Cybersecurity researchers and IT admins have raised concerns over Google’s new ZIP and MOV Internet domains, warning that threat actors could use them for phishing attacks and malware delivery.
Earlier this month, Google introduced eight new top-level domains (TLD) that could be purchased for hosting websites or email addresses.
The new domains are .dad, .esq, .prof, .phd, .nexus, .foo, and for the topic of our article, the .zip and .mov domain TLDs.
While the ZIP and MOV TLDs have been available since 2014, it wasn’t until this month that they became generally available, allowing anyone to purchase a domain, like bleepingcomputer.zip, for a website.
However, these domains could be perceived as risky as the TLDs are also extensions of files commonly shared in forum posts, messages, and online discussions, which will now be automatically converted into URLs by some online platforms or applications.
The concern
Two common file types seen online are ZIP archives and MPEG 4 videos, whose file names end in .zip (ZIP archive) or .mov (video file).
Therefore, it’s very common for people to post instructions containing filenames with the .zip and .mov extensions.
However, now that they are TLDs, some messaging platforms and social media sites will automatically convert file names with .zip and .mov extensions into URLs.
For example, on Twitter, if you send someone instructions on opening a zip file and accessing a MOV file, the innocuous filenames are converted into an URL, as shown below.
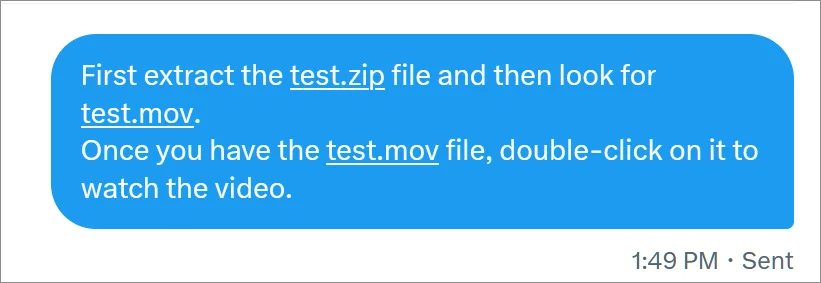
Source: BleepingComputer
When people see URLs in instructions, they commonly think that the URL can be used to download the associated file and may click on the link. For example, linking filenames to downloads is how we usually provide instructions on BleepingComputer in our articles, tutorials, and discussion forums.
However, if a threat actor owned a .zip domain with the same name as a linkified filename, a person may mistakenly visit the site and fall for a phishing scam or download malware, thinking the URL is safe because it came from a trusted source.
While it’s very unlikely that threat actors will register thousands of domains to capture a few victims, you only need one corporate employee to mistakenly install malware for an entire network to be affected.
Abuse of these domains is not theoretical, with cyber intel firm Silent Push Labs already discovering what appears to be a phishing page at microsoft-office[.]zip attempting to steal Microsoft Account credentials.
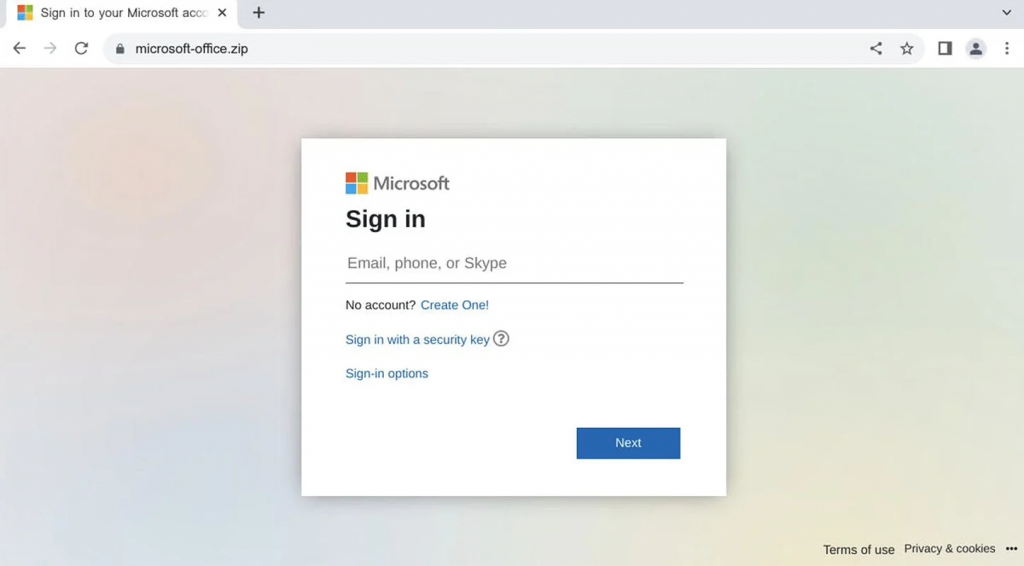
Source: Silent Push Labs
Cybersecurity researchers have also started to play with the domains, with Bobby Rauch publishing research on developing convincing phishing links using Unicode characters and the userinfo delimiter (@) in URLs.
