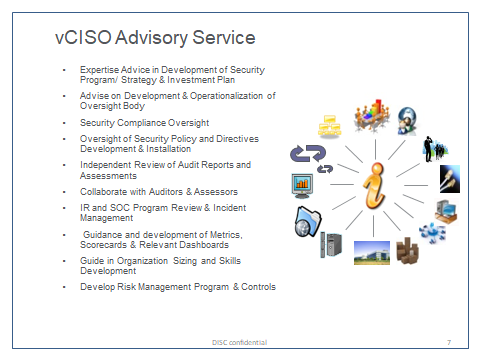
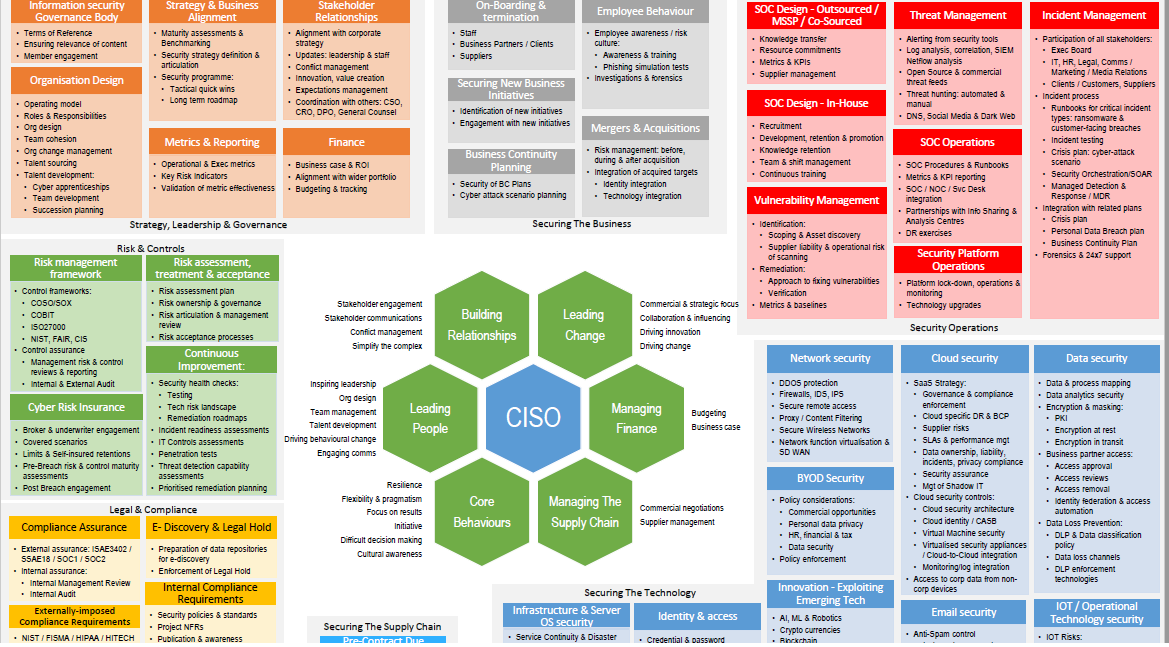
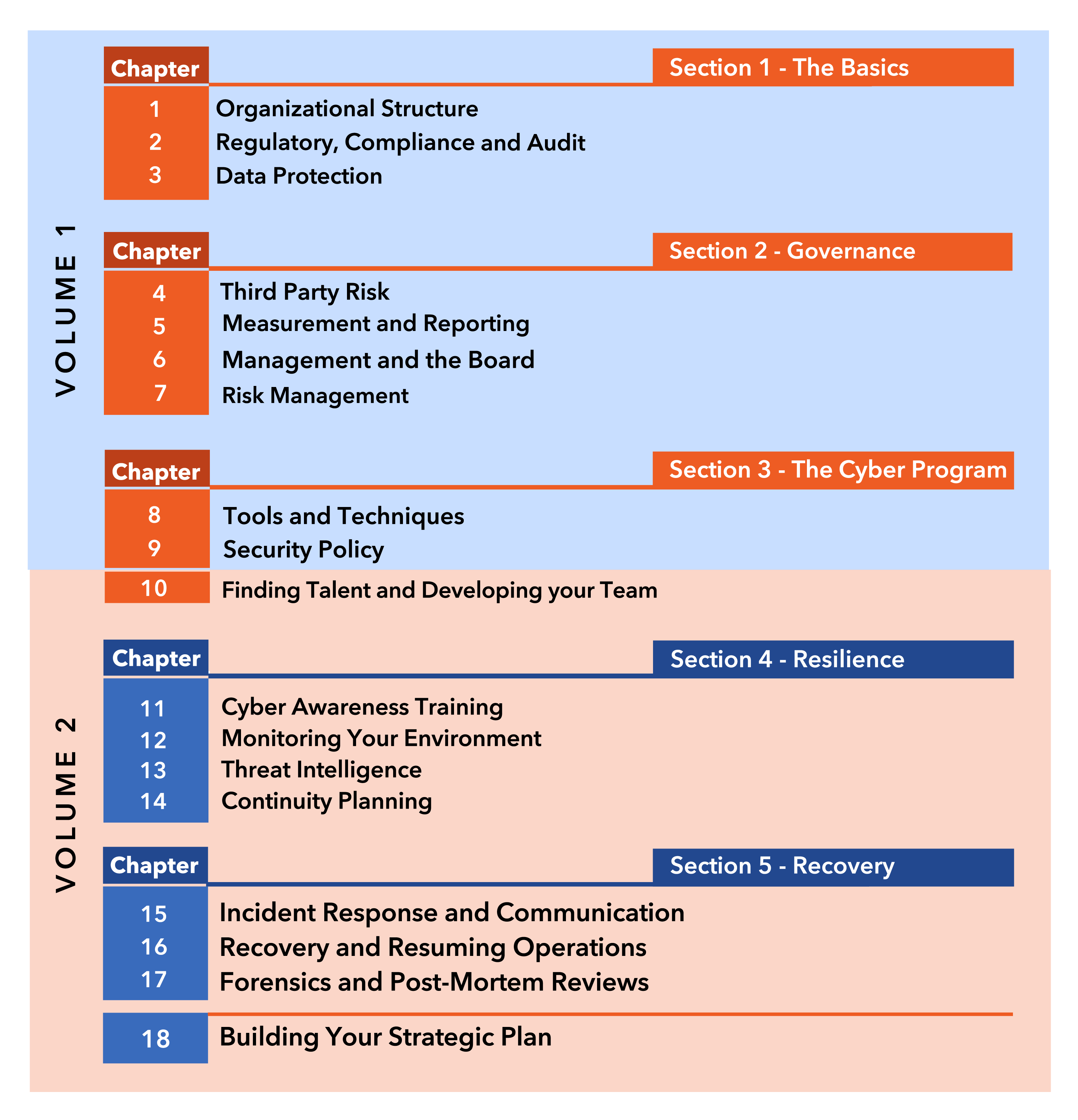
Here are five signs that a virtual CISO may be right for your organization.
1. You have a lot to protect
Companies produce more data than ever, and keeping track of it all is the first step to securing it. A virtual CISO can identify what data needs to be protected and determine the negative impact that compromised data can have, whether that impact is regulatory, financial or reputational.
2. Your organization is complex
Risk increases with employee count, but there are many additional factors that contribute to an organization’s complexity: the number of departments, offices and geographies; how data is used and shared; the distribution of architecture; and the life cycle of applications, data and the technology stack.
A virtual CISO offers an unbiased, objective view, and can sort out the complexity of a company’s IT architecture, applications and services. They can also determine how plans for the future add complexity, identify and account for the corresponding risk, and recommend security measures that will scale to support future demand.
3. Your attack surface is broad
For many organizations, potential vulnerabilities, especially those that share a great deal of data within the organization, may not be obvious at first glance. Virtual CISOs can identify both internal and external threats, determine their probability and quantify the impact they could have on your organization. And at a more granular level, they can determine if those same threats are applicable to competitors, which can help maintain competitiveness within your market.
4. Your industry is highly regulated
Organizations in regulated industries like healthcare, finance, energy/power and insurance will have data that is more valuable, which could make them a bigger target for bad actors. Exposure is even more of a concern due to potential noncompliance. Virtual CISOs bring a wealth of expertise on regulatory standards. They can implement processes to maintain compliance and offer recommendations based on updates to applicable rules and regulations.
5. Your risk tolerance is low
An organization without a great deal of sensitive data may have a much greater tolerance for risk than a healthcare provider or a bank, but an honest assessment is important in determining how much risk each organization should accept. A virtual CISO can coordinate efforts to examine perceived and actual risk, identify critical vulnerabilities and provide a better picture of risk exposure that can inform future decisions.
Cybersecurity is growing more complex, and organizations of all sizes, especially those in regulated industries, require a proven security specialist who can address the aforementioned challenges and ensure that technology and processes are in place to mitigate security risks.