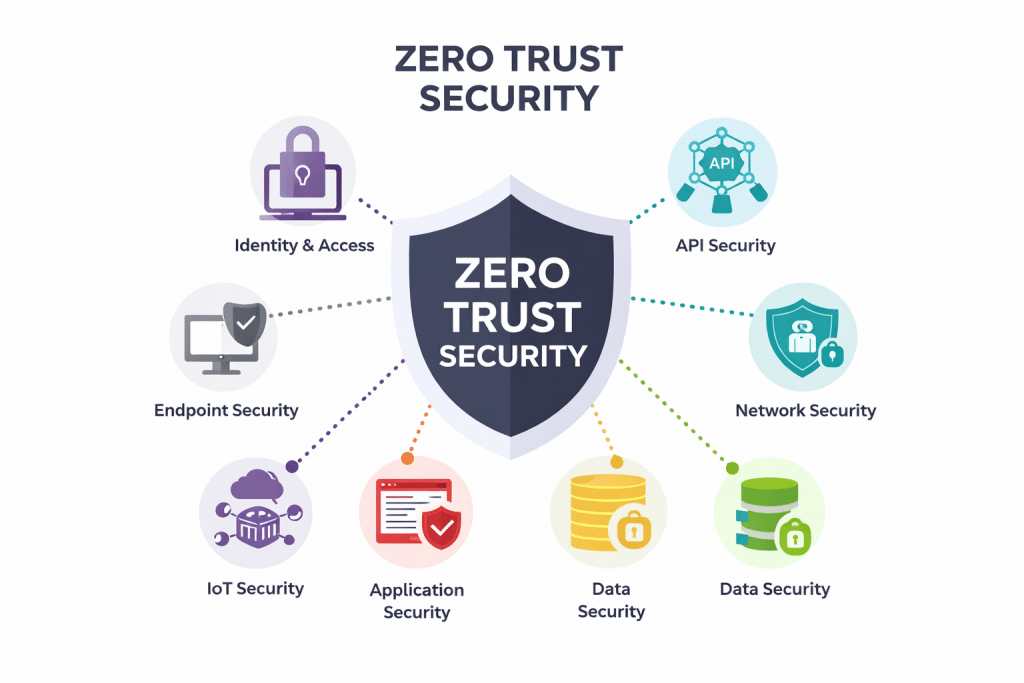
1. What is Zero Trust Security
Zero Trust Security is a security model that assumes no user, device, workload, application, or network is inherently trusted, whether inside or outside the traditional perimeter.
The core principles reflected in the image are:
- Never trust, always verify – every access request must be authenticated, authorized, and continuously evaluated.
- Least privilege access – users and systems only get the minimum access required.
- Assume breach – design controls as if attackers are already present.
- Continuous monitoring and enforcement – security decisions are dynamic, not one-time.
Instead of relying on perimeter defenses, Zero Trust distributes controls across endpoints, identities, APIs, networks, data, applications, and cloud environments—exactly the seven domains shown in the diagram.
2. The Seven Components of Zero Trust
1. Endpoint Security
Purpose: Ensure only trusted, compliant devices can access resources.
Key controls shown:
- Antivirus / Anti-Malware
- Endpoint Detection & Response (EDR)
- Patch Management
- Device Control
- Data Loss Prevention (DLP)
- Mobile Device Management (MDM)
- Encryption
- Threat Intelligence Integration
Zero Trust intent:
Access decisions depend on device posture, not just identity.
2. API Security
Purpose: Protect machine-to-machine and application integrations.
Key controls shown:
- Authentication & Authorization
- API Gateways
- Rate Limiting
- Encryption (at rest & in transit)
- Threat Detection & Monitoring
- Input Validation
- API Keys & Tokens
- Secure Development Practices
Zero Trust intent:
Every API call is explicitly authenticated, authorized, and inspected.
3. Network Security
Purpose: Eliminate implicit trust within networks.
Key controls shown:
- IDS / IPS
- Network Access Control (NAC)
- Network Segmentation / Micro-segmentation
- SSL / TLS
- VPN
- Firewalls
- Traffic Analysis & Anomaly Detection
Zero Trust intent:
The network is treated as hostile, even internally.
4. Data Security
Purpose: Protect data regardless of location.
Key controls shown:
- Encryption (at rest & in transit)
- Data Masking
- Data Loss Prevention (DLP)
- Access Controls
- Backup & Recovery
- Data Integrity Verification
- Tokenization
Zero Trust intent:
Security follows the data, not the infrastructure.
5. Cloud Security
Purpose: Enforce Zero Trust in shared-responsibility environments.
Key controls shown:
- Cloud Access Security Broker (CASB)
- Data Encryption
- Identity & Access Management (IAM)
- Security Posture Management
- Continuous Compliance Monitoring
- Cloud Identity Federation
- Cloud Security Audits
Zero Trust intent:
No cloud service is trusted by default—visibility and control are mandatory.
6. Application Security
Purpose: Prevent application-layer exploitation.
Key controls shown:
- Secure Code Review
- Web Application Firewall (WAF)
- API Security
- Runtime Application Self-Protection (RASP)
- Software Composition Analysis (SCA)
- Secure SDLC
- SAST / DAST
Zero Trust intent:
Applications must continuously prove they are secure and uncompromised.
7. IoT Security
Purpose: Secure non-traditional and unmanaged devices.
Key controls shown:
- Device Authentication
- Network Segmentation
- Secure Firmware Updates
- Encryption for IoT Data
- Anomaly Detection
- Vulnerability Management
- Device Lifecycle Management
- Secure Boot
Zero Trust intent:
IoT devices are high-risk by default and strictly controlled.
3. Mapping Zero Trust Controls to ISO/IEC 27001
Below is a practical mapping to ISO/IEC 27001:2022 (Annex A).
(Zero Trust is not a standard, but it maps very cleanly to ISO controls.)
Identity, Authentication & Access (Core Zero Trust)
Zero Trust domains: API, Cloud, Network, Application
ISO 27001 controls:
- A.5.15 – Access control
- A.5.16 – Identity management
- A.5.17 – Authentication information
- A.5.18 – Access rights
Endpoint & Device Security
Zero Trust domain: Endpoint, IoT
ISO 27001 controls:
- A.8.1 – User endpoint devices
- A.8.7 – Protection against malware
- A.8.8 – Management of technical vulnerabilities
- A.5.9 – Inventory of information and assets
Network Security & Segmentation
Zero Trust domain: Network
ISO 27001 controls:
- A.8.20 – Network security
- A.8.21 – Security of network services
- A.8.22 – Segregation of networks
- A.5.14 – Information transfer
Application & API Security
Zero Trust domain: Application, API
ISO 27001 controls:
- A.8.25 – Secure development lifecycle
- A.8.26 – Application security requirements
- A.8.27 – Secure system architecture
- A.8.28 – Secure coding
- A.8.29 – Security testing in development
Data Protection & Cryptography
Zero Trust domain: Data
ISO 27001 controls:
- A.8.10 – Information deletion
- A.8.11 – Data masking
- A.8.12 – Data leakage prevention
- A.8.13 – Backup
- A.8.24 – Use of cryptography
Monitoring, Detection & Response
Zero Trust domain: Endpoint, Network, Cloud
ISO 27001 controls:
- A.8.15 – Logging
- A.8.16 – Monitoring activities
- A.5.24 – Incident management planning
- A.5.25 – Assessment and decision on incidents
- A.5.26 – Response to information security incidents
Cloud & Third-Party Security
Zero Trust domain: Cloud
ISO 27001 controls:
- A.5.19 – Information security in supplier relationships
- A.5.20 – Addressing security in supplier agreements
- A.5.21 – ICT supply chain security
- A.5.22 – Monitoring supplier services
4. Key Takeaway (Executive Summary)
- Zero Trust is an architecture and mindset
- ISO 27001 is a management system and control framework
- Zero Trust implements ISO 27001 controls in a continuous, adaptive, and identity-centric way
In short:
ISO 27001 defines what controls you need.
Zero Trust defines how to enforce them effectively.
Zero Trust → ISO/IEC 27001 Crosswalk
| Zero Trust Domain | Primary Security Controls | Zero Trust Objective | ISO/IEC 27001:2022 Annex A Controls |
|---|---|---|---|
| Identity & Access (Core ZT Layer) | IAM, MFA, RBAC, API auth, token-based access, least privilege | Ensure every access request is explicitly verified | A.5.15 Access control A.5.16 Identity management A.5.17 Authentication information A.5.18 Access rights |
| Endpoint Security | EDR, AV, MDM, patching, device posture checks, disk encryption | Allow access only from trusted and compliant devices | A.8.1 User endpoint devices A.8.7 Protection against malware A.8.8 Technical vulnerability management A.5.9 Inventory of information and assets |
| Network Security | Micro-segmentation, NAC, IDS/IPS, TLS, VPN, firewalls | Remove implicit trust inside the network | A.8.20 Network security A.8.21 Security of network services A.8.22 Segregation of networks A.5.14 Information transfer |
| Application Security | Secure SDLC, SAST/DAST, WAF, RASP, dependency scanning | Prevent application-layer compromise | A.8.25 Secure development lifecycle A.8.26 Application security requirements A.8.27 Secure system architecture A.8.28 Secure coding A.8.29 Security testing |
| API Security | API gateways, rate limiting, input validation, encryption, monitoring | Secure machine-to-machine trust | A.5.15 Access control A.8.20 Network security A.8.26 Application security requirements A.8.29 Security testing |
| Data Security | Encryption, DLP, tokenization, masking, access controls, backups | Protect data regardless of location | A.8.10 Information deletion A.8.11 Data masking A.8.12 Data leakage prevention A.8.13 Backup A.8.24 Use of cryptography |
| Cloud Security | CASB, cloud IAM, posture management, identity federation, audits | Enforce Zero Trust in shared-responsibility models | A.5.19 Supplier relationships A.5.20 Supplier agreements A.5.21 ICT supply chain security A.5.22 Monitoring supplier services |
| IoT / Non-Traditional Assets | Device authentication, segmentation, secure boot, firmware updates | Control high-risk unmanaged devices | A.5.9 Asset inventory A.8.1 User endpoint devices A.8.8 Technical vulnerability management |
| Monitoring & Incident Response | Logging, SIEM, anomaly detection, SOAR | Assume breach and respond rapidly | A.8.15 Logging A.8.16 Monitoring activities A.5.24 Incident management planning A.5.25 Incident assessment A.5.26 Incident response |

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- Expanding Risk, Shrinking Authority: The Modern CISO Dilemma
- Stop Debating Frameworks. Start Implementing Safeguards
- The 14 Vulnerability Domains That Make or Break Your Application Security
- Why Cryptographic Agility Is Now a Leadership Imperative
- Global Privacy Regulators Draw a Hard Line on AI-Generated Imagery