The Polish computer emergency response team CERT.pl has issued a warning about an ongoing cyberattack campaign by the notorious APT28 hacking group, also known as Fancy Bear or Sofacy. The campaign is targeting various Polish government institutions with a new strain of malware.
According to the CERT.pl analysis, the attack begins with spear-phishing emails containing malicious attachments or links.
The malware is deployed once the victim opens the attachment or clicks the link, establishing a foothold in the targeted network.
Subject: I solved your problem
Hello Paweł!
I did a little research and found this mysterious Ukrainian woman.
Now she is in Warsaw.
She runs a rather unusual company that sells used underwear.
also has clients from senior authorities in Poland and Ukraine.
All information on this subject is available at this link - ALINA-BOKLAN (Link)Threat actors are increasingly using free, commonly-used services like run.mocky.io and webhook.site to deliver malware while evading detection.
This technique involves redirecting through these services to obfuscate the final malicious payload. The link first goes to run.mocky.io, a free API testing service, which then redirects to webhook.site for logging requests.
A ZIP archive disguised as an image file (e.g. IMG-238279780.zip) is downloaded from webhook.site.
With default Windows settings hiding extensions and hidden files, the victim sees the ZIP as an image, potentially leading them to open the malicious payload.
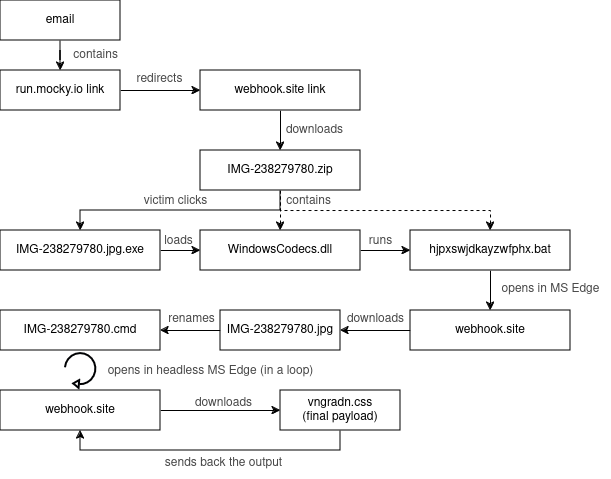
Using free services reduces costs and makes malicious links harder to flag as they blend in with legitimate developer traffic. This stealthy approach is becoming a trend across many APT groups.
“The malware used in this campaign is a new variant of the X-Agent backdoor, which allows the attackers to execute arbitrary commands, exfiltrate data, and move laterally within the compromised network,” explained CERT.pl in their report.
CERT.pl urges all Polish government agencies and critical infrastructure operators to remain vigilant and implement security measures.
APT28 is a highly sophisticated cyber-espionage group believed to be associated with the Russian military intelligence agency GRU.
The group has been active since at least 2007 and has been linked to numerous high-profile cyberattacks, including the 2016 Democratic National Committee email leak and the 2017 NotPetya ransomware outbreak.
This latest campaign highlights the persistent threat posed by state-sponsored hacking groups and the importance of maintaining robust cybersecurity measures, especially for critical government and infrastructure systems.
The report details the attack flow, providing indicators of compromise (IOCs) and recommendations for detecting and mitigating the threat.

The Bear Roars: Russia’s Cyber Spies And Global Threat To Security
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot



