
Defining risk appetite, risk tolerance, and risk capacity is foundational to effective risk management because they set the boundaries for decision-making, ensure consistency, and prevent both reckless risk-taking and over-conservatism. Each plays a distinct role:
1. Risk Appetite – Strategic Intent
What it is:
The amount and type of risk an organization is willing to pursue to achieve its objectives.
Why it’s necessary:
- Aligns risk-taking with business strategy
- Guides leadership on where to invest, innovate, or avoid
- Prevents ad-hoc or emotion-driven decisions
- Provides a top-down signal to management and staff
Example:
“We are willing to accept moderate cybersecurity risk to accelerate digital innovation, but zero tolerance for regulatory non-compliance.”
Without a defined appetite, risk decisions become inconsistent and reactive.
2. Risk Tolerance – Operational Guardrails
What it is:
The acceptable variation around the risk appetite—usually expressed as measurable limits.
Why it’s necessary:
- Translates strategy into actionable thresholds
- Enables monitoring and escalation
- Supports objective decision-making
- Prevents “death by risk avoidance” or uncontrolled exposure
Example:
- Maximum acceptable downtime: 4 hours
- Acceptable phishing click rate: <3%
- Financial loss per incident: <$250K
Risk appetite without tolerance is too abstract to manage day-to-day risk.
3. Risk Capacity – Hard Limits
What it is:
The maximum risk the organization can absorb without threatening survival (financial, legal, operational, reputational).
Why it’s necessary:
- Establishes non-negotiable boundaries
- Prevents existential or catastrophic risk
- Informs stress testing and scenario analysis
- Ensures risk appetite is realistic, not aspirational
Example:
- Cash reserves can absorb only one major ransomware event
- Loss of a specific license would shut down operations
Risk capacity is about what you can survive, not what you prefer.
How They Work Together
| Concept | Question It Answers | Focus |
|---|---|---|
| Risk Appetite | What risk do we want to take? | Strategy |
| Risk Tolerance | How much deviation is acceptable? | Operations |
| Risk Capacity | How much risk can we survive? | Survival |
Golden Rule:
Risk appetite must always stay within risk capacity, and risk tolerance enforces appetite in practice.
Why This Matters (Especially for Governance & Compliance)
- Required by ISO 27001, ISO 31000, COSO ERM, NIST, ISO 42001
- Enables defensible decisions for auditors and regulators
- Strengthens board oversight and executive accountability
- Critical for cyber risk, AI risk, third-party risk, and resilience planning
In One Line
Defining risk appetite, tolerance, and capacity ensures an organization takes the right risks, in the right amount, without risking its existence.
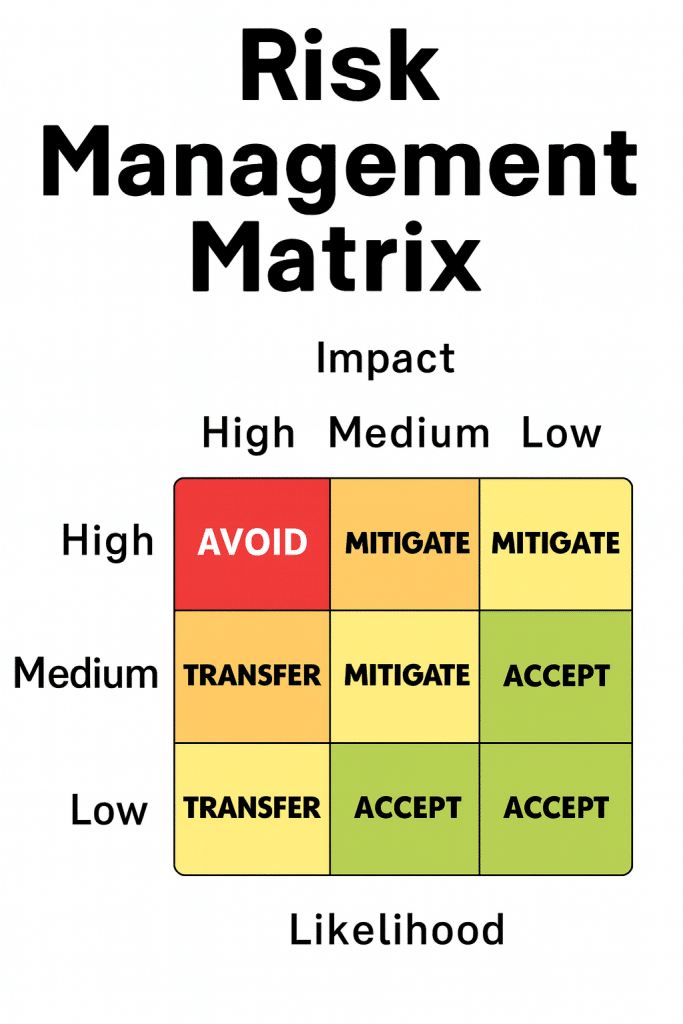
Risk appetite, risk tolerance, and risk capacity describe different but closely related dimensions of how an organization deals with risk. Risk appetite defines the level of risk an organization is willing to accept in pursuit of its objectives. It reflects intent and ambition: too little risk appetite can result in missed opportunities, while staying within appetite is generally acceptable. Exceeding appetite signals that mitigation is required because the organization is operating beyond what it has consciously agreed to accept.
