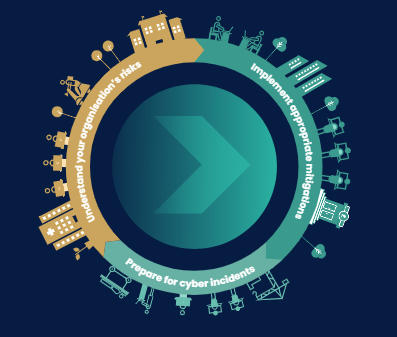
Cybersecurity and cyber risk are closely related, but they operate with different priorities and lenses. Cybersecurity is primarily concerned with defending systems, networks, and data from threats. It focuses on identifying vulnerabilities, applying controls, and fixing technical weaknesses. The central question in cybersecurity is often, “How do we remediate this issue to make the system more secure?” It is action-oriented and technical, aiming to reduce exposure through engineering and operational safeguards.
Cyber risk, in contrast, shifts the conversation from technical fixes to business consequences. It asks, “If this system fails or is compromised, what does that mean for the organization?” This perspective evaluates the likelihood of an event and its potential impact on finances, operations, compliance, and reputation. Not every vulnerability translates into significant business risk, and some of the most serious risks may stem from strategic or process gaps rather than isolated technical flaws. Cyber risk management therefore emphasizes context, prioritization, and tradeoffs, helping leaders decide where to invest resources and which risks are acceptable.
From my perspective, the distinction between cyber risk and cybersecurity represents a maturation of the field. Cybersecurity is essential as the execution arm — it provides the tools and controls that protect assets. Cyber risk is the decision framework that ensures those efforts align with business objectives. Organizations that focus only on cybersecurity can become trapped in an cycle of chasing vulnerabilities without clear prioritization. Conversely, a cyber risk approach connects technical findings to measurable business outcomes, enabling informed decisions at the executive level. The strongest programs integrate both: cybersecurity delivers protection, while cyber risk guides strategy, investment, and governance so the organization can operate confidently amid uncertainty.


InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- AI in Cybersecurity: Building Proactive and Adaptive Digital Defense
- AI Exposure Readiness assessment: A Practical Framework for Identifying and Managing Emerging Risks
- Top 10 AI Governance Best Practices: A Practical Guide to Responsible AI
- From Chaos to Control: Building a Practical GRC Framework for Modern Organizations
- NIST CSF and ISO 27001: Reducing Security Chaos Through Layered Frameworks














![IT Vendor Risk Management A Complete Guide - 2021 Edition by [Gerardus Blokdyk]](https://m.media-amazon.com/images/I/41jZ5XeJBgL.jpg)





