📘 What Is the OWASP Smart Contract Top 10?
The OWASP Smart Contract Top 10 is an industry-standard awareness and guidance document for Web3 developers and security teams detailing the most critical classes of vulnerabilities in smart contracts. It’s based on real attacks and expert analysis and serves as both a checklist for secure design and an audit reference to help reduce risk before deployment.
🔍 The 2026 Smart Contract Top 10 (Rephrased & Explained)
SC01 – Access Control Vulnerabilities
What it is: Happens when a contract fails to restrict who can call sensitive functions (like minting, admin changes, pausing, or upgrades).
Why it matters: Without proper permission checks, attackers can take over critical actions, change ownership, steal funds, or manipulate state.
Mitigation: Use well-tested access control libraries (e.g., Ownable, RBAC), apply permissions modifiers, and ensure admin/initialization functions are restricted to trusted roles.
👉 Ensures only authorized actors can invoke critical logic.
SC02 – Business Logic Vulnerabilities
What it is: Flaws in how contract logic is designed, not just coded (e.g., incorrect accounting, faulty rewards, broken lending logic).
Why it matters: Even if code is syntactically correct, logic errors can be exploited to drain funds or warp protocol economics.
Mitigation: Thoroughly define intended behavior, write comprehensive tests, and undergo peer reviews and professional audits.
👉 Helps verify that the contract does what it should, not just compiles.
SC03 – Price Oracle Manipulation
What it is: Contracts often rely on external price feeds (“oracles”). If those feeds can be tampered with or spoofed, protocol logic behaves incorrectly.
Why it matters: Manipulated price data can trigger unfair liquidations, bad trades, or exploit chains that profit the attacker.
Mitigation: Use decentralized or robust oracle networks with slippage limits, price aggregation, and sanity checks.
👉 Prevents external data from being a weak link in internal calculations.
SC04 – Flash Loan–Facilitated Attacks
What it is: Flash loans let attackers borrow large amounts with no collateral within one transaction and manipulate a protocol.
Why it matters: Small vulnerabilities in pricing or logic can be leveraged with borrowed capital to cause big economic damage.
Mitigation: Include checks that prevent manipulations during a single transaction (e.g., TWAP pricing, re-pricing guards, invariants).
👉 Stops attackers from using borrowed capital as an offensive weapon.
SC05 – Lack of Input Validation
What it is: A contract accepts values (addresses, amounts, parameters) without checking they are valid or within expected ranges.
Why it matters: Bad input can lead to malformed state, unexpected behavior, or exploitable conditions.
Mitigation: Validate and sanitize all inputs — reject zero addresses, negative amounts, out-of-range values, and unexpected data shapes.
👉 Reduces the risk of attackers “feeding” bad data into sensitive functions.
SC06 – Unchecked External Calls
What it is: The contract calls external code but doesn’t check if those calls succeed or how they influence its state.
Why it matters: A failing external call can leave a contract in an inconsistent state and expose it to exploits.
Mitigation: Always check return values or use Solidity patterns that handle call failures explicitly (e.g., require).
👉 Ensures your logic doesn’t blindly trust other contracts or addresses.
SC07 – Arithmetic Errors (Rounding & Precision)
What it is: Mistakes in math operations — rounding, scaling, and precision errors — especially around decimals or shares.
Why it matters: In DeFi, small arithmetic mistakes can be exploited repeatedly or magnified with flash loans.
Mitigation: Use safe math libraries and clearly define how rounding/truncation should work. Consider fixed-point libraries with clear precision rules.
👉 Avoids subtle calculation bugs that can siphon value over time.
SC08 – Reentrancy Attacks
What it is: A contract calls an external contract before updating its own state. A malicious callee re-enters and manipulates state repeatedly.
Why it matters: This classic attack can drain funds, corrupt internal accounting, or turn single actions into repeated ones.
Mitigation: Update state before external calls, use reentrancy guards, and follow established secure patterns.
👉 Prevents an external party from interrupting your logic in a harmful order.
SC09 – Integer Overflow and Underflow
What it is: Arithmetic exceeds the maximum or minimum representable integer value, causing wrap-around behavior.
Why it matters: Attackers can exploit wrapped values to inflate balances or break invariants.
Mitigation: Use Solidity’s built-in checked arithmetic (since 0.8.x) or libraries that revert on overflow/underflow.
👉 Stops attackers from exploiting unexpected number behavior.
SC10 – Proxy & Upgradeability Vulnerabilities
What it is: Misconfigured upgrade mechanisms or proxy patterns let attackers take over contract logic or state.
Why it matters: Many modern protocols support upgrades; an insecure path can allow malicious re-deployments, unauthorized initialization, or bypass of intended permissions.
