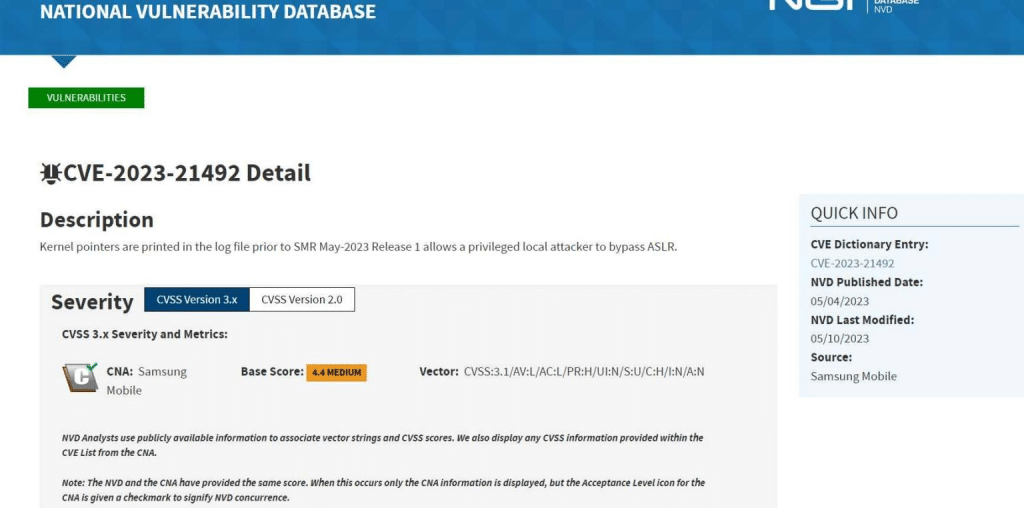
The vulnerability (CVE-2023-21492) affects mobile devices manufactured by Samsung and running on the following versions of the Android operating system. The vulnerability results from the accidental inclusion of sensitive data in log files.
Android 11, Android 12, Android 13
CISA has just recently issued a warning on a security hole that affects Samsung devices and makes it possible for attackers to avoid Android’s address space layout randomization (ASLR) protection while carrying out targeted attacks.
Randomization of the memory locations at which important app and operating system components are loaded into the device’s memory is made possible thanks to Android’s Address Space Layout Randomization (ASLR), which is a fundamental component of Android’s security architecture. The information that has been revealed may be used by local attackers who have elevated rights to perform an ASLR bypass, which would therefore make it easier to exploit weaknesses in memory management. Samsung has essentially remedied this issue as a part of the most recent security upgrades by adopting safeguards that prevent kernel references from being recorded in future instances. This was done as part of a larger effort to introduce new security measures.
According to the advice that was included in the May 2023 Security Maintenance Release (SMR), Samsung has admitted that it was notified of an attack that targets this specific flaw that is now active in the wild.
Despite the fact that Samsung did not provide any particular information on the exploit of CVE-2023-21492, it is essential to keep in mind that during highly focused cyberattacks, security vulnerabilities are regularly exploited as part of a sophisticated chain of exploits.
These attacks used chains of exploits that targeted the vulnerabilities to spread spyware that was driven by commercial interests.
While this is going on, security researchers working for Google’s Threat Analysis Group (TAG) and Amnesty International discovered and reported on two different attack operations in the month of March. Following the recent addition of the CVE-2023-21492 vulnerability to CISA’s list of Known Exploited Vulnerabilities, the United States Federal Civilian Executive Branch Agencies (FCEB) have been given a three-week window of time until June 9 to patch their Samsung Android devices in order to protect themselves from potential attacks that exploit this security flaw.
In accordance with BOD 22-01, government agencies have until the deadline of June 9, 2023 to fix any vulnerabilities that have been added to the CISA’s KEV list.
ANDROID SECURITY BOOK: 10 Simple Ways Billionaires Secure Their Android Devices




