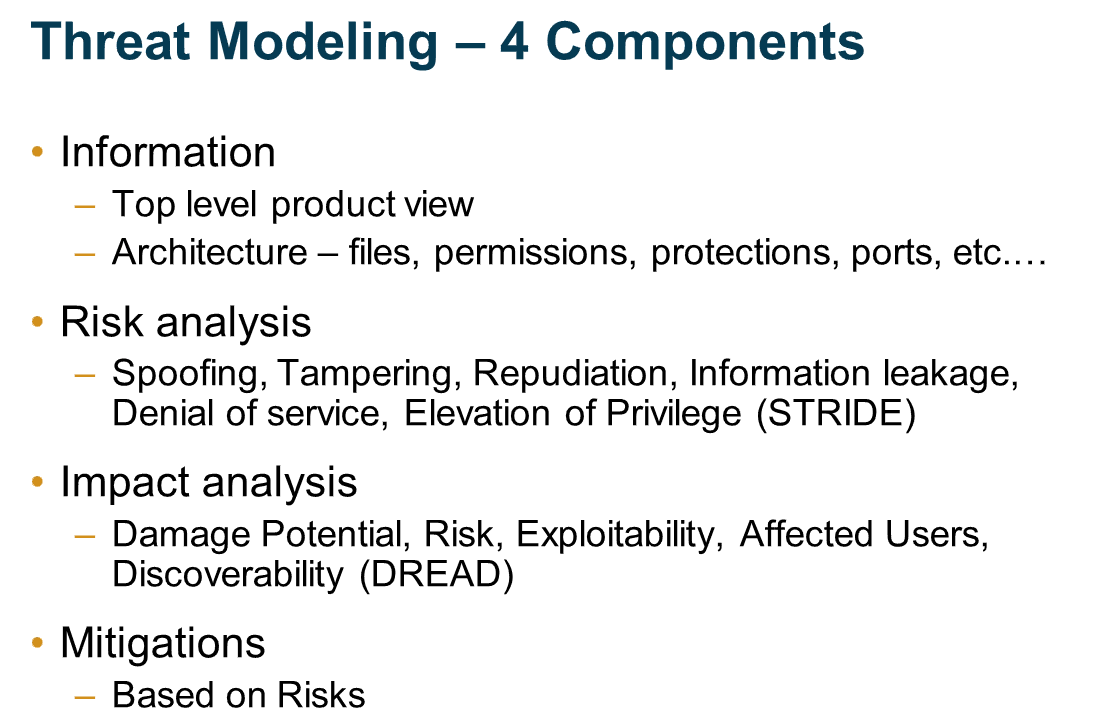
Threat Modeling for Data Protection
When evaluating the security of an application and data model ask the questions:
- What is the sensitivity of the data?
- What are the regulatory, compliance, or privacy requirements for the data?
- What is the attack vector that a data owner is hoping to mitigate?
- What is the overall security posture of the environment, is it a hostile environment or a relatively trusted one?
Data When threat modeling, consider the following common scenarios:
Source: Threat Modeling for Data Protection
Threat Modeling in 2019
httpv://www.youtube.com/watch?v=ZoxHIpzaZ6U
Subscribe to DISC InfoSec blog by Email