The article discusses a new cyberattack targeting Apache Tomcat servers, a popular open-source web server environment written in Java. Apache Tomcat supports various technologies and is widely used by developers.
The attack is orchestrated by the Mirai botnet and bitcoin miners, specifically targeting improperly configured Apache Tomcat servers lacking sufficient security measures. The research, conducted by Aqua, involved setting up Tomcat server honeypots to monitor the attacks over a two-year period.
During the research, more than 800 attacks were recorded, with an overwhelming 96% of them linked to the Mirai botnet. Out of these attempts, 20% (152 attacks) utilized a web shell script named “neww,” originating from 24 different IP addresses. Interestingly, 68% of these attacks were attributed to a single IP address, 104.248.157[.]218. Fortunately, the attacks using the “neww” web shell script were unsuccessful in compromising the targeted servers.
A brute force attack was carried out by the threat actor against the scanned Tomcat servers in order to acquire access to the web application management using a variety of different credential combinations.
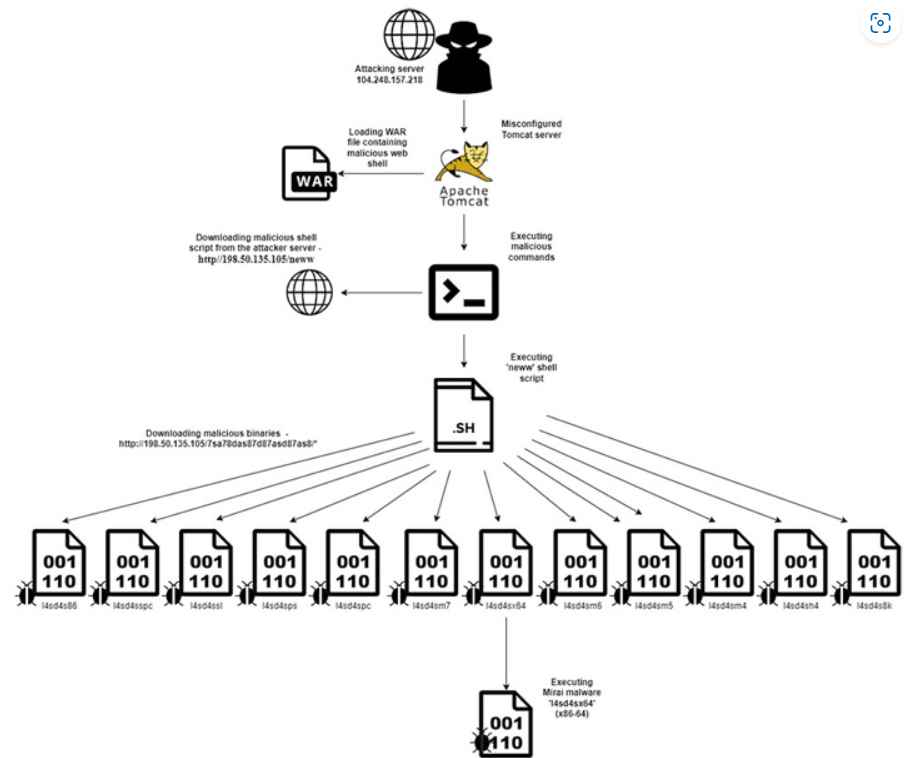
After successfully gaining entrance, threat actors will install a WAR file containing a web shell called ‘cmd.jsp’ on the Tomcat server that has been hacked. This will allow for remote command execution.
The “downloading and running” of the “neww” shell script is an integral part of the whole attack chain. The “rm -rf” command is then used to remove the script once it has been executed. The software then retrieves 12 binary files that are customized to the architecture of the system that is being attacked.
While all of these components work together to expedite the web app deployment on compromised Tomcat servers in an effective manner.
The last step of the malware is a variation of the Mirai botnet that uses infected systems for the purpose of coordinating distributed denial-of-service (DDoS) assaults.
Threat actor infiltrates web app manager by using legitimate credentials, uploads disguised web shell in WAR file, remotely executes commands, and starts the attack.The statistics shed light on the profitable expansion of cryptocurrency mining, which is projected to have a 399% increase and 332 million cryptojacking assaults worldwide in H1 2023.
Recommendation
In order to protect against attacks of this kind, specialists in the field of cybersecurity suggested the following measures:
Make sure that each of your environments has the appropriate configuration.
Be careful to do regular scans of your servers to look for any dangers.
Cloud-native tools that scan for vulnerabilities and misconfigurations should be made available to your development, DevOps, and security teams so that they can better do their jobs.
It is imperative that you use runtime detection and response technologies.
Web Security for Developers: Real Threats, Practical Defense

InfoSec books | InfoSec tools | InfoSec services








