I’ve been meaning to talk more about what I actually do, which is help the teams within Microsoft who are threat modeling (for our boxed software) to do their jobs better. Better means faster, cheaper or more effectively. There are good reasons to optimize for different points on that spectrum (of better/faster/cheaper) at different times in different products. One of the things that I’ve learned is that we ask a lot of developers, testers, and PMs here. They all have some exposure to security, but terms that I’ve been using for years are often new to them.
Larry Osterman is a longtime MS veteran, currently working in Windows audio. He’s been a threat modeling advocate for years, and has been blogging a lot about our new processes, and describes in great detail the STRIDE per element process. His recent posts are “Threat Modeling, Once Again,” “Threat modeling again. Drawing the diagram,” “Threat Modeling Again: STRIDE,” “Threat modeling again, STRIDE mitigations,” “Threat modeling again, what does STRIDE have to do with threat modeling,” “Threat modeling again, STRIDE per element,” “Threat modeling again, threat modeling playsound.”
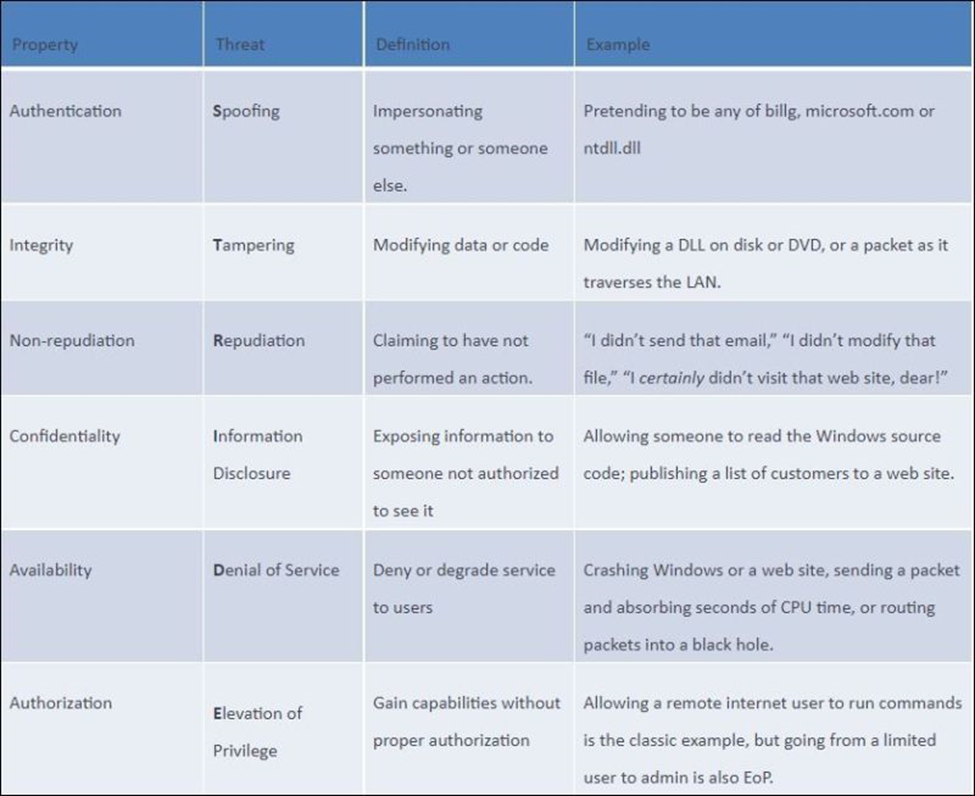
I wanted to chime in and offer up this handy chart that we use. It’s part of how we teach people to go from a diagram to a set of threats. We used to ask them to brainstorm, and have discovered that that works a lot better with some structure.
Source:



