
MITRE ATT&CK for dummies
How to Improve Threat Detection and Hunting in the AWS Cloud Using the MITRE ATT&CK® Matrix
InfoSec and Compliance – With 20 years of blogging experience, DISC InfoSec blog is dedicated to providing trusted insights and practical solutions for professionals and organizations navigating the evolving cybersecurity landscape. From cutting-edge threats to compliance strategies, this blog is your reliable resource for staying informed and secure. Dive into the content, connect with the community, and elevate your InfoSec expertise!
Dec 13 2021
Nov 08 2021
According to the Verizon 2021 Data Breach Investigations Report, insiders are responsible for around 22% of security incidents. That is clearly a significant number and insider threats are quickly becoming one of the most common cybersecurity threats organizations face today. The challenge that continues to remain high with insider threats is that it is difficult to differentiate between normal and abnormal user behavior for any user since they already have access to the environment compared to external threats. Therefore, it makes a very important case to correlate content, threat and behavior to make an accurate prediction for an insider threat.
The significance of insider threats can be seen in the last update by MITRE where the version of ATT&CK for Enterprise contains 14 Tactics, 185 Techniques, and 367 Sub-techniques, among which are those used in insider threat attacks. In this analysis, we’ll look at a selection of the techniques published in the update and examine how they are used, the motivations and the types of attacks they are used for.
An insider threat is a security threat that originates internally from within an organization. It’s usually someone who uses their authorized access—intentionally or unintentionally—to compromise an organization’s network, data or devices. Due to the authorized access, the attacker doesn’t need to raise a request or hack some credentials to gain access. There are three most common categories of an inside attacker.
Let’s take a look at some of the recent insider attacks to understand the magnitude of the impact. – Updated MITRE ATT&CK TTPs Used in Insider Threat Attacks
ATT&CK™ Framework and open source tools

Oct 29 2021

Historically, vulnerability management and threat management have been separate disciplines, but in a risk-focused world, they need to be brought together. Defenders struggle to integrate vulnerability and threat information and lack a consistent view of how adversaries use vulnerabilities to achieve their goals. Without this context, it is difficult to appropriately prioritize vulnerabilities.
To bridge vulnerability management and threat management, the Center for Threat-Informed Defense, with support from participants including AttackIQ and JP Morgan Chase, developed a methodology to use the adversary behaviors described in MITRE ATT&CK® to characterize the impact of vulnerabilities from CVE®. Vulnerability reporters and researchers can use the methodology to describe the impact of vulnerabilities more clearly and consistently. When used in a vulnerability report, ATT&CK’s tactics and techniques enable defenders to quickly understand how a vulnerability can impact them, helping defenders integrate vulnerability information into their risk models and identify appropriate compensating security controls.
This methodology aims to establish a critical connection between vulnerability management, threat modeling, and compensating controls. CVEs linked to ATT&CK techniques can empower defenders to better assess the true risk posed by specific vulnerabilities in their environment. We have applied the methodology and mapped several hundred CVEs to ATT&CK to validate the model and demonstrated its value. To fully realize our goal, we need community support to apply the methodology at scale.
Mitre Att&ck Framework: Everything you need to know by Peter Buttler
Practical Threat Intelligence and Data-Driven Threat Hunting: A hands-on guide to threat hunting with the ATT&CK™ Framework and open source tools

Oct 25 2021
MITRE Corporation has released the tenth version of ATT&CK, its globally accessible (and free!) knowledge base of cyber adversary tactics and techniques based on real-world observations.
Version ten comes with new Data Source objects, new and changed techniques in its various matrices, key changes to facilitate hunting in ICS environments, and more.

The most prominent change in this newest version of the framework is new objects with aggregated information about data sources.
“The data source object features the name of the data source as well as key details and metadata, including an ID, a definition, where it can be collected (collection layer), what platform(s) it can be found on, and the data components highlighting relevant values/properties that comprise the data source,” MITRE ATT&CK Content Lead Amy L. Robertson and cybersecurity engineers Alexia Crumpton and Chris Ante explained.
“These data sources are available for all platforms of Enterprise ATT&CK, including our newest additions that cover OSINT-related data sources mapped to PRE platform techniques.”
Changes in ATT&CK for ICS and the Mobile matrices are focused on providing all the features currently provided in the Enterprise matrices.
“v10 also includes cross-domain mappings of Enterprise techniques to software that were previously only represented in the ICS Matrix, including Stuxnet, Industroyer, and several others. The fact that adversaries don’t respect theoretical boundaries is something we’ve consistently emphasized, and we think it’s crucial to feature Enterprise-centric mappings for more comprehensive coverage of all the behaviors exhibited by the software,” they added.
The complete release notes for MITRE ATT&CK v10 can be found here.
Jun 23 2021
MITRE Engenuity has released ATT&CK Workbench, an open source tool that allows organizations to customize their local instance of the MITRE ATT&CK database of cyber adversary behavior.

