DECIPHERING WEBWYRM: AN IN-DEPTH ANALYSIS OF THE PERVASIVE MALWARE THREATENING GLOBAL CYBERSECURITY
In the intricate landscape of global cybersecurity, Webwyrm malware has surfaced as a formidable adversary, casting its ominous shadow across 50 nations and leaving in its wake over 100,000 compromised victims. This insidious digital menace successfully emulates in excess of 1000 reputable companies globally, with the ensuing potential financial fallout estimated to surpass a staggering $100 million. It is imperative for cybersecurity professionals and organizations alike to comprehend the multifaceted nature of this threat to devise and implement robust defensive strategies effectively.
THE EVOLUTIONARY TRAJECTORY OF WEBWYRM
In the dynamic realm of cyber threats, malicious actors incessantly refine their Tactics, Techniques, and Procedures (TTPs), exploiting extant vulnerabilities and augmenting the efficacy of their malicious campaigns. Webwyrm epitomizes this relentless pursuit of evolution, embodying a level of sophistication reminiscent of infamous cyber threats of yore, such as the notorious ‘Blue Whale Challenge.’
REFINED MODUS OPERANDI
WebWyrm malware orchestrates a complex, deceptive narrative aimed at duping unsuspecting job seekers into relinquishing their cryptocurrency. Initiating contact predominantly via WhatsApp, the malefactors likely leverage data procured from employment portals to pinpoint and engage individuals predisposed to their deceptive overtures. Prospective victims are enticed with promises of lucrative weekly remuneration, ranging between $1200 and $1500, contingent upon the completion of daily task “packets” or “resets.”
Upon transferring funds into designated cryptocurrency wallets, victims are led to believe that the completion of tasks results in monetary withdrawals from their accounts, which are subsequently returned along with additional commissions. The introduction of “combo tasks” promises substantial financial returns but necessitates a more considerable investment. However, the caveat is that these returns are accessible only upon the sequential completion of all combo tasks, with each task demanding a progressively larger investment.
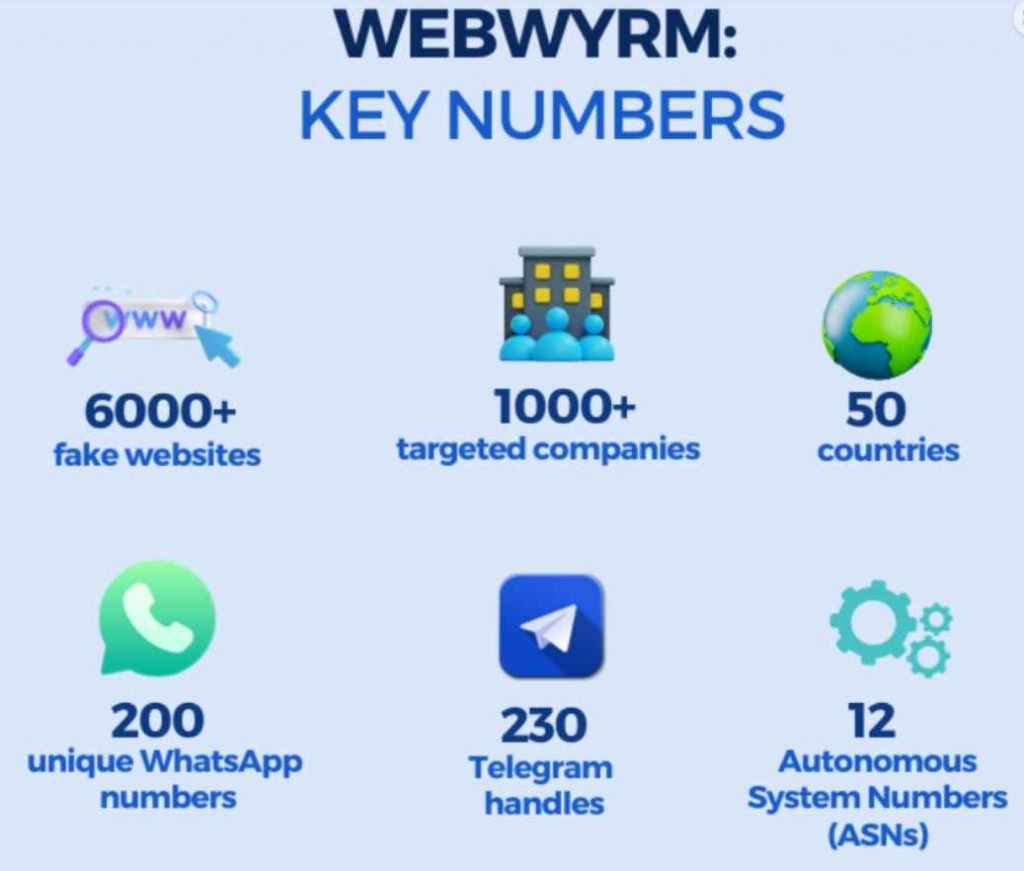
CAMPAIGN ENABLERS: TECHNICAL INSIGHTS
WebWyrm’s campaign is characterized by its sophistication, adaptability, and elusive operational framework. The initiative employs dedicated personnel engaging with victims via various platforms, thereby lending an aura of legitimacy and support to their endeavors. The orchestrators have meticulously crafted approximately 6000 counterfeit websites, directing victims to register their accounts. These platforms are expertly designed to mimic legitimate enterprises, with a keen focus on geo-targeting and associated contact numbers reflecting the respective victim’s geographical location.
