https://www.mandiant.com/resources/blog/infected-usb-steal-secrets
In the first half of 2023, Mandiant Managed Defense has observed a threefold increase in the number of attacks using infected USB drives to steal secrets. Mandiant tracked all of the cases and found that the majority of the incidents could be attributed to several active USB-based operation campaigns affecting both the public and private sectors globally.
Previously, we covered one of the campaigns that leverages USB flash drives as an initial infection vector and concentrates on the Philippines. In this blog post, we are covering two additional USB-based cyber espionage campaigns that have been observed by Managed Defense:
- SOGU Malware Infection via USB Flash Drives Across Industries and Geographies
This is the most prevalent USB-based cyber espionage attack using USB flash drives and one of the most aggressive cyber espionage campaigns targeting both public and private sector organizations globally across industry verticals. It uses USB flash drives to load the SOGU malware to steal sensitive information from a host.
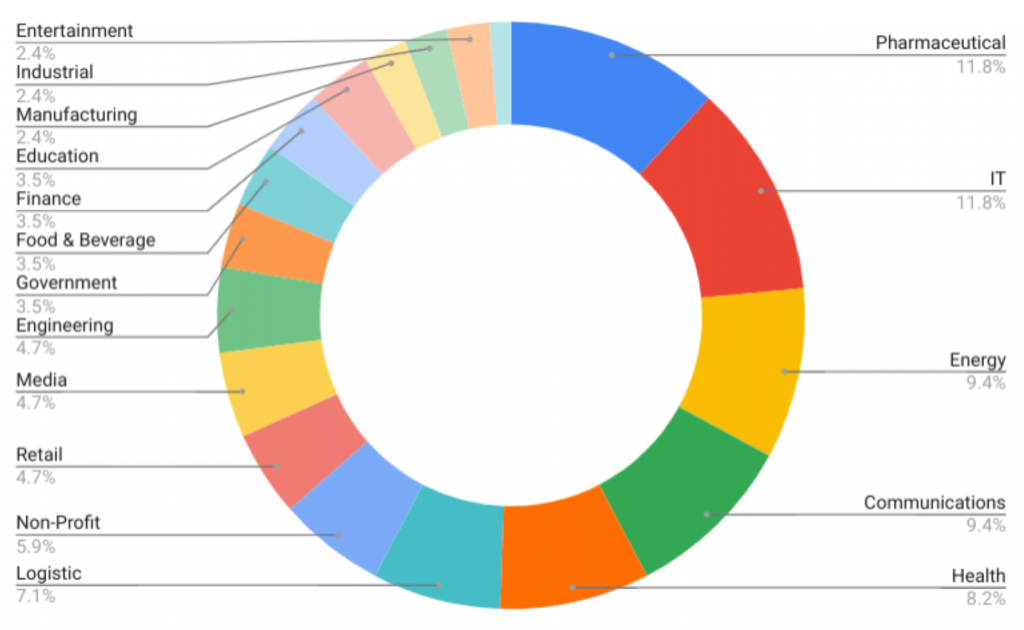
Mandiant attributes this campaign to TEMP.Hex, a China-linked cyber espionage actor. TEMP.Hex likely conducted these attacks to collect information in support of Chinese national security and economic interests. These operations pose a risk to a variety of industries, including construction and engineering, business services, government, health, transportation, and retail in Europe, Asia, and the United States.
- SNOWYDRIVE Malware Infection via USB Flash Drives, Targets Oil and Gas Organizations in Asia
This campaign uses USB flash drives to deliver the SNOWYDRIVE malware. Once SNOWYDRIVE is loaded, it creates a backdoor on the host system, giving attackers the ability to remotely issue system commands. It also spreads to other USB flash drives and propagates throughout the network.
Mandiant attributes this campaign to UNC4698, a threat actor that has targeted oil and gas organizations in Asia. Once the actor has gained access to the system, they execute arbitrary payloads using the Windows Command Prompt, use removable media devices, create local staging directories, and modify the Windows registry.
SOGU Malware Infection via USB Flash Drives Across Industries and Geographies
Pegasus: How a Spy in Your Pocket Threatens the End of Privacy, Dignity, and Democracy
InfoSec tools | InfoSec services | InfoSec books