The tool allows users to add notes, and create new or extend existing objects – matrices, techniques, tactics, mitigations, groups, and software – with new content. It also allows them to share these insights with other organizations.
Apr 29 2021

We’re excited to announce the official release of ATT&CK for Containers! This release marks the culmination of a Center for Threat-Informed Defense (Center) research project sponsored by Citigroup, JPMorgan Chase, and Microsoft that investigated the viability of adding container-related techniques into ATT&CK. This investigation led to developing a draft of an ATT&CK for Containers matrix, which we contributed to ATT&CK. Our contribution was accepted and is now live in ATT&CK version 9.0! We want to give a special thank you to the community for all of your feedback and help in developing this content. Creating ATT&CK for Containers has been a fun journey for us, with a lot of new faces and names along the way. You’ll notice a lot of new contributors in ATT&CK with this release, which is in part a testament to how many folks helped us scope and create this new platform in ATT&CK!
For more on: Why did container-related techniques get added to ATT&CK?
Apr 09 2021
When selecting an attack detection solution, no single product will provide the adequate detection needed that is required to detect and defend against the current advanced threat landscape. The holistic aspect of defending against threat actors requires technology, expertise, and intelligence.
The technology should be a platform of integrated technologies providing detection at each point of entry that a threat actor may use such as email, endpoint, network, and public cloud. These should not be disparate technologies that don’t work together to holistically defend the organization.
We must use technologies that can scale against threat actors that have a very large number of resources. The technology should also be driven by intelligence cultivated from the frontlines where incident responders have an unmatched advantage. It is also important to remember that post-exploitation, threat actors masquerade as your own employee’s making it difficult to know legitimate from non-legitimate activity occurring on the network or your endpoints.
This is where intelligence and expertise is extremely valuable to determine when a threat actor is operating within the organization. Being able to identify the threat actors “calling card” and potential next moves, is paramount. While many solutions will claim they defend against advanced threats, it is important to understand the experience that a vendor has and how that is included into their product offering.
How do I select an attack detection solution for my business?

Mar 31 2021
Ismael Valenzuela (McAfee/SANS) and Vicente Diaz (Threat Intel Strategist at Virustotal)
SANS Institute‘s #SEC530 course co-authored by Ismael Valenzuela (@aboutsecurity), providing students access to VTIntelligence to help them make TTPs actionable.
MITRE Enterprise ATT&CK Framework
Comparing Layers in ATT&CK Navigator – MITRE ATT&CK®
Mar 23 2021
MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.
With the creation of ATT&CK, MITRE is fulfilling its mission to solve problems for a safer world — by bringing communities together to develop more effective cybersecurity. ATT&CK is open and available to any person or organization for use at no charge.
Mar 22 2021

A recent article from Gartner states that, “Audit Chiefs Identify IT Governance as Top Risk for 2021.” I agree that IT governance is important but I question how much does the IT governance board understand about the day to day tactical risks such as the current threats and vulnerabilities against a companies attack surface? How are the tactical risks data being reported up to the board? Does the board understand the current state of threats and vulnerabilities or is this critical information being filtered on the way up?
If the concept of hierarchy of needs was extended to cyber security it may help business owners and risk management teams asses how to approach implementing a risk management approach for the business.
There are three key questions to ask:

