garak — LLM Vulnerability Scanner / Red-Teaming Kit
garak(Generative AI Red-teaming & Assessment Kit) is an open-source tool aimed specifically at testing Large Language Models and dialog systems for AI-specific vulnerabilities: prompt injection, jailbreaks, data leakage, hallucinations, toxicity, etc.- It supports many LLM sources: Hugging Face models, OpenAI APIs, AWS Bedrock, local ggml models, etc.
- Typical usage is via command line, making it relatively easy to incorporate into a Linux/pen-test workflow.
- For someone interested in “governance,”
garakhelps identify when an AI system violates safety, privacy or compliance expectations before deployment.
BlackIce — Containerized Toolkit for AI Red-Teaming & Security Testing
- BlackIce is described as a standardized, containerized red-teaming toolkit for both LLMs and classical ML models. The idea is to lower the barrier to entry for AI security testing by packaging many tools into a reproducible Docker image.
- It bundles a curated set of open-source tools (as of late 2025) for “Responsible AI and Security testing,” accessible via a unified CLI interface — akin to how Kali bundles network-security tools.
- For governance purposes: BlackIce simplifies running comprehensive AI audits, red-teaming, and vulnerability assessments in a consistent, repeatable environment — useful for teams wanting to standardize AI governance practices.
LibVulnWatch — Supply-Chain & Library Risk Assessment for AI Projects
- While not specific to LLM runtime security, LibVulnWatch focuses on evaluating open-source AI libraries (ML frameworks, inference engines, agent-orchestration tools) for security, licensing, supply-chain, maintenance and compliance risks.
- It produces governance-aligned scores across multiple domains, helping organizations choose safer dependencies and keep track of underlying library health over time.
- For an enterprise building or deploying AI: this kind of tool helps verify that your AI stack — not just the model — meets governance, audit, and risk standards.
Giskard (open-source / enterprise) — LLM Red-Teaming & Monitoring for Safety/Compliance
- Giskard offers LLM vulnerability scanning and red-teaming capabilities (prompt injection, data leakage, unsafe behavior, bias, etc.) via both an open-source library and an enterprise “Hub” for production-grade systems.
- It supports “black-box” testing: you don’t need internal access to the model — as long as you have an API or interface, you can run tests.
- For AI governance, Giskard helps in evaluating compliance with safety, privacy, and fairness standards before and after deployment.
🔧 What This Means for Kali Linux / Pen-Test-Oriented Workflows
- The emergence of tools like
garak,BlackIce, andGiskardshows that AI governance and security testing are becoming just as “testable” as traditional network or system security. For people familiar with Kali’s penetration-testing ecosystem — this is a familiar, powerful shift. - Because they are Linux/CLI-friendly and containerizable (especially BlackIce), they can integrate neatly into security-audit pipelines, continuous-integration workflows, or red-team labs — making them practical beyond research or toy use.
- Using a supply-chain-risk tool like LibVulnWatch alongside model-level scanners gives a more holistic governance posture: not just “Is this LLM safe?” but “Is the whole AI stack (dependencies, libraries, models) reliable and auditable?”
⚠️ A Few Important Caveats (What They Don’t Guarantee)
- Tools like
garakandGiskardattempt to find common issues (jailbreaks, prompt injection, data leakage, harmful outputs), but cannot guarantee absolute safety or compliance — because many risks (e.g. bias, regulatory compliance, ethics, “unknown unknowns”) depend heavily on context (data, environment, usage). - Governance is more than security: It includes legal compliance, privacy, fairness, ethics, documentation, human oversight — many of which go beyond automated testing.
- AI-governance frameworks are still evolving; even red-teaming tools may lag behind novel threat types (e.g. multi-modality, chain-of-tool-calls, dynamic agentic behaviors).
🎯 My Take / Recommendation (If You Want to Build an AI-Governance Stack Now)
If I were you and building or auditing an AI system today, I’d combine these tools:
- Start with garak or Giskard to scan model behavior for injection, toxicity, privacy leaks, etc.
- Use BlackIce (in a container) for more comprehensive red-teaming including chaining tests, multi-tool or multi-agent flows, and reproducible audits.
- Run LibVulnWatch on your library dependencies to catch supply-chain or licensing risks.
- Complement that with manual reviews, documentation, human-in-the-loop audits and compliance checks (since automated tools only catch a subset of governance concerns).
