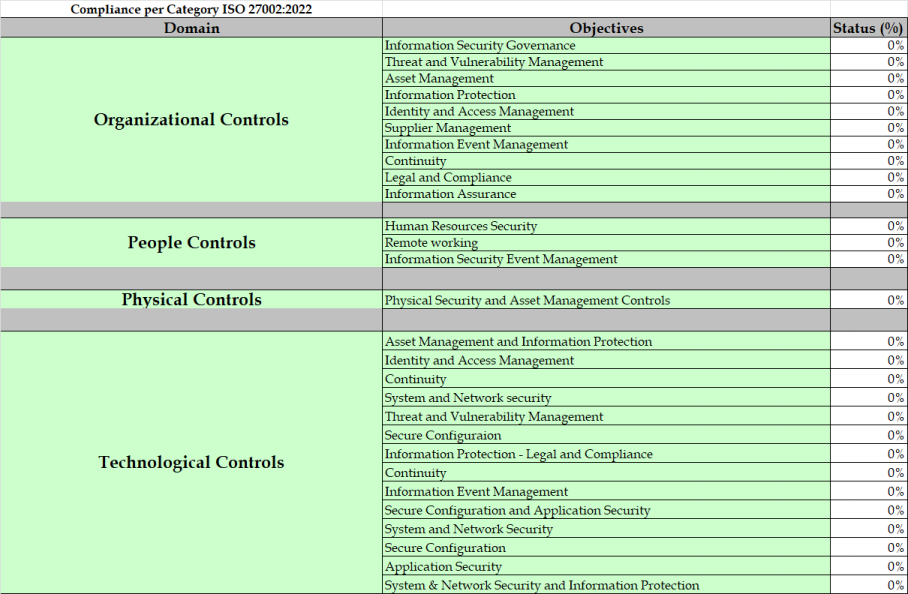
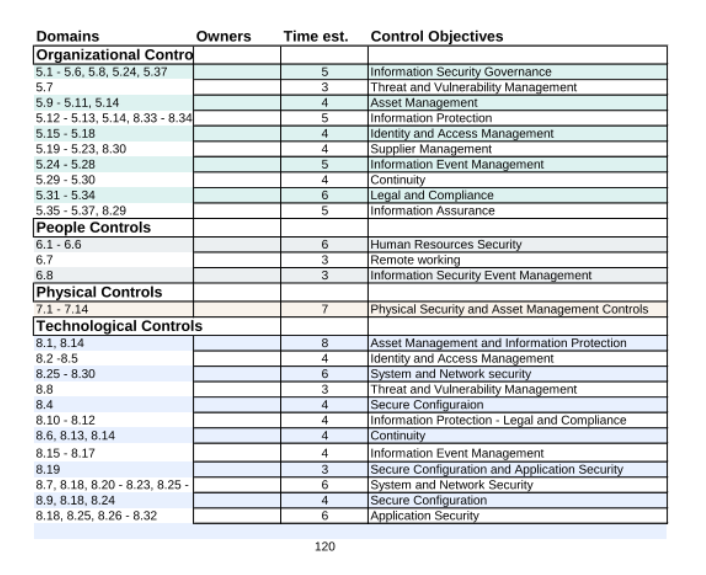
The ISO 27701 Gap Analysis Tool has been created to help organizations identify whether they are meeting the requirements of the Standard and where they are falling short. Note that this tool assumes that you have a complete and functioning ISO 27001:2013 ISMS (information security management system).
It helps organizations prioritise work areas in order to expand an existing ISMS to take account of privacy. It also gives organizations direction, helping project managers identify where to start.

This standard is ideal for organizations wishing to implement a PIMS that supports their ISMS objectives and helps meet their data privacy compliance requirements, such as those stipulated by the EU’s GDPR (General Data Protection Regulation) and the UK’s DPA (Data Protection Act) 2018.

An ideal guide for anyone wanting to implement a PIMS (personal information management system) and understand how it can benefit their organization
ISO/IEC 27701:2019: An introduction to privacy information management

More ISO 27701 related tools and training…
We’d love to hear from you! If you have any questions, comments, or feedback, please don’t hesitate to contact us. Our team is here to help and we’re always looking for ways to improve our services. You can reach us by email (info@deurainfosec.com), or through our website’s contact form.
InfoSec tools | InfoSec services | InfoSec books