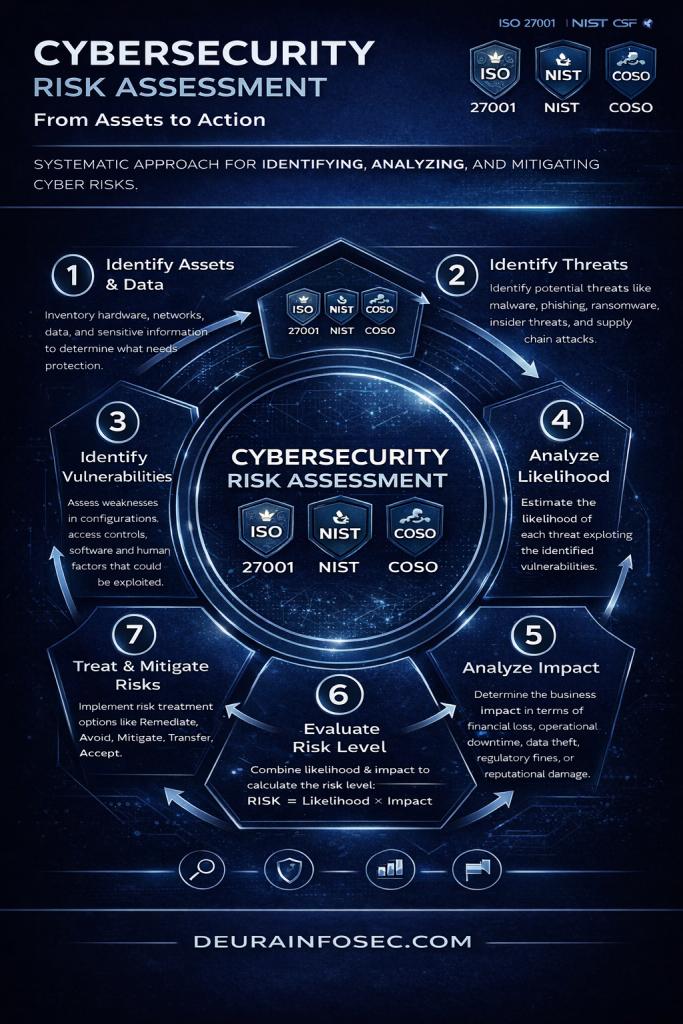
Below is a clear, structured explanation Cybersecurity Risk Assessment Process
What Is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is a structured process for understanding how cyber threats could impact the business, not just IT systems. Its purpose is to identify what assets matter most, what could go wrong, how likely those events are, and what the consequences would be if they occur. Rather than focusing on tools or controls first, a risk assessment provides decision-grade insight that leadership can use to prioritize investments, allocate resources, and accept or reduce risk knowingly. When aligned with frameworks like ISO 27001, NIST CSF, and COSO, it creates a common language between security, executives, and the board.
1. Identify Assets & Data
The first step is to identify and inventory critical assets, including hardware, software, cloud services, networks, data, and sensitive information. This step answers the fundamental question: what are we actually protecting? Without a clear understanding of assets and their business value, security efforts become unfocused. Many breaches stem from misconfigured or forgotten assets, making visibility and ownership essential to effective risk management.
2. Identify Threats
Once assets are known, the next step is identifying the threats that could realistically target them. These include external threats such as malware, ransomware, phishing, and supply chain attacks, as well as internal threats like insider misuse or human error. Threat identification focuses on who might attack, how, and why, based on real-world attack patterns rather than hypothetical scenarios.
3. Identify Vulnerabilities
Vulnerabilities are weaknesses that threats can exploit. These may exist in system configurations, software, access controls, processes, or human behavior. This step examines where defenses are insufficient or outdated, such as unpatched systems, excessive privileges, weak authentication, or lack of security awareness. Vulnerabilities are the bridge between threats and actual incidents.
4. Analyze Likelihood
Likelihood analysis evaluates how probable it is that a given threat will successfully exploit a vulnerability. This assessment considers threat actor capability, exposure, historical incidents, and the effectiveness of existing controls. The goal is not precision but reasonable estimation, enabling organizations to distinguish between theoretical risks and those that are most likely to occur.
5. Analyze Impact
Impact analysis focuses on the potential business consequences if a risk materializes. This includes financial loss, operational disruption, data theft, regulatory penalties, legal exposure, and reputational damage. By framing impact in business terms rather than technical language, this step ensures that cyber risk is understood as an enterprise risk, not just an IT issue.
6. Evaluate Risk Level
Risk level is determined by combining likelihood and impact, commonly expressed as Risk = Likelihood × Impact. This step allows organizations to rank risks and identify which ones exceed acceptable thresholds. Not all risks require immediate remediation, but all should be understood, documented, and owned at the appropriate level.
7. Treat & Mitigate Risks
Risk treatment involves deciding how to handle each identified risk. Options include remediating the risk through controls, mitigating it by reducing likelihood or impact, transferring it through insurance or contracts, avoiding it by changing business practices, or accepting it when the risk is within tolerance. This step turns analysis into action and aligns security decisions with business priorities.
8. Monitor & Review
Cyber risk is not static. New threats, technologies, and business changes continuously reshape the risk landscape. Monitoring and review ensure that controls remain effective and that risk assessments stay current. This step embeds risk management into ongoing governance rather than treating it as a one-time exercise.
Bottom line:
A cybersecurity risk assessment is not about achieving perfect security—it’s about making informed, defensible decisions in an environment where risk is unavoidable. When done well, it transforms cybersecurity from a technical function into a strategic business capability.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- AI Agents and the New Cybersecurity Frontier: Understanding the 7 Major Attack Surfaces
- Understanding AI/LLM Application Attack Vectors and How to Defend Against Them
- AI Governance Assessment for ISO 42001 Readiness
- Beyond ChatGPT: The 9 Layers of AI Transforming Business from Analytics to Autonomous Agents
- CMMC Level 2 Third-Party Assessment: What It Is, Why It Matters, and What to Expect





