In risk management, risk treatment process begins after completion of a comprehensive risk assessment.
Once risks have been assessed, risk manager utilize the following techniques to manage the risks
• Avoidance (eliminate)
• Reduction (mitigate)
• Transfer (outsource or insure)
• Retention (accept and budget)
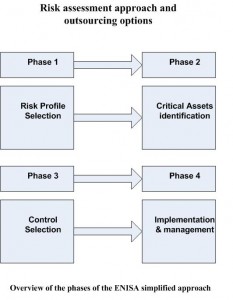
Now the question is how to select an appropriate control to avoid or reduce risk. While selecting appropriate control to mitigate and avoid risk we need to consider compensating control to cut cost and supplemental control to increase protection for sensitive or classified assets.
Compensating control is a safeguard or countermeasure is employed by an organization in lieu of recommended security control from standards such as ISO 27002 or NIST 800-53. Compensating control provides an equivalent or comparable protection for information system to the original control requirement form standard. For example, even though most standards recommend separation of duties, but for a small operation it might be an unacceptable cost to separate the duties of system administration and system auditing. In that case system owner can utilize compensating control such as strengthening the audit and personnel security.
On the other hand with supplemental control, the system owner may decide to supplement the control to achieve more protection for sensitive and classified assets. If there is high likelihood or magnitude of impact is high should a threat exploit a given vulnerability you might want to consider a supplemental control because overall risk is high. For example you might want to utilize defense in depth method to safeguard your crown jewel.
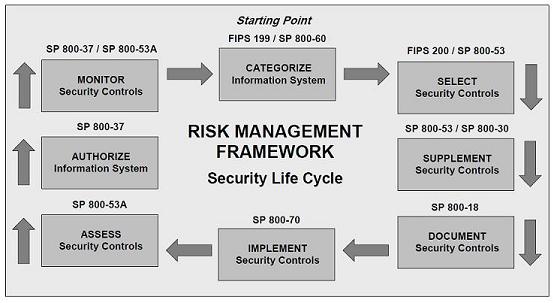
Implementing and monitoring security control can be expensive, system owner are pressured by management to look for cost savings without any reduction in the security posture of an organization. The system owner can either inherit the common controls or segment the system exposure to reduce cost and risks.
Common controls are the security controls which have been implemented by another information system that your system can utilize. Basically working with another system owner who has utilized some of the security controls need to be implemented in your system. For example utilize the corporate office base line hardening configuration for Windows and Unix system instead of developing your own. This will significantly reduce the cost of developing, testing and maintaining a secure baseline configuration.
Best and cheapest method of cost reduction is to segment the information system into multiple systems which will add different layers and levels of security into each system. Basically you put your crown jewel in multiple layers of security if one control breaks there is another control in place to monitor and protect your assets. This will allow the system owner to focus implementing higher security controls to the segment with most sensitive or classified information instead of entire system









![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=313b8a37-86b7-420d-b8eb-24979016eeac)
![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=8310531f-dd51-48b2-9dca-4a52b857f987)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=28dcae72-914e-4823-9632-cd34145194b7)

![Reblog this post [with Zemanta]](https://img.zemanta.com/reblog_e.png?x-id=f4c7607a-8a48-4ed1-bba2-9bb41450aa23)