Risk tolerance translates appetite into measurable thresholds that trigger action. It sets the boundaries for monitoring and review. When outcomes fall below tolerance, they are usually still acceptable, but when outcomes sit within tolerance limits, mitigation may already be required. Once tolerance is exceeded, the situation demands immediate escalation, as predefined limits have been breached and governance intervention is needed.
Risk capacity represents the absolute limit of risk an organization can absorb without threatening its viability. It is non-negotiable. Operating below capacity still requires mitigation, operating within capacity often demands immediate escalation, and exceeding capacity is simply not acceptable. At that point, the organization’s survival, legal standing, or core mission may be at risk.
Together, these three concepts form a hierarchy: appetite expresses willingness, tolerance defines control points, and capacity marks the hard stop.
Opinion on the statement
The statement “When appetite, tolerance, and capacity are clearly defined (and consistently understood), risk stops being theoretical and becomes a practical decision guide” is accurate and highly practical, especially in governance and security contexts.
Without clear definitions, risk discussions stay abstract—people debate “high” or “low” risk without shared meaning. When these concepts are defined, risk becomes operational. Decisions can be made quickly and consistently because everyone knows what is acceptable, what requires action, and what is unacceptable.
Example (Information Security / vCISO context):
An organization may have a risk appetite that accepts moderate operational risk to enable faster digital transformation. Its risk tolerance might specify that any vulnerability with a CVSS score above 7.5 must be remediated within 14 days. Its risk capacity could be defined as “no risk that could result in regulatory fines exceeding $2M or prolonged service outage.”
With this clarity, a newly discovered critical vulnerability is no longer a debate—it either sits within tolerance (monitor), exceeds tolerance (mitigate and escalate), or threatens capacity (stop deployment immediately).
Example (AI governance):
A company may accept some experimentation risk (appetite) with internal AI tools, tolerate limited model inaccuracies under defined error rates (tolerance), but have zero capacity for risks that could cause regulatory non-compliance or IP leakage. This makes go/no-go decisions on AI use cases clear and defensible.
In practice, clearly defining appetite, tolerance, and capacity turns risk management from a compliance exercise into a decision-making framework. It aligns leadership intent with operational action—and that is where risk management delivers real value.

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- The Real AI Threat Isn’t the Model. It’s the Decision at Scale
- Agentic AI: The New Shadow IT Crisis Demanding Immediate Governance
- Expanding Risk, Shrinking Authority: The Modern CISO Dilemma
- Stop Debating Frameworks. Start Implementing Safeguards
- The 14 Vulnerability Domains That Make or Break Your Application Security