Mitigation: Secure admin keys, guard initializer functions, and use time-locked governance for upgrades.
👉 Ensures upgrade patterns do not become new attack surfaces.
💡 How the Top 10 Helps Build Better Smart Contracts
- Security baseline: Provides a structured checklist for teams to review and assess risk throughout development and before deployment.
- Risk prioritization: Highlights the most exploited or impactful vulnerabilities seen in real attacks, not just academic theory.
- Design guidance: Encourages developers to bake security into requirements, design, testing, and deployment — not just fix bugs reactively.
- Audit support: Auditors and reviewers can use the Top 10 as a framework to validate coverage and threat modeling.
🧠 Feedback Summary
The OWASP Smart Contract Top 10 is valuable because it combines empirical data and expert consensus to pinpoint where real smart contract breaches occur. It moves beyond generic lists to specific classes tailored for blockchain platforms. As a result:
- It helps developers avoid repeat mistakes made by others.
- It provides practical remediations rather than abstract guidance.
- It supports continuous improvement in smart contract practices as the threat landscape evolves.
Using this list early in design (not just before audits) can elevate security hygiene and reduce costly exploits.
Below are practical Solidity defense patterns and code snippets mapped to each item in the OWASP Smart Contract Top 10 (2026). These are simplified examples meant to illustrate secure design patterns, not production-ready contracts.
SC01 — Access Control Vulnerabilities
Defense pattern: Role-based access control + modifiers
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.20;
contract AccessControlled {
address public owner;
modifier onlyOwner() {
require(msg.sender == owner, "Not authorized");
_;
}
constructor() {
owner = msg.sender;
}
function updateOwner(address newOwner) external onlyOwner {
require(newOwner != address(0), "Invalid address");
owner = newOwner;
}
}
Key idea: Always gate sensitive functions with explicit permission checks.
SC02 — Business Logic Vulnerabilities
Defense pattern: Invariant checks + sanity validation
contract Vault {
mapping(address => uint256) public balances;
uint256 public totalDeposits;
function deposit() external payable {
balances[msg.sender] += msg.value;
totalDeposits += msg.value;
// Invariant check
assert(address(this).balance == totalDeposits);
}
}
Key idea: Encode assumptions as invariants and assertions to catch logic flaws.
SC03 — Price Oracle Manipulation
Defense pattern: Use time-weighted average price (TWAP) checks
interface IOracle {
function getTWAP() external view returns (uint256);
}
contract PriceConsumer {
IOracle public oracle;
uint256 public maxDeviation = 5; // %
function validatePrice(uint256 marketPrice) public view returns (bool) {
uint256 oraclePrice = oracle.getTWAP();
uint256 diff = (oraclePrice * maxDeviation) / 100;
return (
marketPrice >= oraclePrice - diff &&
marketPrice <= oraclePrice + diff
);
}
}
Key idea: Don’t trust a single spot price; add bounds and sanity checks.
SC04 — Flash Loan–Facilitated Attacks
Defense pattern: Transaction-level guardrails
contract FlashLoanGuard {
uint256 public lastActionBlock;
modifier noSameBlock() {
require(block.number > lastActionBlock, "Flash attack blocked");
_;
lastActionBlock = block.number;
}
function sensitiveOperation() external noSameBlock {
// critical logic
}
}
Key idea: Prevent atomic manipulation by adding timing/state constraints.
SC05 — Lack of Input Validation
Defense pattern: Strict parameter validation
function transfer(address to, uint256 amount) external {
require(to != address(0), "Zero address");
require(amount > 0, "Invalid amount");
require(balances[msg.sender] >= amount, "Insufficient balance");
balances[msg.sender] -= amount;
balances[to] += amount;
}
Key idea: Validate all external inputs before state changes.
SC06 — Unchecked External Calls
Defense pattern: Check call results explicitly
function safeCall(address target, bytes calldata data) external {
(bool success, bytes memory result) = target.call(data);
require(success, "External call failed");
// Optionally decode and validate result
}
Key idea: Never ignore return values from external calls.
SC07 — Arithmetic Errors (Precision/Rounding)
Defense pattern: Fixed-point math discipline
uint256 constant PRECISION = 1e18;
function calculateShare(uint256 amount, uint256 ratio)
public
pure
returns (uint256)
{
return (amount * ratio) / PRECISION;
}
Key idea: Use consistent scaling factors to control rounding behavior.
