It is commonly believed that an asset-based information security risk assessment provides a thorough and comprehensive approach to conducting a risk assessment, and this article will look at the steps to follow when conducting this type of risk assessment.
Where do you start when you embark on an asset-based information security risk assessment?
The first step would be to produce an asset register, which can be done through a series of interviews with asset owners. The ‘asset owner’ is an individual or entity that has responsibility for controlling the production, development, maintenance, use and security of an information asset.
Note: In the new standard, ISO 27001:2013, there is a stronger emphasis on the role of the ‘risk owner’, which pushes up the responsibility for the risks to a higher level within the organisation. However, since the approach we are following is an asset-based methodology, the asset owner would be the logical point to start in order to compile an asset register.
Once the asset register has been compiled, the next step is to identify any potential threats and vulnerabilities that could pose risks to those assets. A vulnerability / weakness of an asset or control can be defined as one that can be exploited by one or more threats.
Risk assessment & impact determination
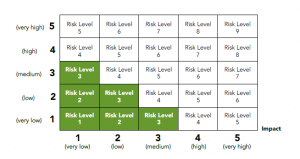
Once the threats and vulnerabilities have been identified, then an analysis of the risks should be undertaken, to establish the impact level of the risks. The impact value needs to take into consideration how the Confidentiality, Integrity and Availability of data can be affected by each of the risks.
It should also consider the business, legal, contractual and regulatory implications of risks, including the cost of the replacement of the asset, the potential loss of income, fines and reputational damage.
ISO 27005 presents a structured, systematic and rigorous process of analysing risks, and for creating the risk treatment plan, and includes a list of known threats and vulnerabilities that can be used for establishing the risks your information assets are exposed to.
vsRisk comes with an optional, pre-populated asset library. Organisational roles are pre-assigned to each asset group, and the corresponding potential threats / risks are pre-applied to each asset. vsRisk also pre-assigns the relevant controls from Annex A to each threat. See sample below. View options to purchase vsRisk now.

vsRisk™ provides key benefits for anyone undertaking an asset-based risk assessment.
By providing a simple framework and process to follow, vsRisk minimises the manual hassle and complexity of carrying out an information security risk assessment, saving the risk assessor time and resources. In addition, once the assessment has been completed, the risk assessments can be repeated easily in a standard format year after year. The tool generates a set of 6 reports that can be exported and edited, presented to management and audit teams, and includes pre-populated databases of threats and vulnerabilities as well as 7 different control sets that can be applied to treat the risks.























