Blockchain 101: Understanding the Basics Through a Visual
Think of cryptocurrency as a new kind of digital money that exists only on the internet and doesn’t rely on banks or governments to run it.
A good way to understand it is by starting with the most famous example: Bitcoin.
What is cryptocurrency?
Cryptocurrency is digital money secured by cryptography (advanced math used to protect information). Instead of a bank keeping track of who owns what, transactions are recorded on a public digital ledger called a blockchain.
You can imagine blockchain as a shared Google Sheet that thousands of computers around the world constantly verify and update. No single company controls it.
Key features:
- 💻 Digital only – no physical coins or bills
- 🌍 Decentralized – not controlled by one government or bank
- 🔒 Secure – protected by cryptography
- 📜 Transparent – transactions are recorded publicly
How does cryptocurrency work?
Most cryptocurrencies run on a blockchain network.
Here’s a simplified flow:
- You create a wallet
A crypto wallet is like a digital bank account. It has:- a public address (like your email you can share)
- a private key (like your password — keep it secret)
- You send a transaction
When you send crypto, your wallet signs the transaction with your private key. - The network verifies it
Thousands of computers (called nodes or miners/validators) check that:- you actually own the funds
- you aren’t spending the same money twice
- The transaction is added to the blockchain
Once verified, it’s grouped with others into a “block” and permanently recorded.
After that, the transaction can’t easily be changed.
Benefits of cryptocurrency
1. Faster global payments
You can send money anywhere in the world in minutes, often cheaper than banks.
2. No middleman required
You don’t need a bank or payment company to approve transactions.
3. Financial access
Anyone with internet access can use crypto — helpful in places with weak banking systems.
4. Transparency and security
Transactions are public and hard to tamper with.
5. Programmable money
Some cryptocurrencies (like Ethereum) allow smart contracts — programs that automatically execute agreements.
Example: A simple crypto transaction
Let’s walk through a real-world style example.
Scenario:
Alice wants to send $20 worth of Bitcoin to Bob for helping with a project.
Step-by-step:
- Alice opens her wallet app and enters Bob’s public address.
- She types in the amount and presses Send.
- Her wallet signs the transaction with her private key.
- The Bitcoin network checks that Alice has enough funds.
- The transaction is added to the blockchain.
- Bob sees the payment appear in his wallet.
Time: ~10 minutes (depending on network traffic)
No bank involved.
It’s similar to handing someone cash — but done digitally and verified by a global network.
Simple analogy
Think of cryptocurrency like:
Email for money
Before email, sending letters took days and required postal systems.
Crypto lets you send money across the internet as easily as sending an email.
Important things to know (balanced view)
While crypto has benefits, it also has challenges:
- ⚠️ Prices can be very volatile
- 🔐 If you lose your private key, you may lose your funds
- 🧾 Regulations are still evolving
- 🧠 It has a learning curve
let’s walk through the diagram step by step in plain language, like you would in a classroom.
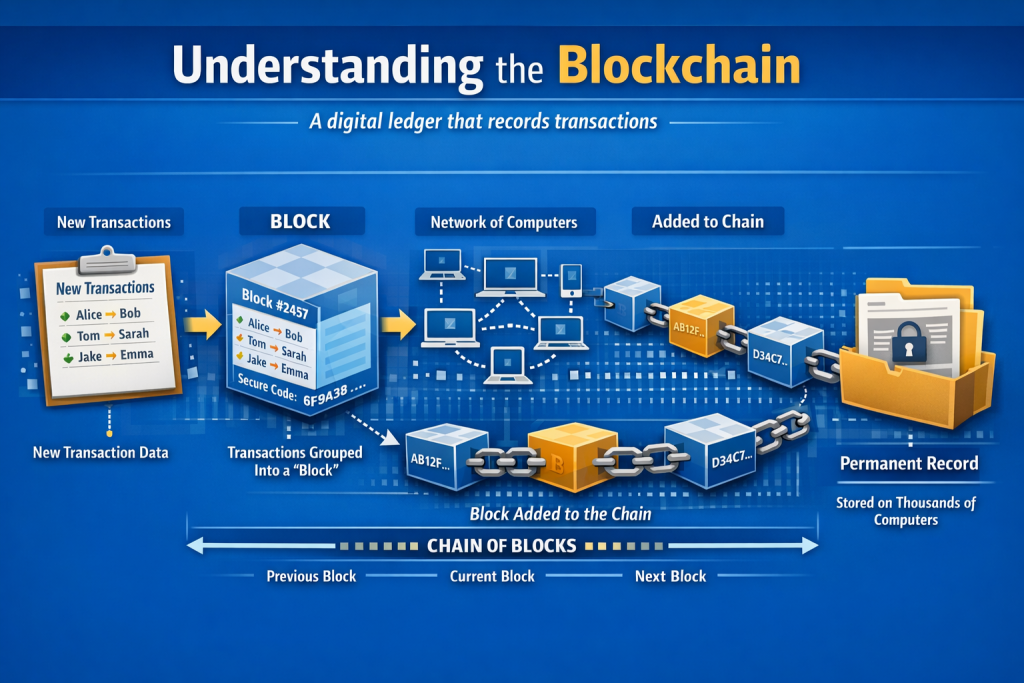
This diagram is showing how a blockchain records a transaction (like sending money using Bitcoin).
Step 1: New transactions are created
On the left side, you see a list of new transactions (for example: Alice sends money to Bob).
Think of this as:
👉 People requesting to send digital money to each other.
At this stage, the transactions are waiting to be verified.
Step 2: Transactions are grouped into a block
In the next section, those transactions are packed into a block.
A block is like a container or page in a notebook that stores:
- A list of transactions
- A timestamp (when it happened)
- A unique security code (called a hash)
This security code links the block to the previous block — like a chain link.
Step 3: The network of computers verifies the block
In the middle of the diagram, you see many connected computers.
These computers form a global network that checks:
- Are the transactions valid?
- Does the sender actually have the funds?
- Is anyone trying to cheat?
If most computers agree the transactions are valid, the block is approved.
Think of it like a group of students checking each other’s math homework to make sure it’s correct.
Step 4: The block is added to the chain
Once approved, the block is attached to previous blocks, forming a chain of blocks — this is the blockchain.
Each new block connects to the one before it using cryptographic links.
This makes it very hard to change past records, because you would have to change every block after it.
Step 5: Permanent record stored everywhere
On the far right, the diagram shows a secure folder.
This represents the permanent record:
- The transaction is now finalized
- It’s copied and stored across thousands of computers
- It cannot easily be altered
This is what makes blockchain secure and transparent.
Big picture summary
The diagram shows this simple flow:
👉 Transaction → Block → Verification → Chain → Permanent record
In other words:
Someone sends crypto → it gets verified by many computers → it becomes a permanent part of a shared digital ledger.
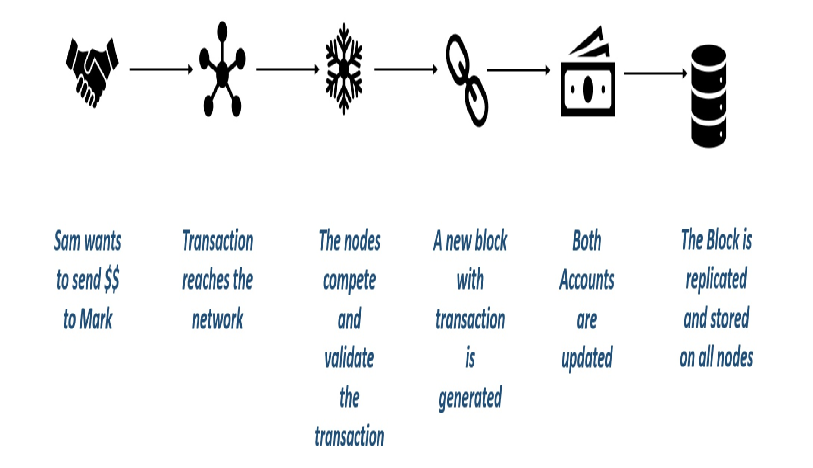
Here is another digital transaction exmple: in this example Sam want to send digital asset ($$) to Mark

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- AI in Cybersecurity: Building Proactive and Adaptive Digital Defense
- AI Exposure Readiness assessment: A Practical Framework for Identifying and Managing Emerging Risks
- Top 10 AI Governance Best Practices: A Practical Guide to Responsible AI
- From Chaos to Control: Building a Practical GRC Framework for Modern Organizations
- NIST CSF and ISO 27001: Reducing Security Chaos Through Layered Frameworks