SC08 — Reentrancy Attacks
Defense pattern: Checks-Effects-Interactions + guard
contract ReentrancySafe {
mapping(address => uint256) public balances;
bool private locked;
modifier nonReentrant() {
require(!locked, "Reentrant call");
locked = true;
_;
locked = false;
}
function withdraw(uint256 amount) external nonReentrant {
require(balances[msg.sender] >= amount);
// Effects first
balances[msg.sender] -= amount;
// Interaction last
payable(msg.sender).transfer(amount);
}
}
Key idea: Update internal state before external calls.
SC09 — Integer Overflow & Underflow
Defense pattern: Use Solidity ≥0.8 checked math
function safeAdd(uint256 a, uint256 b)
public
pure
returns (uint256)
{
return a + b; // auto-reverts on overflow in Solidity 0.8+
}
Key idea: Rely on compiler protections and avoid unchecked unless justified.
SC10 — Proxy & Upgradeability Vulnerabilities
Defense pattern: Secure initializer + upgrade restriction
contract Upgradeable {
address public admin;
bool private initialized;
modifier onlyAdmin() {
require(msg.sender == admin, "Not admin");
_;
}
function initialize(address _admin) external {
require(!initialized, "Already initialized");
require(_admin != address(0));
admin = _admin;
initialized = true;
}
function upgrade(address newImpl) external onlyAdmin {
require(newImpl != address(0));
// upgrade logic
}
}
Key idea: Prevent re-initialization and tightly control upgrade authority.
Practical Takeaway
These patterns collectively enforce a secure smart contract lifecycle:
- Restrict authority (who can act)
- Validate assumptions (what is allowed)
- Protect math and logic (how it behaves)
- Guard external interactions (who you trust)
- Secure upgrades (how it evolves)
They translate abstract vulnerability categories into repeatable engineering habits.
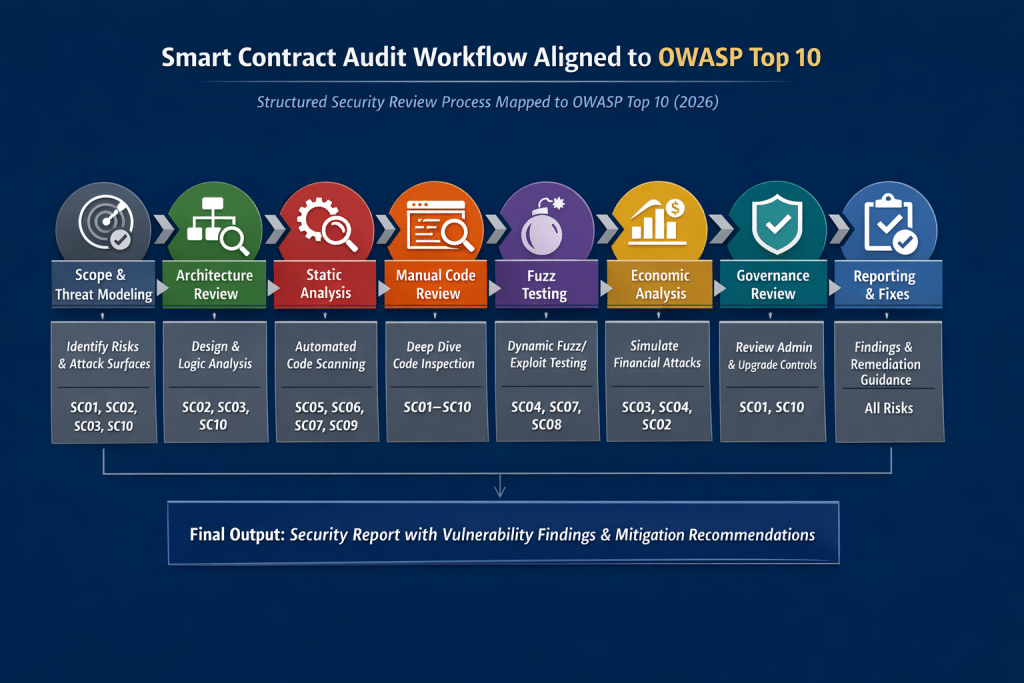
Here’s a practical mapping of the OWASP Smart Contract Top 10 (2026) to a real-world smart contract audit workflow — structured the way professional auditors actually run engagements.
I’ll show:
👉 Audit phase → What auditors do → Which Top 10 risks are checked → Tools & techniques
Smart Contract Audit Workflow Mapped to OWASP Top 10
1. Scope Definition & Threat Modeling
Goal: Understand architecture, trust boundaries, and attack surface before touching code.
What auditors do
- Review protocol architecture diagrams
- Identify privileged roles and external dependencies
- Map trust assumptions (oracles, bridges, governance)
- Define attacker models
Top 10 focus
- SC01 — Access Control
- SC02 — Business Logic
- SC03 — Oracle Risks
- SC10 — Upgradeability
Key audit questions
- Who controls admin keys?
- What happens if an privileged actor is compromised?
- Can economic incentives be abused?
Output
- Threat model document
- Attack surface map
- Risk prioritization matrix
2. Architecture & Design Review
Goal: Validate that the protocol design itself is secure.
This happens before deep code inspection.
What auditors do
- Review system invariants
- Analyze economic assumptions
- Evaluate upgrade mechanisms
- Review oracle integration design
Top 10 focus
- SC02 — Business Logic
- SC03 — Oracle Manipulation
- SC04 — Flash Loan Attacks
- SC10 — Proxy/Upgradeability
Techniques
- Economic modeling
- Scenario walkthroughs
- Failure mode analysis
Output
- Design weaknesses list
- Architecture recommendations
3. Automated Static Analysis
Goal: Catch common coding mistakes quickly.
What auditors do
Run automated scanners to detect:
- Reentrancy risks
- Arithmetic errors
- Unchecked calls
- Input validation issues
Top 10 focus
- SC05 — Input Validation
- SC06 — Unchecked External Calls
- SC07 — Arithmetic Errors
- SC08 — Reentrancy
- SC09 — Overflow/Underflow
Common tools
- Slither
- Mythril
- Foundry fuzzing
- Echidna
Output
- Machine-generated vulnerability list
- False-positive triage
4. Manual Code Review (Deep Dive)
Goal: Find subtle vulnerabilities automation misses.
This is the core of a professional audit.
What auditors do
Line-by-line review of:
- Permission checks
- State transitions
- External call patterns
- Edge cases
Top 10 focus
👉 All categories, especially:
- SC01 — Access Control
- SC02 — Business Logic
- SC08 — Reentrancy
- SC10 — Upgradeability
Techniques
- Adversarial reasoning
- Attack simulation
- Logic tracing
Output
- Detailed vulnerability report
- Severity classification
5. Dynamic Testing & Fuzzing
Goal: Stress test the contract under adversarial conditions.
What auditors do
- Fuzz inputs
- Simulate flash loan attacks
- Test extreme edge cases
- Validate invariants
Top 10 focus
- SC04 — Flash Loan Attacks
- SC07 — Arithmetic Errors
- SC08 — Reentrancy
- SC02 — Business Logic
Output
- Exploit reproducibility evidence
- Proof-of-concept attack cases
6. Economic Attack Simulation
Goal: Evaluate real-world exploitability.
This is crucial for DeFi protocols.
What auditors do
- Simulate price manipulation
- Test liquidity attacks
- Analyze arbitrage vectors
Top 10 focus
- SC03 — Oracle Manipulation
- SC04 — Flash Loan Attacks
- SC02 — Business Logic
Output
- Attack scenarios
- Economic impact assessment
7. Upgrade & Governance Security Review
Goal: Prevent takeover or governance abuse.
What auditors do
- Inspect proxy patterns
- Review admin privileges
- Evaluate governance safeguards
Top 10 focus
- SC01 — Access Control
- SC10 — Upgradeability
Output
- Governance risk assessment
- Key management recommendations
8. Reporting & Remediation Guidance
Goal: Deliver actionable fixes.
What auditors provide
- Severity-ranked findings
- Code patch recommendations
- Secure design patterns
- Retest verification
Top 10 coverage
Each finding is mapped to a Top 10 category to ensure full coverage.
How This Workflow Improves Smart Contract Security
Mapping audits to the OWASP Top 10 creates:
✅ Structured coverage
No major risk category gets overlooked.
✅ Repeatable methodology
Teams can standardize audit practices.
✅ Measasurable security maturity
Organizations can track improvements over time.
✅ Faster remediation
Developers understand root causes, not just symptoms.
Practical Audit Checklist (Condensed)
Here’s a field-ready checklist auditors often use:
- Access roles verified and minimized
- Business logic invariants documented
- Oracle dependencies stress-tested
- Flash loan attack scenarios simulated
- Input validation enforced everywhere
- External calls checked and guarded
- Arithmetic precision validated
- Reentrancy protections implemented
- Overflow protections confirmed
- Upgrade paths locked down

InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- AI in Cybersecurity: From Intelligent Threat Detection to Adaptive Defense
- Below the Waterline: Why AI Strategy Fails Without Data Foundations
- From Ethics to Enforcement: The AI Governance Shift No One Can Ignore
- ISO 42001 Training and Awareness: Turning AI Governance from Policy into Practice
- The ISO Trifecta: Integrating Security, Privacy, and AI Governance