Rauch’s research shows how threat actors can make phishing URLs that look like legitimate file download URLs at GitHub but actually take you to a website at v1.27.1[.]zip when clicked, as illustrated below.
https://github.com/kubernetes/kubernetes/archive/refs/tags/@v1.27.1.zip
Conflicting opinions
These developments have sparked a debate among developers, security researchers, and IT admins, with some feeling the fears are not warranted and others feeling that the ZIP and MOV TLDs add unnecessary risk to an already risky online environment.
People have begun registering .zip domains that are associated with common ZIP archives, such as update.zip, financialstatement.zip, setup.zip, attachment.zip, officeupdate.zip, and backup.zip, to display information about the risks of ZIP domains, to RickRoll you, or to share harmless information.
Open source developer Matt Holt also requested that the ZIP TLD be removed from Mozilla’s Public Suffix List, a list of all public top-level domains to be incorporated in applications and browsers.
However, the PSL community quickly explained that while there may be a slight risk associated with these TLDs, they are still valid and should not be removed from the PSL as it would affect the operation of legitimate sites.
“Removing existing TLDs from the PSL for this reason would just be wrong. This list is used for many different reasons, and just because these entries are bad for one very specific use-case, they are still needed for (almost) all others,” explained software engineer Felix Fontein.
“These are legit TLDs in the ICP3 root. This will not proceed,” further shared PSL maintainer Jothan Frakes.
“Really, the expressed concerns are more of a glaring example of a disconnect between the developer and security community and domain name governance, where they would benefit from more engagement within ICANN.”
At the same time, other security researchers and developers have expressed that they believe the fears regarding these new domains are overblown.
When BleepingComputer contacted Google about these concerns, they said that the risk of confusion between file and domain names is not new, and browser mitigations are in place to protect users from abuse.
“The risk of confusion between domain names and file names is not a new one. For example, 3M’s Command products use the domain name command.com, which is also an important program on MS DOS and early versions of Windows. Applications have mitigations for this (such as Google Safe Browsing), and these mitigations will hold true for TLD’s such as .zip.
At the same time, new namespaces provide expanded opportunities for naming such as community.zip and url.zip. Google takes phishing and malware seriously and Google Registry has existing mechanisms to suspend or remove malicious domains across all of our TLDs, including .zip. We will continue to monitor the usage of .zip and other TLDs and if new threats emerge we will take appropriate action to protect users.” – Google.
What should you do?
The reality is that you do not need to do anything extra than you are already doing to protect yourself from phishing sites.
As everyone should already know, it is never safe to click on links from people or download files from sites you do not trust.
Like any link, if you see a .zip or .mov link in a message, research it before clicking on it. If you are still unsure if the link is safe, do not click on it.
By following these simple steps, the impact of the new TLDs will be minimal and not significantly increase your risk.
However, the exposure to these links will likely increase as more applications automatically turn ZIP and MOV filenames into links, giving you one more thing to be careful about when online.
InfoSec tools | InfoSec services | InfoSec books