Moreover, the malefactors astutely navigate the ephemeral nature of their infrastructure, allocating specific IP addresses or Autonomous System Numbers (ASNs) to host counterfeit domains for limited durations. This modus operandi facilitates operational continuity and anonymity, allowing for a swift transition to alternative infrastructure in response to potential threats, thereby effectively circumventing detection mechanisms.
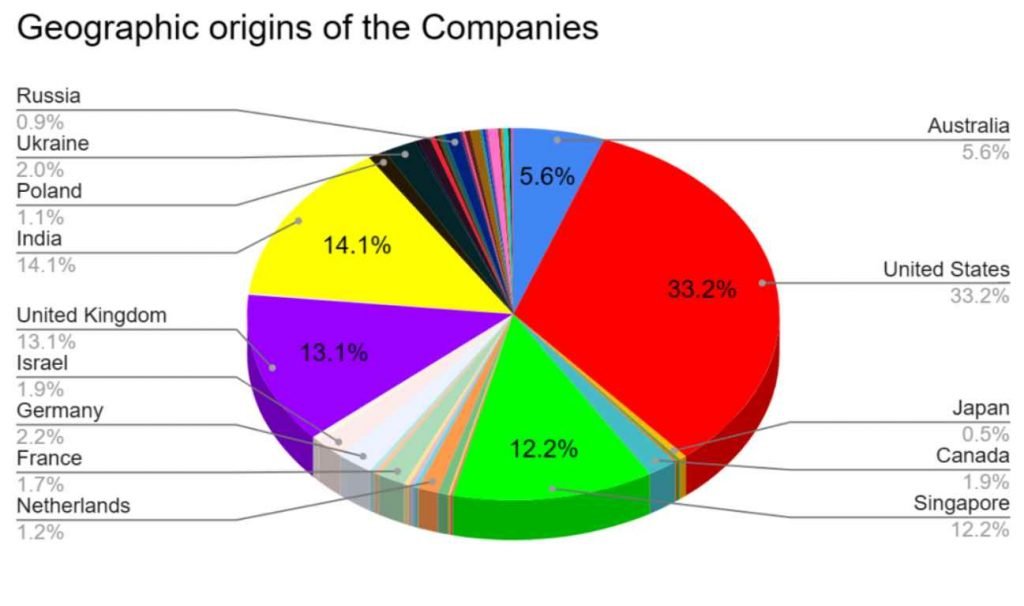
INDUSTRIES IN THE CROSSHAIRS
Webwyrm has indiscriminately targeted a plethora of industries, including:
- IT Services
- Software Development
- Mobile App Development
- User Experience Design
- Digital Marketing
- Web Development
- SEO
- E-Commerce
DEFENSIVE COUNTERMEASURES
Effective defense against Webwyrm necessitates the adoption of several countermeasures:
- Origin Tracing of Malefactors via Employment Portals
- Collaborative Defensive Initiatives
- Deployment of Rapid Response Teams
- Implementation of Domain Blacklisting Protocols
- Asset Seizure
- Launch of Educational Awareness Campaigns
With the incorporation of these enhanced technical insights, it becomes abundantly clear that WebWyrm represents a meticulously orchestrated, sophisticated operation with the singular aim of exploiting job seekers. The nuanced understanding of potential victims, coupled with a highly adaptive and elusive infrastructure, renders this a significant threat warranting coordinated, informed countermeasures to safeguard potential victims. Awareness, education, and the proactive deployment of defense mechanisms are pivotal in mitigating the risks associated with the WebWyrm malware campaign.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