🧠 AI Governance & Security Lab Stack (2024–2025)
1️⃣ LLM Vulnerability Scanning & Red-Teaming (Core Layer)
These are your “nmap + metasploit” equivalents for LLMs.
garak (NVIDIA)
- Automated LLM red-teaming
- Tests for jailbreaks, prompt injection, hallucinations, PII leaks, unsafe outputs
- CLI-driven → perfect for Kali workflows
✅ Baseline requirement for AI audits
Giskard (Open Source / Enterprise)
- Structured LLM vulnerability testing (multi-turn, RAG, tools)
- Bias, reliability, hallucination, safety checks
✅ Strong governance reporting angle
promptfoo
- Prompt, RAG, and agent testing framework
- CI/CD friendly, regression testing
✅ Best for continuous governance
AutoRed
- Automatically generates adversarial prompts (no seeds)
- Excellent for discovering unknown failure modes
✅ Advanced red-team capability
RainbowPlus
- Evolutionary adversarial testing (quality + diversity)
- Better coverage than brute-force prompt testing
✅ Research-grade robustness testing
2️⃣ Benchmarks & Evaluation Frameworks (Evidence Layer)
These support objective governance claims.
HarmBench
- Standardized harm/safety benchmark
- Measures refusal correctness, bypass resistance
✅ Great for board-level reporting
OpenAI / Anthropic Safety Evals (Open Specs)
- Industry-accepted evaluation criteria
✅ Aligns with regulator expectations
HELM / BIG-Bench (Selective usage)
- Model behavior benchmarking
⚠️ Use carefully — not all metrics are governance-relevant
3️⃣ Prompt Injection & Agent Security (Runtime Protection)
This is where most AI systems fail in production.
LlamaFirewall
- Runtime enforcement for tool-using agents
- Prevents prompt injection, tool abuse, unsafe actions
✅ Critical for agentic AI
NeMo Guardrails
- Rule-based and model-assisted controls
✅ Good for compliance-driven orgs
Rebuff
- Prompt-injection detection & prevention
✅ Lightweight, practical defense
4️⃣ Infrastructure & Deployment Security (Kali-Adjacent)
This is often ignored — and auditors will catch it.
AI-Infra-Guard (Tencent)
- Scans AI frameworks, MCP servers, model infra
- Includes jailbreak testing + infra CVEs
✅ Closest thing to “Nessus for AI”
Trivy
- Container + dependency scanning
✅ Use on AI pipelines and inference containers
Checkov
- IaC scanning (Terraform, Kubernetes, cloud AI services)
✅ Cloud AI governance
5️⃣ Supply Chain & Model Provenance (Governance Backbone)
Auditors care deeply about this.
LibVulnWatch
- AI/ML library risk scoring
- Licensing, maintenance, vulnerability posture
✅ Perfect for vendor risk management
OpenSSF Scorecard
- OSS project security maturity
✅ Mirror SBOM practices
Model Cards / Dataset Cards (Meta, Google standards)
- Manual but essential
✅ Regulatory expectation
6️⃣ Data Governance & Privacy Risk
AI governance collapses without data controls.
Presidio
- PII detection/anonymization
✅ GDPR, HIPAA alignment
Microsoft Responsible AI Toolbox
- Error analysis, fairness, interpretability
✅ Human-impact governance
WhyLogs
- Data drift & data quality monitoring
✅ Operational governance
7️⃣ Observability, Logging & Auditability
If it’s not logged, it doesn’t exist to auditors.
OpenTelemetry (LLM instrumentation)
- Trace model prompts, outputs, tool calls
✅ Explainability + forensics
LangSmith / Helicone
- LLM interaction logging
✅ Useful for post-incident reviews
8️⃣ Policy, Controls & Governance Mapping (Human Layer)
Tools don’t replace governance — they support it.
ISO/IEC 42001 Control Mapping
- AI management system
✅ Enterprise governance standard
NIST AI RMF
- Risk identification & mitigation
✅ US regulator alignment
DASF / AICM (AI control models)
- Control-oriented governance
✅ vCISO-friendly frameworks
🔗 How This Fits into Kali Linux
Kali doesn’t yet ship AI governance tools by default — but:
- ✅ Almost all of these run on Linux
- ✅ Many are CLI-based or Dockerized
- ✅ They integrate cleanly with red-team labs
- ✅ You can easily build a custom Kali “AI Governance profile”
My recommendation:
Create:
- A Docker compose stack for garak + Giskard + promptfoo