Layers 1-2 – Inventory and Telemetry – The first two layers are related to asset inventory which is part of the CIS Controls 1-2. How can you defend the vulnerable Windows 2003 server that is still connected to your network at a remote site?
Layers 3-4 – Detection and Triage – These layers are related to a SOC/SIEM/SOAR program which will allow the cyber security team to begin to detect threats through logging and monitoring.
Layers 5-10 – Threats, Behaviors, Hunt, Track, Act – The final layers are threat hunting, tracking and incident response and this is where the MITRE framework is very helpful to identify threats, understand the data sources, build use cases and prepare the incident response playbooks based on real world threat intelligence.
To more about What is the MITRE’s Att&CK Framework? Source: The MITRE Att&CK Framework
Mar 11 2021
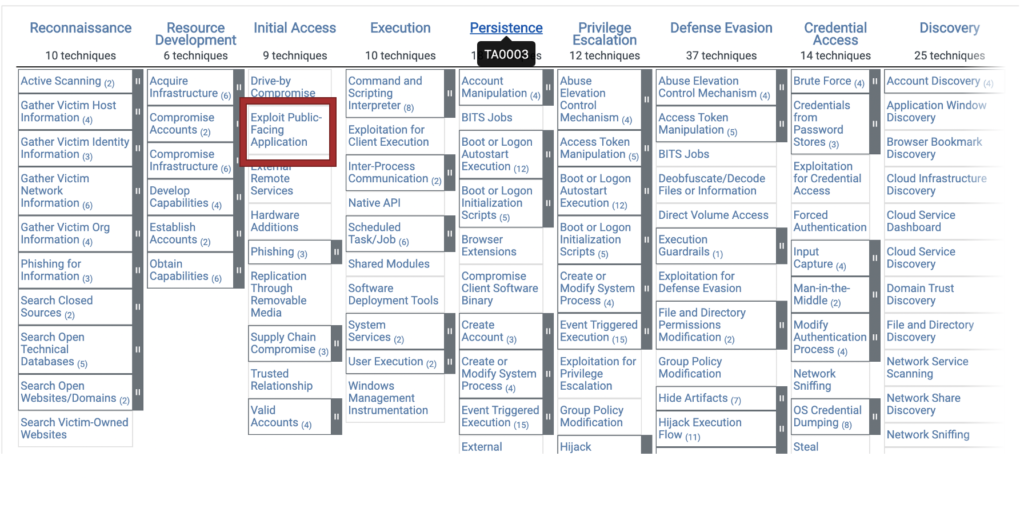
MITRE ATT&CK matrices
MITRE ATT&CK is a tool to help cybersecurity teams get inside the minds of threat actors to anticipate their lines of attack and most effectively position defenses. MITRE ATT&CK works synergistically with FAIR to refine a risk scenario (“threat actor uses a method to attack an asset resulting in a loss”).
Enter an asset into the MITRE ATT&CK knowledge base and it returns a list of likely threat actors and their methods to inform a risk scenario statement. It also helps to fill in color and detail for the FAIR factors, such as the relative strength of threat actors likely to go after an asset or the resistance strength of the controls around the asset, as well as the frequency of attack one might expect from these actors, based on internal or industry data (housed in the Data Helpers and Loss Tables on the RiskLens platform). All these are ultimately fed into the Monte Carlo simulation engine to show probable loss exposure for the scenario. The data we collect on our assets and threat actors can be stored in libraries on the platform for repeat use.
MITRE ATT&CK also suggests controls for mitigation efforts specific to attacks. As with the controls suggested by NIST CSF, we can assess those in the platform for cost-effectiveness in risk reduction in financial terms.
Finally, RiskLens + MITRE ATT&CK can help refine tactics for the first line of defense. With a clear sense of top risk scenarios generated by RiskLens, and a clear sense of attack vectors for those scenarios, the SOC can better prioritize among the many incoming alerts based on potential bottom-line impact.
Feb 02 2021
The natural inclination of most security teams when looking at MITRE ATT&CK is to try and develop some kind of detection or prevention control for each technique in the enterprise matrix. While this isn’t a terrible idea, the nuances of ATT&CK make this approach a bit dangerous if certain caveats aren’t kept in mind. Techniques in the ATT&CK matrices can often be performed in a variety of ways. So blocking or detecting a single way to perform them doesn’t necessarily mean that there is coverage for every possible way to perform that technique. This can lead to a false sense of security thinking that because a tool blocks one form of employing a technique that the technique is properly covered for the organization. Yet attackers can still successfully employ other ways to employ that technique without any detection or prevention in place.
The way to address this is the following:
For example, if antivirus detects the presence of Mimikatz, that doesn’t mean that Pass the Hash (T1075) and Pass the Ticket (T1097) are covered as there are still several other ways to perform these techniques that don’t involve the use of Mimikatz. Keep this in mind if trying to use ATT&CK to show defensive coverage in an organization.
Source: Use ATT&CK to map defenses and understand gaps

The new MITRE ATT&CK™ tool helps security practitioners to build an Attempted Attack Matrix —
To know more about MITRE Attack Metrics

SANS-Measuring-and-Improving-Cyber-Defense-MITRE-ATTCK-Anomali-Report