Your Risk Program Is Only as Strong as Its Feedback Loop
Many organizations are excellent at identifying risks, but far fewer are effective at closing them. Logging risks in a register without follow-up is not true risk management—it’s merely risk archiving.
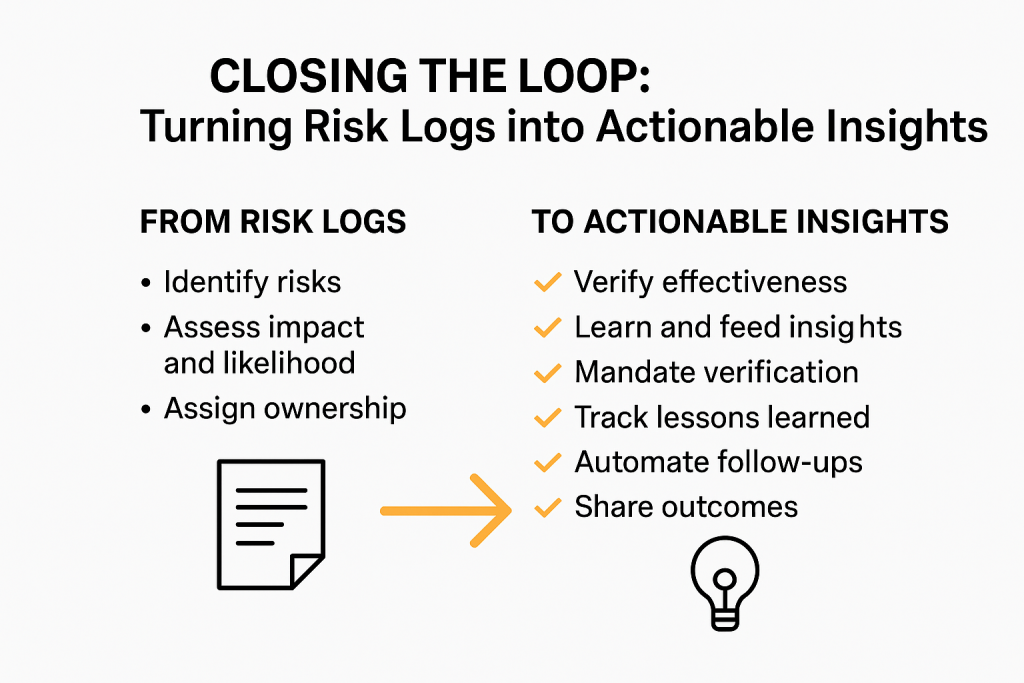
A robust risk program follows a complete cycle: identify risks, assess their impact and likelihood, assign ownership, implement mitigation, verify effectiveness, and feed lessons learned back into the system. Skipping verification and learning steps turns risk management into a task list, not a strategic control process.
Without a proper feedback loop, the same issues recur across departments, “closed” risks resurface during audits, teams lose confidence in the process, and leadership sees reports rather than meaningful results.
Building an Effective Feedback Loop:
- Make verification mandatory: every mitigation must be validated through control testing or monitoring.
- Track lessons learned: use post-mortems to refine controls and frameworks.
- Automate follow-ups: trigger reviews for risks not revisited within set intervals.
- Share outcomes: communicate mitigation results to teams to strengthen ownership and accountability.
Pro Tips:
- Measure risk elimination, not just identification.
- Highlight a “risk of the month” internally to maintain awareness.
- Link the risk register to performance metrics to align incentives with action.
The most effective GRC programs don’t just record risks—they learn from them. Every feedback loop strengthens organizational intelligence and security.
Many organizations excel at identifying risks but fail to close them, turning risk management into mere record-keeping. A strong program not only identifies, assesses, and mitigates risks but also verifies effectiveness and feeds lessons learned back into the system. Without this feedback loop, issues recur, audits fail, and teams lose trust. Mandating verification, tracking lessons, automating follow-ups, and sharing outcomes ensures risks are truly managed, not just logged—making your organization smarter, safer, and more accountable.
Risk Maturity Models: How to Assess Risk Management Effectiveness
- The Real AI Threat Isn’t the Model. It’s the Decision at Scale
- Agentic AI: The New Shadow IT Crisis Demanding Immediate Governance
- Expanding Risk, Shrinking Authority: The Modern CISO Dilemma
- Stop Debating Frameworks. Start Implementing Safeguards
- The 14 Vulnerability Domains That Make or Break Your Application Security
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security