- A CI pipeline for prompt & agent testing
- A governance evidence pack (logs + scores + reports)
Map each tool to ISO 42001 / NIST AI RMF controls
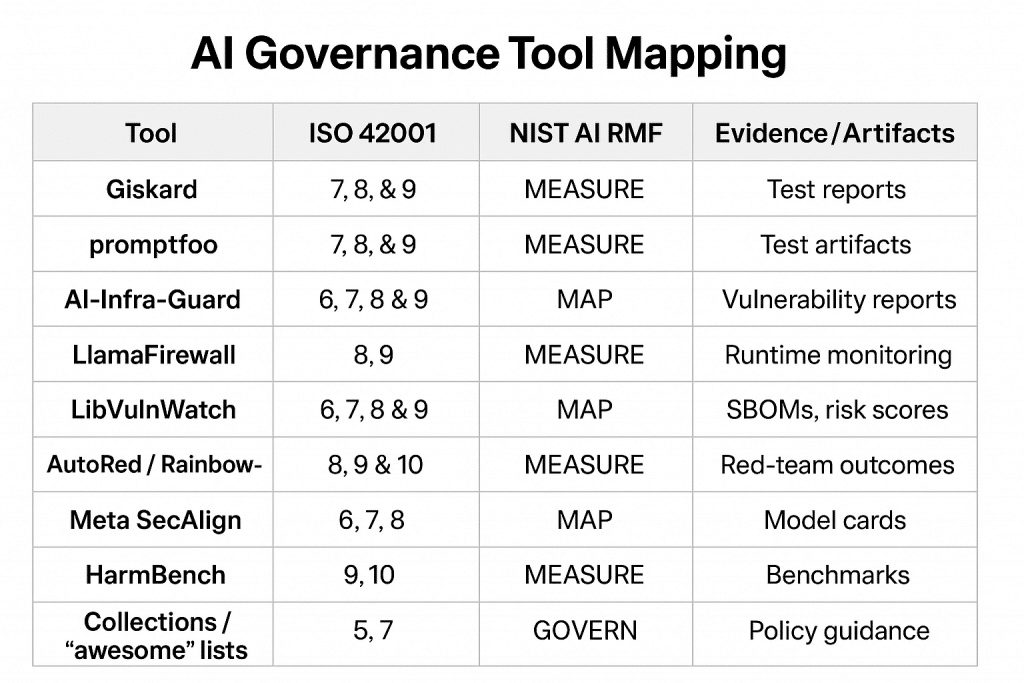
below is a compact, actionable mapping that connects the ~10 tools we discussed to ISO/IEC 42001 clauses (high-level AI management system requirements) and to the NIST AI RMF Core functions (GOVERN / MAP / MEASURE / MANAGE).
I cite primary sources for the standards and each tool so you can follow up quickly.
Notes on how to read the table
• ISO 42001 — I map to the standard’s high-level clauses (Context (4), Leadership (5), Planning (6), Support (7), Operation (8), Performance evaluation (9), Improvement (10)). These are the right level for mapping tools into an AI Management System. Cloud Security Alliance+1
• NIST AI RMF — I use the Core functions: GOVERN / MAP / MEASURE / MANAGE (the AI RMF core and its intended outcomes). Tools often map to multiple functions. NIST Publications
• Each row: tool → primary ISO clauses it supports → primary NIST functions it helps with → short justification + source links.
Tool → ISO 42001 / NIST AI RMF mapping
1) Giskard (open-source + platform)
- ISO 42001: 7 Support (competence, awareness, documented info), 8 Operation (controls, validation & testing), 9 Performance evaluation (testing/metrics). Cloud Security Alliance+1
- NIST AI RMF: MEASURE (testing, metrics, evaluation), MAP (identify system behavior & risks), MANAGE (remediation actions). NIST Publications+1
- Why: Giskard automates model testing (bias, hallucination, security checks) and produces evidence/metrics used in audits and continuous evaluation. GitHub
2) promptfoo (prompt & RAG test suite / CI integration)
- ISO 42001: 7 Support (documented procedures, competence), 8 Operation (validation before deployment), 9 Performance evaluation (continuous testing). Cloud Security Alliance
- NIST AI RMF: MEASURE (automated tests), MANAGE (CI/CD enforcement, remediation), MAP (describe prompt-level risks). GitHub+1
- Why: promptfoo provides automated prompt tests, integrates into CI (pre-deployment gating) and produces test artifacts for governance traceability. GitHub+1
3) AI-Infra-Guard (Tencent A.I.G)
- ISO 42001: 6 Planning (risk assessment), 7 Support (infrastructure), 8 Operation (secure deployment), 9 Performance evaluation (vulnerability scanning reports). Cloud Security Alliance+1
- NIST AI RMF: MAP (asset & infrastructure risk mapping), MEASURE (vulnerability detection, CVE checks), MANAGE (remediation workflows). NIST Publications+1
- Why: A.I.G scans AI infra, fingerprints components, and includes jailbreak evaluation — key for supply-chain and infra controls. GitHub
4) LlamaFirewall (runtime guardrail / agent monitor)
- ISO 42001: 8 Operation (runtime controls / enforcement), 7 Support (monitoring tooling), 9 Performance evaluation (runtime monitoring metrics). Cloud Security Alliance+1
- NIST AI RMF: MANAGE (runtime risk controls), MEASURE (monitoring & detection), MAP (runtime threat vectors). NIST Publications+1
- Why: LlamaFirewall is explicitly designed as a last-line runtime guardrail for agentic systems — enforcing policies and detecting task-drift/prompt injection at runtime. arXiv
5) LibVulnWatch (supply-chain & lib risk assessment)
- ISO 42001: 6 Planning (risk assessment), 7 Support (SBOMs, supplier controls), 8 Operation (secure build & deploy), 9 Performance evaluation (dependency health). Cloud Security Alliance+1
- NIST AI RMF: MAP (supply-chain mapping & dependency inventory), MEASURE (vulnerability & license metrics), MANAGE (mitigation/prioritization). NIST Publications+1
- Why: LibVulnWatch performs deep, evidence-backed evaluations of AI/ML libraries (CVEs, SBOM gaps, licensing) — directly supporting governance over the supply chain. arXiv+1
6) AutoRed / RainbowPlus (automated adversarial prompt generation & evolutionary red-teaming)
- ISO 42001: 8 Operation (adversarial testing), 9 Performance evaluation (benchmarks & stress tests), 10 Improvement (feed results back to controls). Cloud Security Alliance
