By Kevin Townsend
Never-ending breaches , ever-increasing regulations, and the potential effect of brand damage on profits has made cybersecurity
, ever-increasing regulations, and the potential effect of brand damage on profits has made cybersecurity a mainstream board-level issue. It has never been more important for cybersecurity controls
a mainstream board-level issue. It has never been more important for cybersecurity controls and processes to be in line with business
and processes to be in line with business
priorities.

A recent survey by security firm Varonis highlights that business and security are not fully aligned; and while security teams feel they are being heard, business leaders admit they aren’t listening.
feel they are being heard, business leaders admit they aren’t listening.
The problem is well-known: security and business speak different languages. Since security is the poor relation of the two, the onus is absolutely on security to drive the conversation in business terms. When both sides are speaking the same language, aligning security controls  with business priorities will be much easier.
with business priorities will be much easier.
Well-presented metrics are the common factor understood by both sides and could be used as the primary driver in this alignment. The reality, however, is this isn’t always happening
are the common factor understood by both sides and could be used as the primary driver in this alignment. The reality, however, is this isn’t always happening
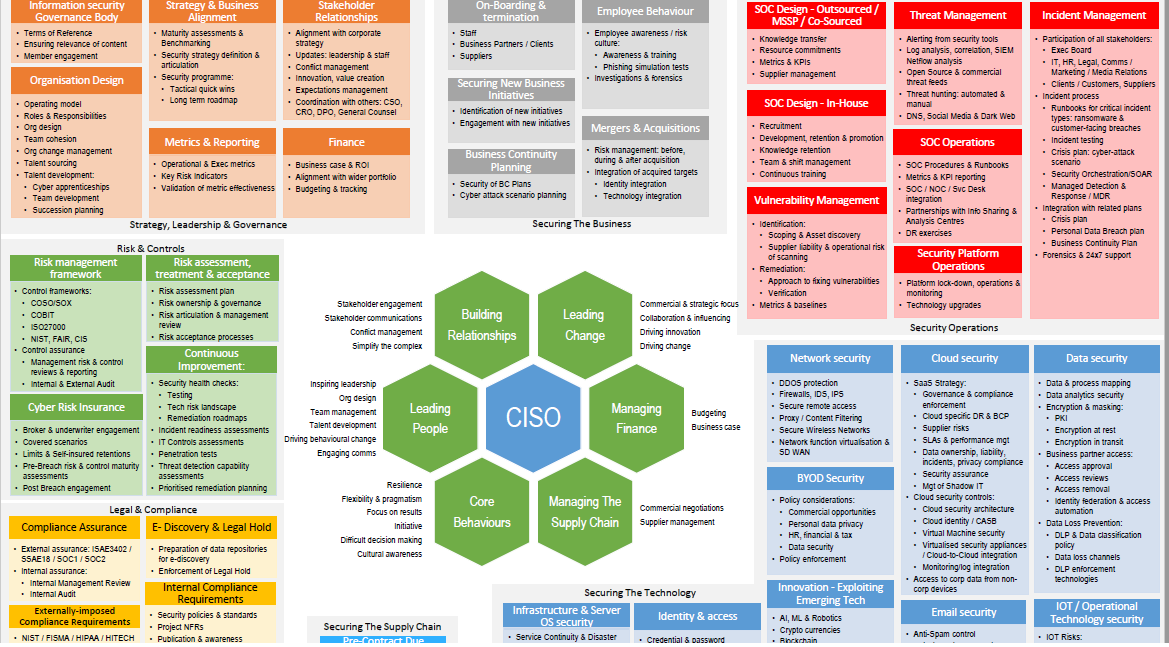
Using metrics to align Security and Business: Information security metrics
SecurityWeek spoke to several past and present CISO s to better understand the use of metrics to communicate with business leaders: why metrics are necessary; how they can be improved; what are the problems; and what is the prize?
s to better understand the use of metrics to communicate with business leaders: why metrics are necessary; how they can be improved; what are the problems; and what is the prize?
Demolishing the Tower of Babel
“While some Board members may be aware of what firewalls are,” comments John Masserini: CISO at Millicom Telecommunications, “the vast majority have no understanding what IDS /IPS
/IPS , SIEM
, SIEM s, Proxies, or any other solution you have actually do. They only care about the level of risk in the company.”
s, Proxies, or any other solution you have actually do. They only care about the level of risk in the company.”
CISOs, on the other hand, understand risk but do not necessarily understand which parts of the business are at most risk at any time. Similarly, business leaders do not understand how changing cybersecurity threats impact specific business risks
impact specific business risks .
.
The initial onus is on the security lead to better understand the business side of the organization to be able to deliver meaningful risk management metrics that business leaders understand. This can be used to start the process for each side to learn more about the other. Business will begin to see how security reduces risk, and will begin to specify other areas that need more specific protection.
that business leaders understand. This can be used to start the process for each side to learn more about the other. Business will begin to see how security reduces risk, and will begin to specify other areas that need more specific protection.
The key and most common difficulty is in finding and presenting the initial metrics to get the ball rolling. This is where the different ‘languages’ get in the way. “The IT department led by the CIO typically must maintain uptime for critical systems and support transformation initiatives that improve the technology used by the business to complete its mission,” explains Keyaan Williams, CEO at CLASS-LLC. “The Security department led by the CISO typically must maintain confidentiality, integrity, and availability of data and information stored, processed, or transmitted by the organization. These departments and these leaders tend to provide metrics that focus on their tactical duties rather than business drivers that concern the board/C-suite.”
and information stored, processed, or transmitted by the organization. These departments and these leaders tend to provide metrics that focus on their tactical duties rather than business drivers that concern the board/C-suite.”
Drew Koenig, consultant and host of the Security in Five podcast, sees the same basic problem. “In security there tends to be a focus on the technical metrics . Logins, blocked traffic, transaction counts, etc… but most do not map back to business objectives or are explained in a format business leaders can understand or care about. Good metrics need to be tied to dollars, business efficiency shown through time improvements, and able to show trending patterns of security effectiveness as it relates to the business. That’s the real challenge.”
. Logins, blocked traffic, transaction counts, etc… but most do not map back to business objectives or are explained in a format business leaders can understand or care about. Good metrics need to be tied to dollars, business efficiency shown through time improvements, and able to show trending patterns of security effectiveness as it relates to the business. That’s the real challenge.”
Williams sees the problem emanating from a lack of basic business training in the academic curriculum that supports IT and security degrees. “The top management tool in 2017 was strategic planning,” he said. “Strategic planning is often listed as one of the top-five tools of business leaders. How many security leaders understand strategic planning and execution enough to ensure their metrics contribute to the strategic initiatives of the organization?”
It is not up to the business leaders to learn about security. “The downfall for many CISOs in the past is believing that business needs to understand security,” adds Candy Alexander, a virtual CISO and president-elect of ISSA. “That is a mistake, because security is our job. We need to better understand the business, so that we can articulate the impact of not applying appropriate safeguards
and president-elect of ISSA. “That is a mistake, because security is our job. We need to better understand the business, so that we can articulate the impact of not applying appropriate safeguards . The key to this whole approach is for the CISO to understand the business, and to understand the mission and goals of the business.”
. The key to this whole approach is for the CISO to understand the business, and to understand the mission and goals of the business.”
for more on this article: CISOs and the Quest for Cybersecurity Metrics Fit for Business
Tags: CISO, infosec metrics