Hackers have been found hijacking Facebook pages to impersonate popular AI brands, thereby injecting malware into the devices of unsuspecting users.
This revelation comes from a detailed investigation by Bitdefender Labs, which has been closely monitoring these malicious campaigns since June 2023.
Recent analyses of malvertising campaigns have revealed a disturbing trend.
Ads are distributing an assortment of malicious software, which poses severe risks to consumers’ devices, data, and identity.
Unwitting interactions with these malware-serving ads could lead to downloading and deploying harmful files, including Rilide Stealer, Vidar Stealer, IceRAT, and Nova Stealer, onto users’ devices.
Rilide Stealer V4: A Closer Look
Bitdefender Labs has spotlighted an updated version of the Rilide Stealer (V4) lurking within sponsored ad campaigns that impersonate popular AI-based software and photo editors such as Sora, CapCut, Gemini AI, Photo Effects Pro, and CapCut Pro.
This malicious extension, targeting Chromium-based browsers, is designed to monitor browsing history, capture login credentials, and even facilitate the withdrawal of crypto funds by bypassing two-factor authentication through script injections.
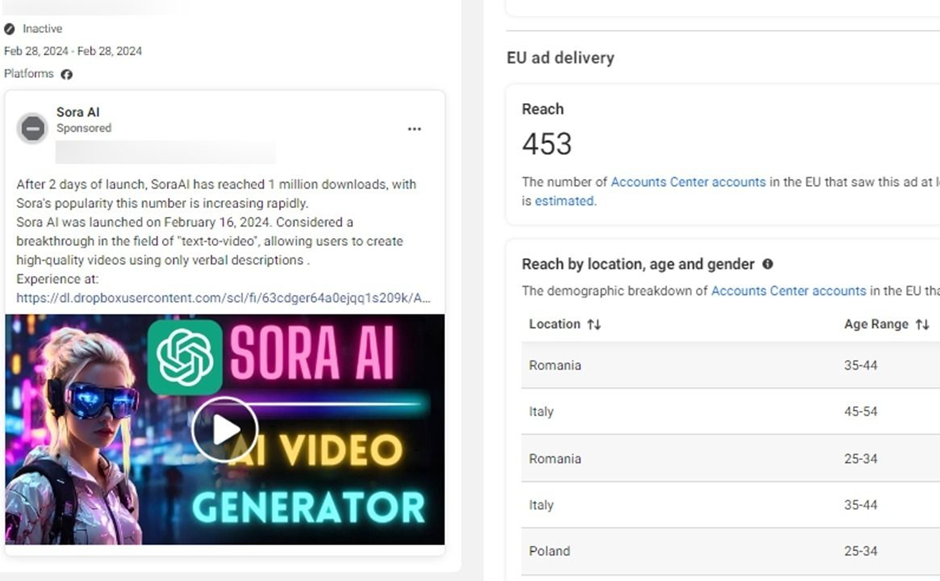
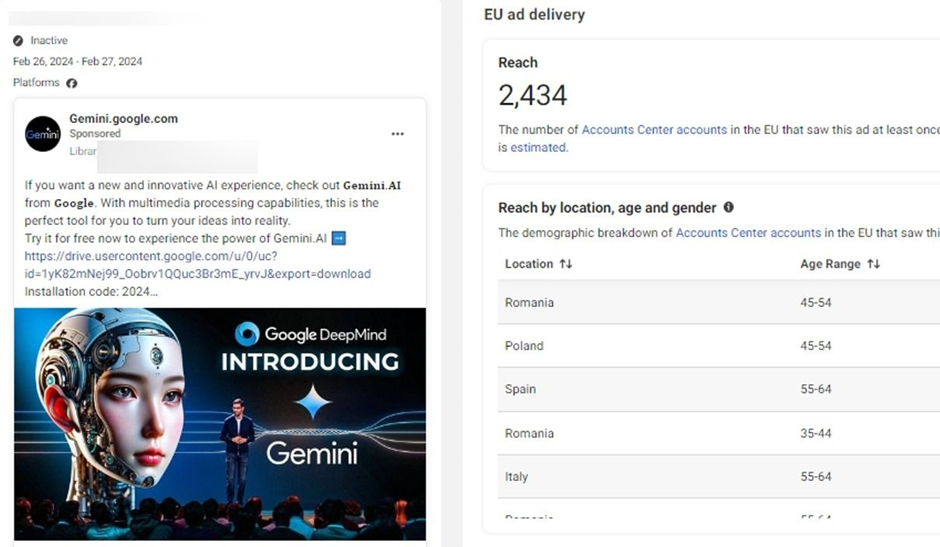
Key Updates in Rilide V4:
- Targeting of Facebook cookies
- Masquerading as a Google Translate Extension
- Enhanced obfuscation techniques to conceal the software’s true intent
Indicators Of Compromise
Malicious hashes
- 2d6829e8a2f48fff5348244ce0eaa35bcd4b26eac0f36063b9ff888e664310db – OpenAI Sora official version setup.msi – Sora
- a7c07d2c8893c30d766f383be0dd78bc6a5fd578efaea4afc3229cd0610ab0cf – OpenAI Sora Setup.zip – Sora
- e394f4192c2a3e01e6c1165ed1a483603b411fd12d417bfb0dc72bd6e18e9e9d – Setup.msi – Sora
- 021657f82c94511e97771739e550d63600c4d76cef79a686aa44cdca668814e0 – Setup.msi – Sora
- 92751fd15f4d0b495e2b83d14461d22d6b74beaf51d73d9ae2b86e2232894d7b – Setup.msi – Sora
- 32a097b510ae830626209206c815bbbed1c36c0d2df7a9d8252909c604a9c1f1 – Setup.msi – Sora
- c665ff2206c9d4e50861f493f8e7beca8353b37671d633fe4b6e084c62e58ed9 – Setup.msi – Sora
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e – Capcut Pro For PC.setup.msi – Capcut
- 757855fcd47f843739b9a330f1ecb28d339be41eed4ae25220dc888e57f2ec51 – OpenAI ChatGPT-4.5 Version Free.msi – ChatGPT
