Researchers from Google’s Threat Analysis Group (TAG) presented their findings in the company’s Threat Horizons Report. Their findings showed that the hacking group APT41 was misusing the GC2 red teaming tool in its attacks. GC2, also known as Google Command and Control, is an open-source project that was built specifically for red teaming operations. It was written in the programming language Go. GC2 (Google Command and Control) is an application for Command and Control that enables an adversary to exfiltrate data using Google Drive and execute instructions on the target system using Google Sheet. During Red Teaming operations, this software was constructed in order to give a command and control that does not need any specific set up (such as a custom domain, VPS, CDN, etc.). This was done in order to make the application more accessible.
In addition, the application will only connect with Google domains (*.google.com) in order to make detection more challenging.
In October 2022, the Threat Analysis Group (TAG) of Google was successful in disrupting a campaign that was being run by HOODOO, a Chinese government-backed attacker also known as APT41. This effort was aimed at a Taiwanese media organization, and it consisted of sending phishing emails that included links to a password-protected file that was housed on Drive. The payload was a piece of open source software known as “G oogle Command and Control” (GC2), which was a red teaming tool. The program is written in Go, and it receives instructions from Google Sheets. These orders are used to exfiltrate data to Google Drive, which is presumably done to conceal the malicious behavior. After it has been installed on the victim’s system, the malware will query Google Sheets in order to collect orders from the attacker.
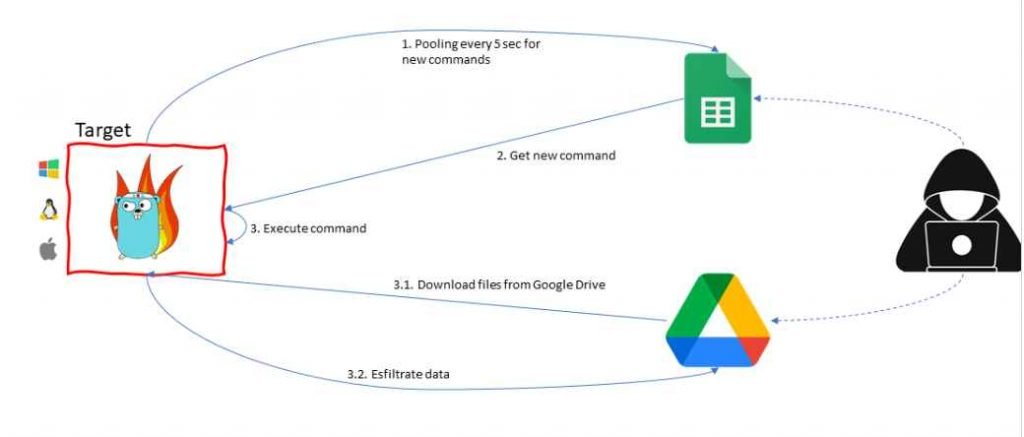
The attacker is able to download more files from Drive onto the target machine using GC2, in addition to exfiltrating data via Drive. HOODOO has previously made use of GC2 in the month of July 2022 in order to target an Italian job search website. These attacks provide light on a few critical patterns in the security landscape posed by threat actors linked with China. First, rather than building its own unique tools, Chinese advanced persistent threat (APT) organizations are increasingly turning to publicly accessible tooling like Cobalt Strike and other “pentest” software that can be purchased or found on sites like Github. This pattern may be seen, for instance, in HOODOO’s implementation of GC2. Second, the number of tools that are created in the Go programming language has been steadily increasing over the last several years. This is most likely attributable to the adaptability of the Go language as well as the ease with which module components may be added or removed. In conclusion, the targeting of Taiwanese media exemplifies the ongoing overlap of public sector threat actors attacking private sector entities with minimal links to the government.
The Google Cybersecurity Action Team (GCAT) and Mandiant conducted research on threat actors’ usage of Google Drive for hosting malware. The research revealed that threat actors store malware in Google Drive as encrypted ZIP files, most likely in an attempt to avoid detection. For instance, in the fourth quarter of 2022, Mandiant discovered a campaign that hosted the URSNIF binary on Google Drive in order to spread the URSNIF malware. URSNIF is a well-known piece of generic intrusion software that has a history of being used as a banking bot. Phishing emails were sent out by threat actors in an attempt to trick potential victims into downloading password-protected ZIP files that included harmful material. This content was subsequently installed on the victims’ computers.
The DICELOADER malware, which is another kind of broad intrusion malware that may be used for a variety of objectives, was employed by threat actors in the latter part of the fourth quarter of 2022 to implement an extension of this approach. During this campaign, Mandiant discovered phishing emails that had malicious links to Google Drive. Clicking on these links caused the recipient’s computer to download a ZIP file that included an LNK file. The Trojanized Zoom MSI installer was later downloaded and installed as a result of the LNK file, which ultimately resulted in the infection caused by the DICELOADER. Based on the phishing emails that were discovered by Mandiant, this campaign gave the impression that it was aimed at the financial services industry. The attackers further concealed their destructive purpose from the Google Drive download by removing the malware binary from the downloaded ZIP file and separating the two.
Google took a number of measures to put a stop to this behavior at the time, and the company also implemented new investigative skills to improve its ability to identify and thwart future instances of similar malicious usage of Google Drive.
These techniques bring to light the risk that is posed by threat actors using cloud services to host malicious content and their ongoing development of evasion techniques to avoid detection. For example, they have transitioned from using encrypted ZIP files that contained malware to encrypted ZIP files that linked to trojanized legitimate installers. Because this trend is expected to continue, businesses should exercise extreme caution while monitoring downloads, especially from websites that seem to be trustworthy.
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services