- NIST AI RMF: MEASURE (adversarial performance metrics), MAP (expose attack surface), MANAGE (prioritize fixes based on attack impact). NIST Publications+2arXiv+2
- Why: These tools expand coverage of red-team tests (free-form and evolutionary adversarial prompts), surfacing edge failures and jailbreaks that standard tests miss. arXiv+1
7) Meta SecAlign (safer model / model-level defenses)
- ISO 42001: 8 Operation (safe model selection/deployment), 6 Planning (risk-aware model selection), 7 Support (model documentation). Cloud Security Alliance+1
- NIST AI RMF: MAP (model risk characteristics), MANAGE (apply safer model choices / mitigations), MEASURE (evaluate defensive effectiveness). NIST Publications+1
- Why: A “safer” model built to resist manipulation maps directly to operational and planning controls where the organization chooses lower-risk building blocks. arXiv
8) HarmBench (benchmarks for safety & robustness testing)
- ISO 42001: 9 Performance evaluation (standardized benchmarks), 8 Operation (validation against benchmarks), 10 Improvement (continuous improvement from results). Cloud Security Alliance
- NIST AI RMF: MEASURE (standardized metrics & benchmarks), MAP (compare risk exposure across models), MANAGE (feed measurement results into mitigation plans). NIST Publications
- Why: Benchmarks are the canonical way to measure and compare model trustworthiness and to demonstrate compliance in audits. arXiv
9) Collections / “awesome” lists (ecosystem & resource aggregation)
- ISO 42001: 5 Leadership & 7 Support (policy, competence, awareness — guidance & training resources). Cloud Security Alliance
- NIST AI RMF: GOVERN (policy & stakeholder guidance), MAP (inventory of recommended tools & practices). NIST Publications
- Why: Curated resources help leadership define policy, identify tools, and set organizational expectations — foundational for any AI management system. Cyberzoni.com
Quick recommendations for operationalizing the mapping
- Create a minimal mapping table inside your ISMS (ISO 42001) that records: tool name → ISO clause(s) it supports → NIST function(s) it maps to → artifact(s) produced (reports, SBOMs, test results). This yields audit-ready evidence. (ISO42001 + NIST suggestions above).
- Automate evidence collection: integrate promptfoo / Giskard into CI so that each deployment produces test artifacts (for ISO 42001 clause 9).
- Supply-chain checks: run LibVulnWatch and AI-Infra-Guard periodically to populate SBOMs and vulnerability dashboards (helpful for ISO 7 & 6).
- Runtime protections: embed LlamaFirewall or runtime monitors for agentic systems to satisfy operational guardrail requirements.
- Adversarial coverage: schedule periodic automated red-teaming using AutoRed / RainbowPlus / HarmBench to measure resilience and feed results into continual improvement (ISO clause 10).
Download 👇 AI Governance Tool Mapping
InfoSec services | ISMS Services | AIMS Services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | Security Risk Assessment Services | Mergers and Acquisition Security
- AI Agents and the New Cybersecurity Frontier: Understanding the 7 Major Attack Surfaces
- Understanding AI/LLM Application Attack Vectors and How to Defend Against Them
- AI Governance Assessment for ISO 42001 Readiness
- Beyond ChatGPT: The 9 Layers of AI Transforming Business from Analytics to Autonomous Agents
- CMMC Level 2 Third-Party Assessment: What It Is, Why It Matters, and What to Expect
At DISC InfoSec, our AI Governance services go beyond traditional security. We help organizations ensure legal compliance, privacy, fairness, ethics, proper documentation, and human oversight — addressing the full spectrum of responsible AI practices, many of which cannot be achieved through automated testing alone.





December 10th, 2025 12:45 pm
[…] Emerging Tools & Frameworks for AI Governance & Security Testing […]
December 15th, 2025 11:16 am
[…] Emerging Tools & Frameworks for AI Governance & Security Testing […]