- 3686204361bf6bf8db68fd81e08c91abcbf215844f0119a458c319e92a396ecf – Google Gemini AI Ultra Version Updata.msi – Gemini AI
- d60ea266c4e0f0e8d56d98472a91dd5c37e8eeeca13bf53e0381f0affc68e78a – Photo Effects Pro v3.1.3 Setup.msi – Photo Effects
- bb7c3b78f2784a7ac3c090331326279476c748087188aeb69f431bbd70ac6407 – Photo Effects Pro v3.1.3 Setup.msi – Photo Effects
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e – AISora.setup.msi – Sora
Vidar Stealer: Evolving Threats
Vidar Stealer, another prolific info stealer, is marketed through the same MaaS model via dark web ads, forums, and Telegram groups.
Capable of exfiltrating personal information and crypto from compromised devices, Vidar’s distribution has evolved from spam campaigns and cracked software to malicious Google Search ads and social media platforms, mainly through sponsored ads on Meta’s platform.
Indicators Of Compromise
Malicious hashes
- 6396ac7b1524bb9759f434fe956a15f5364284a04acd5fc0ef4b625de35d766b- g2m.dll – MidJourney
- 76ed62a335ac225a2b7e6dade4235a83668630a9c1e727cf4ddb0167ab2202f6- Midjourney.7z – MidJourney
IceRAT: More Than Just A Trojan
Despite its name, IceRAT functions more as a backdoor on compromised devices. It acts as a gateway for secondary infections, such as crypto miners and information stealers that target login credentials and other sensitive data.
Indicators Of Compromise
Malicious hashes
- aab585b75e868fb542e6dfcd643f97d1c5ee410ca5c4c5ffe1112b49c4851f47- Midjourneyv6.exe – MidJourney
- b5f740c0c1ac60fa008a1a7bd6ea77e0fc1d5aa55e6856d8edcb71487368c37c- Midjourneyv6ai.exe – MidJourney
- cc15e96ec1e27c01bd81d2347f4ded173dfc93df673c4300faac5a932180caeb- Mid_Setup.exe – MidJourney
- d2f12dec801000fbd5ccc8c0e8ed4cf8cc27a37e1dca9e25afc0bcb2287fbb9a- Midjourney_v6.exe – MidJourney
- f2fc27b96a4a487f39afad47c17d948282145894652485f9b6483bec64932614-Midjourneyv6.1_ins.exe – MidJourney
- f99aa62ee34877b1cd02cfd7e8406b664ae30c5843f49c7e89d2a4db56262c2e – Midjourneys_Setup.exe – MidJourney
- 54a992a4c1c25a923463865c43ecafe0466da5c1735096ba0c3c3996da25ffb7 – Mid_Setup.exe – MidJourney
- 4a71a8c0488687e0bb60a2d0199b34362021adc300541dd106486e326d1ea09b- Mid_Setup.exe – MidJourney
Nova Stealer: The New Kid On The Block
Nova Stealer emerges as a highly proficient info stealer with capabilities including password exfiltration, screen recordings, discord injections, and crypto wallet hijacking.
Nova Stealer, offered as MaaS by the threat actor known as Sordeal, represents a significant threat to digital security.
Indicators Of Compromise
Malicious hashes
- fb3fbee5372e5050c17f72dbe0eb7b3afd3a57bd034b6c2ac931ad93b695d2d9- Instructions_for_using_today_s_AI.pdf.rar – AI and Life
- 6a36f1f1821de7f80cc9f8da66e6ce5916ac1c2607df3402b8dd56da8ebcc5e2- Instructions_for_using_today_s_AI.xlsx_rar.rar – AI and Life
- fe7e6b41766d91fbc23d31573c75989a2b0f0111c351bed9e2096cc6d747794b- Instructions for using today’s AI.pdf.exe – AI and Life
- ce0e41e907cab657cc7ad460a5f459c27973e9346b5adc8e64272f47026d333d- Instructions for using today’s AI.xlsx.exe – AI and Life
- a214bc2025584af8c38df36b08eb964e561a016722cd383f8877b684bff9e83d- 20 digital marketing tips for 2024.xlsx.exe – Google Digital Marketing
- 53714612af006b06ca51cc47abf0522f7762ecb1300e5538485662b1c64d6f55 – Premium advertising course registration form from Oxford.exe – Google Digital Marketing
- 728953a3ebb0c25bcde85fd1a83903c7b4b814f91b39d181f0fc610b243c98d4- New Microsoft Excel Worksheet.exe – Google Digital Marketing
The Midjourney Saga: AI’s Dark Side
The addition of AI tools on the internet, from free offerings and trials to subscription-based services, has not gone unnoticed by cybercriminals.
Midjourney, a leading generative AI tool with a user base exceeding 16 million as of November 2023, has become a favored tool among cyber gangs over the past year, highlighting the intersection of cutting-edge technology and cybercrime.

Indicators Of Compromise
- 159.89.120.191
- 159.89.98.241
As the digital landscape continues to evolve, so does the nature of the threats it maintains.
The rise of Malware-as-a-Service represents a significant shift in the cyber threat paradigm that requires vigilant and proactive measures to combat.
Key Updates in Rilide V4:
- Targeting of Facebook cookies
- Masquerading as a Google Translate Extension
- Enhanced obfuscation techniques to conceal the software’s true intent
Indicators Of Compromise
Malicious hashes
- 2d6829e8a2f48fff5348244ce0eaa35bcd4b26eac0f36063b9ff888e664310db – OpenAI Sora official version setup.msi – Sora
- a7c07d2c8893c30d766f383be0dd78bc6a5fd578efaea4afc3229cd0610ab0cf – OpenAI Sora Setup.zip – Sora
- e394f4192c2a3e01e6c1165ed1a483603b411fd12d417bfb0dc72bd6e18e9e9d – Setup.msi – Sora
- 021657f82c94511e97771739e550d63600c4d76cef79a686aa44cdca668814e0 – Setup.msi – Sora
- 92751fd15f4d0b495e2b83d14461d22d6b74beaf51d73d9ae2b86e2232894d7b – Setup.msi – Sora
- 32a097b510ae830626209206c815bbbed1c36c0d2df7a9d8252909c604a9c1f1 – Setup.msi – Sora
- c665ff2206c9d4e50861f493f8e7beca8353b37671d633fe4b6e084c62e58ed9 – Setup.msi – Sora
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e – Capcut Pro For PC.setup.msi – Capcut
- 757855fcd47f843739b9a330f1ecb28d339be41eed4ae25220dc888e57f2ec51 – OpenAI ChatGPT-4.5 Version Free.msi – ChatGPT
- 3686204361bf6bf8db68fd81e08c91abcbf215844f0119a458c319e92a396ecf – Google Gemini AI Ultra Version Updata.msi – Gemini AI
- d60ea266c4e0f0e8d56d98472a91dd5c37e8eeeca13bf53e0381f0affc68e78a – Photo Effects Pro v3.1.3 Setup.msi – Photo Effects
- bb7c3b78f2784a7ac3c090331326279476c748087188aeb69f431bbd70ac6407 – Photo Effects Pro v3.1.3 Setup.msi – Photo Effects
- 0ed3b92fda104ac62cc3dc0a5ed0f400c6958d7034e3855cad5474fca253125e – AISora.setup.msi – Sora
Vidar Stealer: Evolving Threats
Vidar Stealer, another prolific info stealer, is marketed through the same MaaS model via dark web ads, forums, and Telegram groups.
Capable of exfiltrating personal information and crypto from compromised devices, Vidar’s distribution has evolved from spam campaigns and cracked software to malicious Google Search ads and social media platforms, mainly through sponsored ads on Meta’s platform.
Indicators Of Compromise
Malicious hashes
- 6396ac7b1524bb9759f434fe956a15f5364284a04acd5fc0ef4b625de35d766b- g2m.dll – MidJourney
- 76ed62a335ac225a2b7e6dade4235a83668630a9c1e727cf4ddb0167ab2202f6- Midjourney.7z – MidJourney
IceRAT: More Than Just A Trojan
Despite its name, IceRAT functions more as a backdoor on compromised devices. It acts as a gateway for secondary infections, such as crypto miners and information stealers that target login credentials and other sensitive data.
Indicators Of Compromise
Malicious hashes
- aab585b75e868fb542e6dfcd643f97d1c5ee410ca5c4c5ffe1112b49c4851f47- Midjourneyv6.exe – MidJourney
- b5f740c0c1ac60fa008a1a7bd6ea77e0fc1d5aa55e6856d8edcb71487368c37c- Midjourneyv6ai.exe – MidJourney
- cc15e96ec1e27c01bd81d2347f4ded173dfc93df673c4300faac5a932180caeb- Mid_Setup.exe – MidJourney
- d2f12dec801000fbd5ccc8c0e8ed4cf8cc27a37e1dca9e25afc0bcb2287fbb9a- Midjourney_v6.exe – MidJourney
- f2fc27b96a4a487f39afad47c17d948282145894652485f9b6483bec64932614-Midjourneyv6.1_ins.exe – MidJourney
- f99aa62ee34877b1cd02cfd7e8406b664ae30c5843f49c7e89d2a4db56262c2e – Midjourneys_Setup.exe – MidJourney
- 54a992a4c1c25a923463865c43ecafe0466da5c1735096ba0c3c3996da25ffb7 – Mid_Setup.exe – MidJourney
- 4a71a8c0488687e0bb60a2d0199b34362021adc300541dd106486e326d1ea09b- Mid_Setup.exe – MidJourney
Nova Stealer: The New Kid On The Block
Nova Stealer emerges as a highly proficient info stealer with capabilities including password exfiltration, screen recordings, discord injections, and crypto wallet hijacking.
Nova Stealer, offered as MaaS by the threat actor known as Sordeal, represents a significant threat to digital security.
Indicators Of Compromise
Malicious hashes
- fb3fbee5372e5050c17f72dbe0eb7b3afd3a57bd034b6c2ac931ad93b695d2d9- Instructions_for_using_today_s_AI.pdf.rar – AI and Life
- 6a36f1f1821de7f80cc9f8da66e6ce5916ac1c2607df3402b8dd56da8ebcc5e2- Instructions_for_using_today_s_AI.xlsx_rar.rar – AI and Life
- fe7e6b41766d91fbc23d31573c75989a2b0f0111c351bed9e2096cc6d747794b- Instructions for using today’s AI.pdf.exe – AI and Life
- ce0e41e907cab657cc7ad460a5f459c27973e9346b5adc8e64272f47026d333d- Instructions for using today’s AI.xlsx.exe – AI and Life
- a214bc2025584af8c38df36b08eb964e561a016722cd383f8877b684bff9e83d- 20 digital marketing tips for 2024.xlsx.exe – Google Digital Marketing
- 53714612af006b06ca51cc47abf0522f7762ecb1300e5538485662b1c64d6f55 – Premium advertising course registration form from Oxford.exe – Google Digital Marketing
- 728953a3ebb0c25bcde85fd1a83903c7b4b814f91b39d181f0fc610b243c98d4- New Microsoft Excel Worksheet.exe – Google Digital Marketing
The Midjourney Saga: AI’s Dark Side
The addition of AI tools on the internet, from free offerings and trials to subscription-based services, has not gone unnoticed by cybercriminals.
Midjourney, a leading generative AI tool with a user base exceeding 16 million as of November 2023, has become a favored tool among cyber gangs over the past year, highlighting the intersection of cutting-edge technology and cybercrime.

Indicators Of Compromise
- 159.89.120.191
- 159.89.98.241
As the digital landscape continues to evolve, so does the nature of the threats it maintains.
The rise of Malware-as-a-Service represents a significant shift in the cyber threat paradigm that requires vigilant and proactive measures to combat.
The Complete Guide to Software as a Service: Everything you need to know about SaaS
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot



