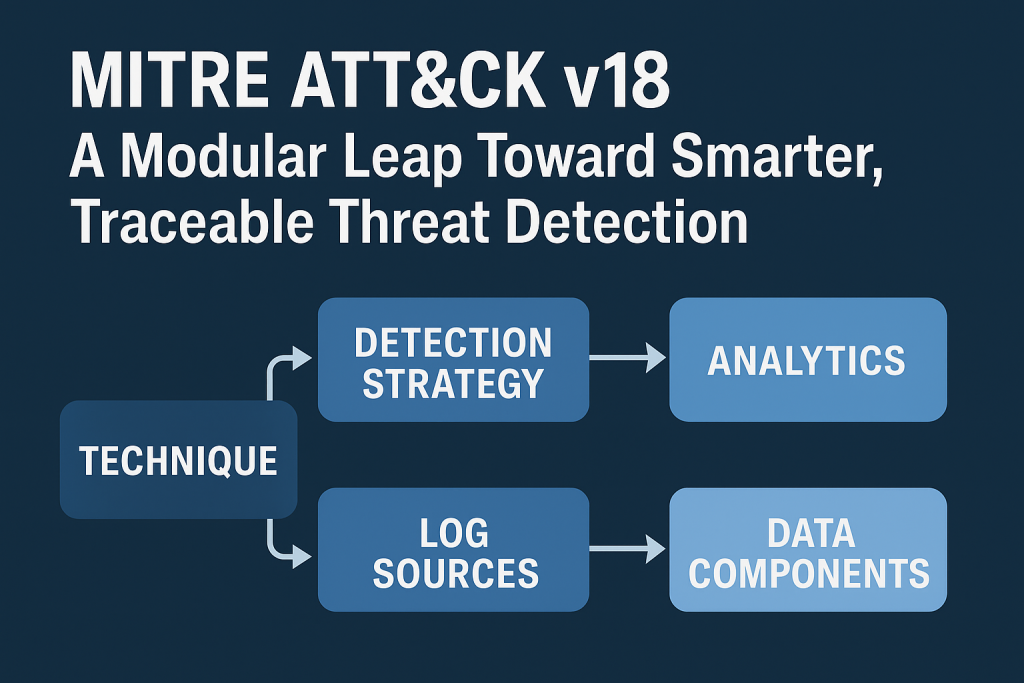
MITRE has released version 18 of the ATT&CK framework, introducing two significant enhancements: Detection Strategies and Analytics. These updates replace the older detection fields and redefine how detection logic connects with real-world telemetry and data.
In this new structure, each ATT&CK technique now maps to a Detection Strategy, which then connects to platform-specific Analytics. These analytics link directly to the relevant Log Sources and Data Components, forming a streamlined path from attacker behavior to observable evidence.
This new model delivers a clearer, more practical view for defenders. It enables organizations to understand exactly how an attacker’s activity translates into detectable signals across their systems.
Each Detection Strategy functions as a conceptual blueprint rather than a specific detection rule. It outlines the general behavior to monitor, the essential data sources to collect, and the configurable parameters for tailoring the detection.
The strategies also highlight which aspects of detection are fixed, based on the nature of the ATT&CK technique itself, versus which elements can be adapted to fit specific platforms or environments.
MITRE’s intention is to make detections more modular, transparent, and actionable. By separating the strategy from the platform-specific logic, defenders can reuse and adapt detections across diverse technologies without losing consistency.
As Amy L. Robertson from MITRE explained, this modular approach simplifies the detection lifecycle. Detection Strategies describe the attacker’s behavior, Analytics guide defenders on implementing detection for particular platforms, and standardized Log Source naming ensures clarity about what telemetry to collect.
The update also enhances collaboration across teams, enabling security analysts, engineers, and threat hunters to communicate more effectively using a shared framework and precise terminology.
Ultimately, this evolution moves MITRE ATT&CK closer to being not just a threat taxonomy but a detection engineering ecosystem, bridging the gap between theory and operational defense.
Opinion:
MITRE ATT&CK v18 represents a major step forward in operationalizing threat intelligence. The modular breakdown of detection logic provides defenders with a much-needed structure to build scalable, reusable, and auditable detections. It aligns well with modern SOC workflows and detection engineering practices. By emphasizing traceability from behavior to telemetry, MITRE continues to make threat-informed defense both practical and measurable — a commendable advancement for the cybersecurity community.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
Latest Posts:
- AI in Cybersecurity: Building Proactive and Adaptive Digital Defense
- AI Exposure Readiness assessment: A Practical Framework for Identifying and Managing Emerging Risks
- Top 10 AI Governance Best Practices: A Practical Guide to Responsible AI
- From Chaos to Control: Building a Practical GRC Framework for Modern Organizations
- NIST CSF and ISO 27001: Reducing Security Chaos Through Layered Frameworks





November 10th, 2025 9:56 am
[…] MITRE ATT&CK v18: A Modular Leap Toward Smarter, Traceable Threat Detection […]