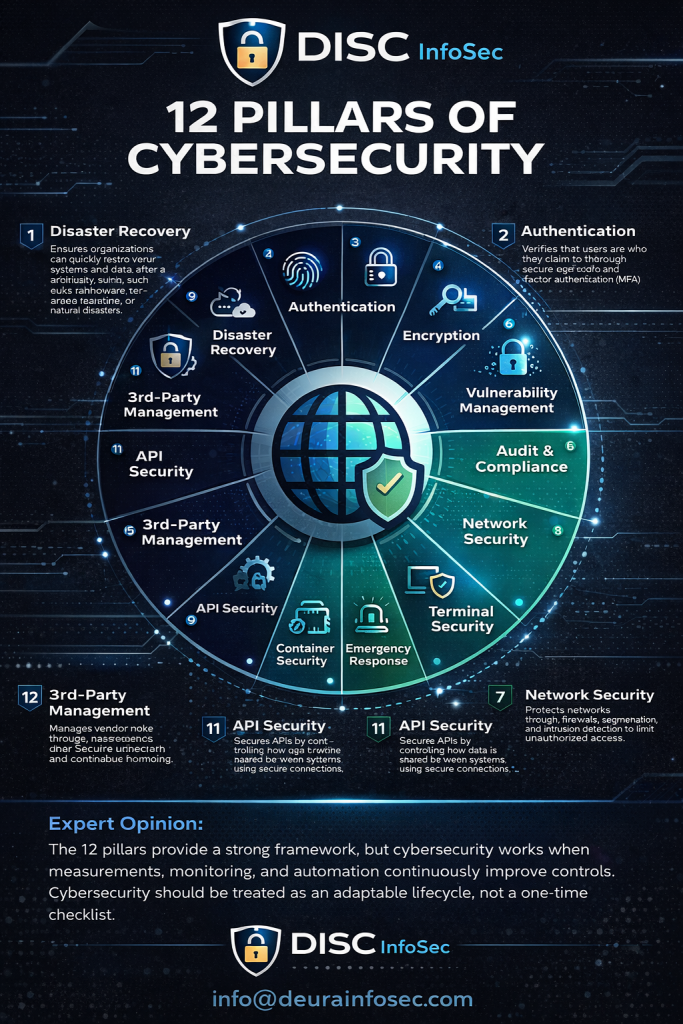
12 Pillars of Cybersecurity — Simplified Overview — Start by getting the basics right — it’s the foundation of every effective security program.
1️⃣ Disaster Recovery
Disaster Recovery ensures organizations can quickly restore systems and data after a disruptive event such as ransomware, hardware failure, or natural disasters. A well-designed plan includes data backups, documented recovery procedures, and resilience testing so the business can continue operating with minimal downtime.
2️⃣ Authentication
Authentication verifies that users are who they claim to be. Strong password policies, secure login controls, and multifactor authentication (MFA) help prevent unauthorized access to critical systems, reducing the risk of credential theft and account compromise.
3️⃣ Authorization
Authorization determines what authenticated users are allowed to do. Properly managed access roles and least-privilege principles ensure individuals only access the information needed for their job, minimizing internal misuse and breach exposure.
4️⃣ Encryption
Encryption protects sensitive data by making it unreadable to unauthorized entities. Whether data is stored or in transit, encryption standards like TLS help maintain confidentiality and integrity, even if attackers intercept it.
5️⃣ Vulnerability Management
This includes identifying weaknesses in applications, systems, or configurations before attackers exploit them. Regular scanning, patching, and proactive remediation are essential to stay ahead of constantly emerging threats.
6️⃣ Audit & Compliance
Audit and compliance confirm that cybersecurity controls meet legal, industry, and internal requirements. Through continuous monitoring, reporting, and assessments, organizations strengthen governance and reduce regulatory risk.
7️⃣ Network Security
Network security protects communication flowing between devices and systems. Firewalls, intrusion detection, segmentation, and DNS security reduce unauthorized access and lateral movement inside the network.
8️⃣ Terminal (Endpoint) Security
Endpoints—like laptops, servers, and mobile devices—must be protected from malware and misuse. Tools such as EDR (Endpoint Detection & Response), encryption, and device control help secure data where employees work every day.
9️⃣ Emergency Response
Incident Response and business continuity actions are triggered when a cyberattack occurs. Quick detection, containment, and communication limit damage and accelerate recovery while maintaining stakeholder trust.
🔟 Container Security
Containerized workloads, used heavily in cloud environments, require specialized protections. Securing container images, runtime behavior, and orchestration platforms prevents vulnerabilities from spreading rapidly across applications.
1️⃣1️⃣ API Security
APIs are now core to digital integrations, making them a prime target for attackers. Secure authentication, encryption, rate limiting, and runtime monitoring protect data shared between systems and prevent unauthorized access.
1️⃣2️⃣ Third-Party / Vendor Management
Vendors introduce additional risk since their systems may connect to yours. Risk assessments, clear security expectations, and continuous monitoring help ensure third-party access doesn’t become the weakest link.
⭐ Expert Opinion
These 12 pillars offer a strong foundational framework — but cybersecurity only works when measurements, monitoring, and automation continuously improve these controls. With attackers advancing faster every year, organizations must treat cybersecurity as an adaptable lifecycle, not a one-time checklist. Prioritized risk-based implementation and skilled oversight remain the keys to real cyber resilience.
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security
- How AI Is Reshaping the Future of Cyber Risk Governance
- Risk Registers vs. GRC Charters: What Comes First?
- Stop Confusing LLMs, RAG, and AI Agents — Here’s the Real Difference
- From Security Leader to Business Enabler: The Modern CISO Role
- AI in Cybersecurity: Building Proactive and Adaptive Digital Defense




