How to Implement ISO 27001: A 9-Step Guide
The hardest part of many projects is knowing where to start.
ISO 27001 is no exception. This standard describes best practice for an ISMS (information security management system).
In other words, it lays out the requirements you must meet, but doesn’t show you the how. How you can adopt or implement them.
With ISO 27001:2013 certification no longer available, many organisations are preparing to adopt the 2022 version of the standard – which means tackling a new Annex A control set, among other new requirements.
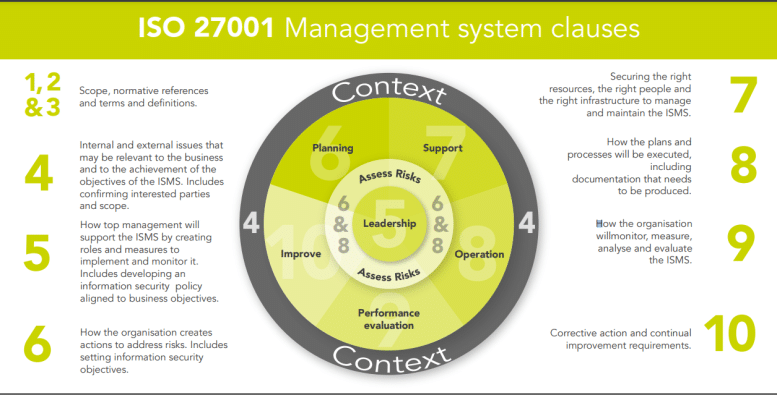
1. Project mandate
The implementation project should begin by appointing a project leader.
They’ll work with other members of staff to create a project mandate, which is essentially a set of answers to these questions:
- What do we hope to achieve?
- How long will the project take?
- Does the project have top management support?
- What resources – financial and otherwise – will the project need?
2. Develop the ISO 27001 implementation plan
The next step is to use your project mandate to create a more detailed outline of:
- Your information security objectives;
- Your project risk register;
- Your project plan; and
- Your project team.
Information security objectives
Your information security objectives should be more granular and specific than your answer to ‘What do we hope to achieve?’ from step 1.
They’ll inform and be included in your top-level information security policy. They’ll also shape how the ISMS is applied.
Project risk register
Your project risk register should account for risks to the project itself, which might be:
- Managerial – will operational management continue to support the project?
- Budgetary – will funding continue to see the project through?
- Legal – are specific legal obligations at risk?
- Cultural – will staff resist change?
Each risk in the register should have an assigned owner and a mitigation plan. You should also regularly review the risks throughout the project.
Project plan
The project plan should detail the actions you must take to implement the ISMS.
This should include the following information:
- Resources required
- Responsibilities
- Review dates
- Deadlines
Project team
The project team should represent the interests of every part of the organisation and include various levels of seniority.
Drawing up a RACI matrix can help with this. This identifies, for the project’s key decisions, who’s:
- Responsible;
- Accountable;
- Consulted; and
- Informed.
One critical person to appoint and include in the project team is the information security manager. They’ll have a central role in the implementation project and eventually be responsible for the day-to-day functioning of the ISMS.
3. ISMS initiation
You’re now ready to initiate your ISMS!
Documentation structure
A big part of this is establishing your documentation structure – any management system is very policy- and procedure-driven.
We recommend a four-tier approach:
A. Policies
These are at the top of the ‘pyramid’, defining your organisation’s position and requirements.
B. Procedures
These enact the requirements of your policies at a high level.
C. Work instructions
These set out how employees implement individual elements of the procedures.
D. Records
These track the procedures and work instructions, providing evidence that you’re following them consistently and correctly.
This structure is simple enough for anyone to grasp quickly. At the same time, it provides an effective way of ensuring you implement policies at each level of your organisation. Plus, that you develop well-functioning, cohesive processes.
Tips for more effective policies and procedures
Your policies and procedures must also be effective. Here are four tips:
- Keep them practicable by balancing aspirations against the reality. If your policies and/or procedures appear too idealised, staff will be much less likely to follow them.
- Keep them clear and straightforward, so staff can easily follow your procedures.
- Use version control, so everyone knows which is the latest document.
- Avoid duplication. This will also help with the version control.
Make sure you systematically communicate your documentation – particularly new or updated policies – throughout your organisation. Be sure to also communicate them to other stakeholders.
Continual improvement
As part of your ISMS initiation, you’ll need to select a continual improvement methodology.
First, understand that continual improvement might sound expensive, but is cost-effective if done well. As ISO 27001 pioneer Alan Calder explains:
Continual improvement means getting better results for your investment. That typically means one of two things:
1. Getting the same results while spending less money.
2. Getting better results while spending the same amount of money.Yes, you need to be looking at your objectives, and asking yourself how well your ISMS is currently meeting them. And where your management system falls short, money may have to be spent.
But many improvements have little financial cost. You can make a process more efficient – perhaps by cutting out a step, or automating some manual work.
While continual improvement is a critical element of an ISO 27001 ISMS, the Standard doesn’t specify any particular continual improvement methodology.
Instead, you can use whatever method you wish, so long as it continually improves the ISMS’s “suitability, adequacy and effectiveness” (Clause 10.1). That can include a continual improvement model you’re already using for another activity.
ISO 27001 Standard, Risk Assessment and Gap Assessment
ISO 27001 standards and training
Key strategies for ISO 27001:2022 compliance adoption
Implementation Guide ISO/IEC 27001:2022
Please send an email related to ISO27001:2022 implementation to info@DeuraInfoSec.com and we are happy to help!
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot



