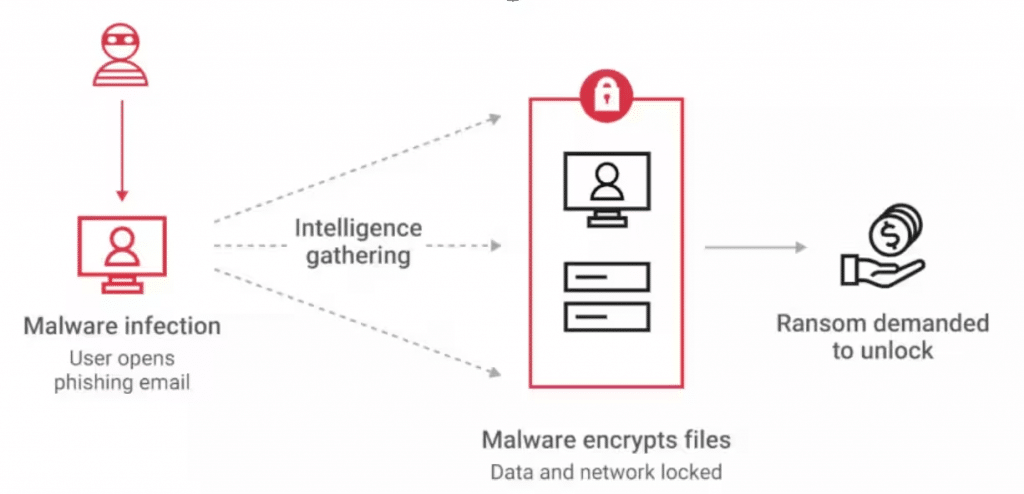
What Is a Ransomware Attack?
A ransomware attack is a type of cyberattack where attackers encrypt an organization’s files or systems and demand payment—usually in cryptocurrency—to restore access. Once infected, critical data becomes unusable, operations can grind to a halt, and organizations are forced into high-pressure decisions with financial, legal, and reputational consequences.
Why People Are Falling for Ransomware Attacks
Ransomware works because it exploits human behavior as much as technical gaps. Attackers craft emails, messages, and websites that look legitimate and urgent, tricking users into clicking links or opening attachments. Weak passwords, reused credentials, unpatched systems, and lack of awareness training make it easy for attackers to gain initial access. As attacks become more polished and automated, even cautious users and small businesses fall victim.
Why It’s a Major Threat Today
Ransomware attacks are increasing rapidly, especially against organizations with limited security resources. Small mistakes—such as clicking a malicious link—can completely shut down business operations, making ransomware a serious operational and financial risk.
Who Gets Targeted the Most
Small and mid-sized businesses are frequent targets because they often lack mature security controls. Hospitals, schools, startups, and freelancers are also heavily targeted due to sensitive data and limited downtime tolerance.
How Ransomware Enters Systems
Attackers commonly use fake emails, malicious attachments, phishing links, weak or reused passwords, and outdated software to gain access. These methods are effective because they blend in with normal business activity.
Warning Signs of a Ransomware Attack
Early indicators include files that won’t open, unusual file extensions, sudden ransom notes appearing on screens, and systems becoming noticeably slow or unstable.
The Cost of One Attack
A single ransomware incident can result in direct financial losses, extended business downtime, loss of critical data, and long-term reputational damage that impacts customer trust.
Why People Fall for It
Attackers design messages that look authentic and urgent. They use fear, pressure, and trusted branding to push users into acting quickly without verifying authenticity.
Biggest Mistakes Organizations Make
Common errors include clicking links without verification, failing to maintain regular backups, ignoring software updates, reusing the same password everywhere, and downloading pirated or cracked software.
How to Prevent Ransomware
Basic prevention includes using strong and unique passwords, enabling multi-factor authentication, keeping systems updated, and training employees to recognize phishing attempts.
What to Do If You’re Attacked
If ransomware strikes, immediately disconnect affected systems from the internet, notify IT or security teams, avoid paying the ransom, restore systems from clean backups, and act quickly to limit damage.
Myths About Ransomware
Many believe attackers won’t target them, antivirus alone is sufficient, or only large companies are at risk. In reality, ransomware affects organizations of all sizes, and layered defenses are essential.
How to Protect Your Business from Cyber Attacks
Employee Cybersecurity Education
Educating employees on phishing, password hygiene, and reporting suspicious activity is one of the most cost-effective security controls. Well-trained staff significantly reduce the likelihood of successful attacks.
Use an Internet Security Suite
A comprehensive security suite—including antivirus, firewall, and intrusion detection—helps protect systems from known threats. Keeping these tools updated is critical for effectiveness.
Prepare for Zero-Day Attacks
Organizations should assume unknown threats will occur. Security solutions should focus on containment and behavior-based detection rather than relying solely on known signatures.
Stay Updated with Patches
Regularly applying software and system updates closes known vulnerabilities. Unpatched systems remain one of the easiest entry points for attackers.
Back Up Your Data
Frequent, secure backups ensure business continuity. Backups should be stored separately from primary systems to prevent them from being encrypted during an attack.
Be Cautious with Public Wi-Fi
Public and unsecured Wi-Fi networks expose systems to interception and attacks. Employees should avoid unknown networks or use secure VPNs when remote.
Use Secure Web Browsers
Modern secure browsers reduce exposure to malicious websites and exploits. Choosing hardened, updated browsers adds another layer of defense.
Secure Personal Devices Used for Work
Personal devices accessing business data must meet organizational security standards. Unsecured endpoints can undermine even strong network defenses.
Establish Access Controls
Each employee should have a unique account with access limited to what they need. Enforcing least privilege reduces the impact of compromised credentials.
Ensure Systems Are Malware-Free
Regular system scans help detect hidden malware that may evade initial defenses. Early detection prevents long-term data theft and damage.
How to Protect Small and Mid-Sized Businesses (SMBs) from Cyber Attacks
For SMBs, cybersecurity must be practical, risk-based, and repeatable. Start with strong identity controls such as multi-factor authentication and unique passwords. Maintain regular, tested backups and keep systems patched. Limit access based on roles, monitor for unusual activity, and educate employees continuously. Most importantly, SMBs should adopt a simple incident response plan and consider periodic risk assessments aligned with frameworks like ISO 27001 or NIST CSF. Cybersecurity for SMBs isn’t about expensive tools—it’s about visibility, discipline, and readiness.
How Attacks Get In
- 📧 Phishing Emails
- 🔑 Weak / Reused Passwords
- 🧩 Unpatched Systems
- 👤 Excessive User Access
- 💾 No Reliable Backups
ISO 27001 controls
- 🔐 MFA & Identity Control
(A.5.17) - 🎓 Security Awareness
(A.6.3) - 🛡️ Malware Protection
(A.8.7) - 🔄 Patch Management
(A.8.8) - 🧭 Least Privilege Access
(A.5.15 / A.5.18) - 💽 Backups & Recovery
(A.8.13) - 🚨 Incident Response
(A.5.24–26)
What the Business Feels
- ⏱️ Operational Downtime
- 💰 Financial Loss
- 📉 Reputation Damage
- ⚖️ Compliance Exposure
- 👔 Executive Accountability
Ransomware is not a technology failure — it’s a governance failure.
Subtext (smaller):
vCISO oversight aligns ISO 27001 controls to real business risk.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | AIMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
At DISC InfoSec, we help organizations navigate this landscape by aligning AI risk management, governance, security, and compliance into a single, practical roadmap. Whether you are experimenting with AI or deploying it at scale, we help you choose and operationalize the right frameworks to reduce risk and build trust. Learn more at DISC InfoSec.
- From Prediction to Autonomy: Mapping AI Risk to ISO 42001, NIST AI RMF, and the EU AI Act
- The Hidden Battle: Defending AI/ML APIs from Prompt Injection and Data Poisoning
- Burp Pro Can Help With with Smart Contract
- 10 Global Risks Every ISO 27001 Risk Register Should Cover
- Why a Cyberattack Didn’t Kill iRobot—But Exposed Why It Failed




