In a startling revelation, Bitdefender, a leading cybersecurity firm, has disclosed a series of sophisticated attack methods that could significantly impact users of Google Workspace and Google Credential Provider for Windows (GCPW). This discovery highlights potential weaknesses in widely used cloud and authentication services, prompting a reevaluation of current security measures.
DISCOVERY OF ADVANCED ATTACK TECHNIQUES
Bitdefender’s research team, working in conjunction with their in-house research institute Bitdefender Labs, has identified previously unknown methods that cybercriminals could use to escalate a breach from a single endpoint to a network-wide level. These techniques, if exploited, could lead to severe consequences such as ransomware attacks or massive data exfiltration.
The attack progression involves several key stages, starting from a single compromised machine. Once inside the system, attackers could potentially:
- Move across cloned machines within the network, especially if they are equipped with GCPW.
- Gain unauthorized access to the Google Cloud Platform through custom permissions.
- Decrypt locally stored passwords, extending their reach beyond the initially compromised machine.
These findings were responsibly disclosed to Google. However, Google has stated that these issues will not be addressed directly, as they fall outside their designated threat model. This decision reflects Google’s risk assessment and security priorities.
THE DUAL ROLE OF GOOGLE CREDENTIAL PROVIDER FOR WINDOWS (GCPW)
At the heart of these vulnerabilities is the Google Credential Provider for Windows (GCPW), a tool designed to streamline access and management within Google’s ecosystem. GCPW serves two primary functions:
- Remote Device Management: Similar to Mobile Device Management (MDM) systems like Microsoft Intune, GCPW allows administrators to remotely manage and control Windows devices connected to Google Workspace. This includes enforcing security policies, deploying software updates, and managing device settings without needing a VPN connection or domain registration.
- Single-Sign On (SSO) Authentication: GCPW facilitates SSO for Windows devices using Google Workspace credentials. This integration provides a seamless login experience, enabling users to access their devices with the same credentials used for Google services like Gmail, Google Drive, and Google Calendar.
THE OPERATIONAL MECHANISM OF GCPW
Understanding GCPW’s functioning is crucial in comprehending the vulnerabilities. Here’s a breakdown of its operational process:
- Local Service Account Creation: Upon installing GCPW, a new user account named ‘gaia’ is created. This account, not intended for regular user interactions, serves as a service account with elevated privileges.
- Credential Provider Integration: GCPW integrates a new Credential Provider into the Windows Local Security Authority Subsystem Service (lsass), a critical component responsible for handling security operations and user authentication in Windows.
- Local User Account Creation: GCPW facilitates the creation of new local user accounts linked to Google Workspace accounts whenever a new user authenticates with the system.
- Logon Procedure: These Google Workspace users are logged in using their newly created local profiles, where a refresh token is stored to ensure continuous access without repeated authentication prompts.
UNCOVERED ATTACK METHODS
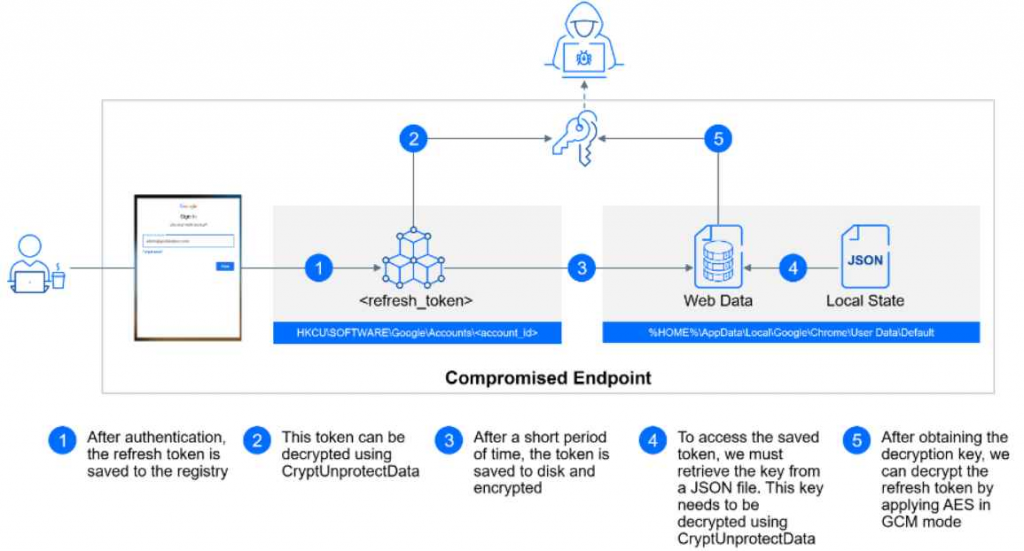
GOLDEN IMAGE LATERAL MOVEMENT:
- Virtualized Environment Challenge: In environments that use cloned virtual machines (VMs), such as Virtual Desktop Infrastructure (VDI) or Desktop as a Service (DaaS) solutions, the installation of GCPW on a base machine means that the ‘gaia’ account and its password are cloned across all VMs.
- Attack Implication: If an attacker discovers the password of one ‘gaia’ account, they can potentially access all machines that have been cloned from the same base image.
- Scenario: Imagine a company, “Acme Corp,” uses a Virtual Desktop Infrastructure (VDI) where multiple virtual machines (VMs) are cloned from a single ‘golden image’ for efficiency. This image has Google Credential Provider for Windows (GCPW) pre-installed for ease of access.
- Attack Example:
- An attacker, Alice, manages to compromise one of Acme Corp’s VMs. During her exploration, she discovers that the VM has GCPW installed.
- She learns that the ‘gaia’ account password created during the GCPW setup is identical across all cloned VMs because they were derived from the same golden image.
- By extracting the ‘gaia’ account password from the compromised VM, Alice can now access all other VMs cloned from the same image. This allows her to move laterally across the network, potentially accessing sensitive information or deploying malware.
UNAUTHORIZED ACCESS TOKEN REQUEST:
- Exploitation of OAuth Tokens: GCPW stores an OAuth 2.0 refresh token within the user’s session, maintaining access to the broader Google ecosystem. Attackers gaining access to this token can request new Access Tokens with varied permissions.
- Scope of Abuse: The permissions granted by these tokens can enable attackers to access or manipulate a wide range of user data and Google services, effectively bypassing multi-factor authentication (MFA) processes.
- Scenario: At a different company, “Beta Ltd.,” employees use their Google Workspace credentials to log into their Windows machines, facilitated by GCPW.
Attack Example:
- Bob, a cybercriminal, gains initial access to a Beta Ltd. employee’s computer through a phishing attack.
- Once inside the system, Bob finds the OAuth 2.0 refresh token stored by GCPW. This token is meant to maintain seamless access to Google services without repeated logins.
- With this token, Bob crafts a request to Google’s authentication servers pretending to be the legitimate user. He requests new Access Tokens with broad permissions, like access to emails or cloud storage.
- Using these tokens, Bob can now access sensitive data in the employee’s Google Workspace environment, like emails or documents, bypassing any multi-factor authentication set up by the company.
PASSWORD RECOVERY THREAT:
- Plaintext Credential Risk: GCPW’s mechanism of saving user passwords as encrypted LSA secrets, intended for password resetting, presents a vulnerability. Skilled attackers could decrypt these credentials, allowing them to impersonate users and gain unrestricted account access.
Scenario: A small business, “Gamma Inc.,” uses GCPW for managing their Windows devices and Google Workspace accounts.
Attack Example:
- Carla, an experienced hacker, targets Gamma Inc. She successfully breaches one of the employee’s systems through a malware-laden email attachment.
- After gaining access, Carla locates the encrypted LSA secret stored by GCPW, which contains the user’s Google Workspace password.
- Using advanced decryption techniques, she decrypts this password. Now, Carla has the same access privileges as the employee, not just on the local machine but across all Google services where the employee’s account is used.
- This enables Carla to impersonate the employee, access company emails, manipulate documents, or even transfer funds if the employee has financial privileges.
GOOGLE’S STANCE AND SECURITY IMPLICATIONS
Google’s decision not to address these findings, citing their exclusion from the company’s specific threat model, has stirred a debate in the cybersecurity community. While Google’s risk.
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory



